Saturday 29 October 2011
Batch Image Processing Using GIMP
I've previously enlisted few tools regarding batch image resizing in windows. However they are limited to windows only and I was searching for something which was cross-platform. With some search, I found that GIMP loaded with David's Batch Processor would let us resize the images easily.
DBP (David's Batch Processor) is a simple batch processing plugin for the Gimp - it allows the user to automatically perform operations (such as resize) on a collection of image files. Its main advantage is that the user does not have to learn a scripting language. Like the Gimp itself, DBP relies on a graphical interface. The user creates a list of images, and sets up the processing required for each image. The results of the current settings can be displayed. Once the required sequence of operations has been set up, DBP performs the same processing on each image in turn. The images can be colour corrected, resized, cropped, and sharpened, then renamed and saved to a different file in a specified image format.
Check official website for more information on installation and downloads.
Read more...
DBP (David's Batch Processor) is a simple batch processing plugin for the Gimp - it allows the user to automatically perform operations (such as resize) on a collection of image files. Its main advantage is that the user does not have to learn a scripting language. Like the Gimp itself, DBP relies on a graphical interface. The user creates a list of images, and sets up the processing required for each image. The results of the current settings can be displayed. Once the required sequence of operations has been set up, DBP performs the same processing on each image in turn. The images can be colour corrected, resized, cropped, and sharpened, then renamed and saved to a different file in a specified image format.
Check official website for more information on installation and downloads.
Read more...
Batch Image Processing Using GIMP
2011-10-29T14:44:00+05:45
Cool Samar
bulk image resizing|gimp|graphics|software|
Comments
Labels:
bulk image resizing,
gimp,
graphics,
software
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Bulk Image Resizing Tools For Windows
You will most likely find a situation when you need to resize multiple images at once. One example is while uploading pictures taken from high megapixel digital cameras. I had the same situation and googled to find few useful softwares for windows which I am going to list here.
1) Picture Resizer: An easy-to-use and free standalone tool for batch resizing of JPG pictures and photos. The tool is using high-quality resizing method, where color of each pixel is a weighted average of all covered pixels from the original image. Linear interpolation is used when zooming in. The algorithm is optimized to work with gamma-corrected pictures.
2) Fotosizer: Fotosizer is a free batch photo/image resizer tool. It lets you resize hundreds of photos in a matter of minutes in a quick and easy way. With Fotosizer, you can shrink JPEG image files, along with other supported formats, and dramatically reduce internet transfer times, enabling you to quickly and easily prepare your image collections to be published on the web.
3) Imagisizer: Imagisizer is absolutely the easiest, straight forward, image resizer and
converter around. It supports major image formats such jpg, png, gif and bmp. You need .NET framework for this tool to work which is bundled along with most moder Windows OS I guess.
4) PhotoResizer: Simple tiny sized batch resizing tools supporting multiple formats in input but only jpeg as output.
I hope some of these tools count useful for you as well like they did to me.
Read more...
1) Picture Resizer: An easy-to-use and free standalone tool for batch resizing of JPG pictures and photos. The tool is using high-quality resizing method, where color of each pixel is a weighted average of all covered pixels from the original image. Linear interpolation is used when zooming in. The algorithm is optimized to work with gamma-corrected pictures.
2) Fotosizer: Fotosizer is a free batch photo/image resizer tool. It lets you resize hundreds of photos in a matter of minutes in a quick and easy way. With Fotosizer, you can shrink JPEG image files, along with other supported formats, and dramatically reduce internet transfer times, enabling you to quickly and easily prepare your image collections to be published on the web.
3) Imagisizer: Imagisizer is absolutely the easiest, straight forward, image resizer and
converter around. It supports major image formats such jpg, png, gif and bmp. You need .NET framework for this tool to work which is bundled along with most moder Windows OS I guess.
4) PhotoResizer: Simple tiny sized batch resizing tools supporting multiple formats in input but only jpeg as output.
I hope some of these tools count useful for you as well like they did to me.
Read more...
Bulk Image Resizing Tools For Windows
2011-10-29T14:30:00+05:45
Cool Samar
bulk image resizing|graphics|software|windows|
Comments
Labels:
bulk image resizing,
graphics,
software,
windows
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Friday 28 October 2011
How To View System Information In Windows
You can easily view the information about your system using a simple command in windows. The systeminfo command lets the administrator query for basic system configuration information.
The command produces significant amount of information that might be useful for system troubleshooting and other purposes.
Open the command prompt by typing "cmd" or "command.com" in Run option.
To find information regarding your system, type systeminfo in the prompt. In few seconds the command will produce the output about basic system configuration. Example output is shown below:
Since the output command produces large lines of output, it is better to save the output to the text file and later analyze the text file. The redirection operator can simplify this task. The command below would save in the filename specified:
The output will be saved in the specified filename. Also, the information can be saved in different formats which can be specified as below:
Other values /FO takes are TABLE and LIST.
I hope this helps you. :)
Read more...
The command produces significant amount of information that might be useful for system troubleshooting and other purposes.
Open the command prompt by typing "cmd" or "command.com" in Run option.
To find information regarding your system, type systeminfo in the prompt. In few seconds the command will produce the output about basic system configuration. Example output is shown below:
Host Name: COMPUTER-1164
OS Name: Microsoft Windows XP Professional
OS Version: 5.1.2600 Service Pack 3 Build 2600
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Workstation
OS Build Type: Multiprocessor Free
Registered Owner: Bugs Bunny
Registered Organization: Warner Brothers Movie World
Product ID: 76487-640-1457236-23040
Original Install Date: 26/10/2011, 22:24:31
System Up Time: 0 Days, 1 Hours, 16 Minutes, 12 Seconds
System Manufacturer: ECS
System Model: G31T-M7
System type: X86-based PC
Processor(s): 1 Processor(s) Installed.
[01]: x86 Family 15 Model 4 Stepping 1 GenuineIntel ~2793 Mhz
BIOS Version: 073108 - 20080731
Windows Directory: C:\WINDOWS
System Directory: C:\WINDOWS\system32
Boot Device: \Device\HarddiskVolume2
System Locale: en-us;English (United States)
Input Locale: en-us;English (United States)
Time Zone: (GMT+05:45) Kathmandu
Total Physical Memory: 2,038 MB
Available Physical Memory: 1,367 MB
Virtual Memory: Max Size: 2,048 MB
Virtual Memory: Available: 1,995 MB
Virtual Memory: In Use: 53 MB
Page File Location(s): C:\pagefile.sys
Domain: WORKGROUP
Logon Server: \\COMPUTER-1164
Hotfix(s): 342 Hotfix(s) Installed.
[01]: File 1
[02]: File 1
[03]: File 1
[04]: File 1
**Snipped To Save Spaces**
NetWork Card(s): 1 NIC(s) Installed.
[01]: Atheros L2 Fast Ethernet 10/100 Base-T Controller
Connection Name: Local Area Connection
DHCP Enabled: Yes
DHCP Server: 192.168.1.1
IP address(es)
[01]: 192.168.1.2
OS Name: Microsoft Windows XP Professional
OS Version: 5.1.2600 Service Pack 3 Build 2600
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Workstation
OS Build Type: Multiprocessor Free
Registered Owner: Bugs Bunny
Registered Organization: Warner Brothers Movie World
Product ID: 76487-640-1457236-23040
Original Install Date: 26/10/2011, 22:24:31
System Up Time: 0 Days, 1 Hours, 16 Minutes, 12 Seconds
System Manufacturer: ECS
System Model: G31T-M7
System type: X86-based PC
Processor(s): 1 Processor(s) Installed.
[01]: x86 Family 15 Model 4 Stepping 1 GenuineIntel ~2793 Mhz
BIOS Version: 073108 - 20080731
Windows Directory: C:\WINDOWS
System Directory: C:\WINDOWS\system32
Boot Device: \Device\HarddiskVolume2
System Locale: en-us;English (United States)
Input Locale: en-us;English (United States)
Time Zone: (GMT+05:45) Kathmandu
Total Physical Memory: 2,038 MB
Available Physical Memory: 1,367 MB
Virtual Memory: Max Size: 2,048 MB
Virtual Memory: Available: 1,995 MB
Virtual Memory: In Use: 53 MB
Page File Location(s): C:\pagefile.sys
Domain: WORKGROUP
Logon Server: \\COMPUTER-1164
Hotfix(s): 342 Hotfix(s) Installed.
[01]: File 1
[02]: File 1
[03]: File 1
[04]: File 1
**Snipped To Save Spaces**
NetWork Card(s): 1 NIC(s) Installed.
[01]: Atheros L2 Fast Ethernet 10/100 Base-T Controller
Connection Name: Local Area Connection
DHCP Enabled: Yes
DHCP Server: 192.168.1.1
IP address(es)
[01]: 192.168.1.2
Since the output command produces large lines of output, it is better to save the output to the text file and later analyze the text file. The redirection operator can simplify this task. The command below would save in the filename specified:
systeminfo > filename.txt
The output will be saved in the specified filename. Also, the information can be saved in different formats which can be specified as below:
systeminfo /FO CSV > filename.txt
Other values /FO takes are TABLE and LIST.
I hope this helps you. :)
Read more...
How To View System Information In Windows
2011-10-28T15:58:00+05:45
Cool Samar
command prompt|windows|
Comments
Labels:
command prompt,
windows
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Wednesday 26 October 2011
Create Fake Facebook Walls
While browsing internet, I came across this site called TheWallMachine.com which offered to create fake and funny facebook walls. I found it funny so googled for such services and am sharing two such websites here.
The Wall Machine
My Fake Wall
Samples:
Franklin D Roosebelt
Osama Bin Laden's Last Status Update
Just for fun.
Read more...
The Wall Machine
My Fake Wall
Samples:
Franklin D Roosebelt
Osama Bin Laden's Last Status Update
Just for fun.
Read more...
Create Fake Facebook Walls
2011-10-26T22:37:00+05:45
Cool Samar
facebook|useful website|
Comments
Labels:
facebook,
useful website
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Lists of Various Steganographic Tools
Steganography is the art and science of hiding information such that only the sender and recipient can read that hidden piece of information. While the cryptography is focussed on making message unreadable, steganography focusses on data hiding and hence combination of both can give better security in most cases.
As mentioned earlier, steganography is the art of hiding information and can be done in many ways. For instance, simplest forms of steganography would be toinsert each character of hidden message in the Nth position of each word in a sentence so that recipient takes Nth letters of each words to reconstruct the message. While this was very basic example, steganography has no bounds and one can hide messages within images, audios, videos, source codes, etc and this involves some sort of creation to increase the obscurity of the hidden message. Wikipedia entry gives far much deeper information on steganography tool and I would like to recommend you to read it.
To make digital steganography easier, numerous tools have been developed and I'm listing some of them here.
1) Hide in Picture: Hide In Picture is a program that allows you to conceal files inside bitmap pictures, using a password. The pictures look like normal images, so people will not suspect there is hidden data in them.
2) wbStego: wbStego4 offers steganography in bitmaps, text files, HTML files and PDF files. It is has two very user-friendly interfaces and is ideal for securely transmitting data online or adding copyright information, especially with the copyright information manager.
3) Hide4PGP: Hide4PGP is a freeware program distributed as source code in ANSI C and precompiled executables for DOS (any version but 1.x), OS/2 (Warp and up), and the Win32 console (9x and NT). It's purpose is to hide any data in a way that the viewer or listener does not recognize any difference. It supports BMP, WAV and VOC file formats.
4) MP3Stego: Hide files within mp3 files. MP3Stego will hide information in MP3 files during the compression process. The data is first compressed, encrypted and then hidden in the MP3 bit stream.
5) TextHide: Simple text steganography
6) GifShuffle: gifshuffle is used to conceal messages in GIF images by shuffling the colourmap, which leaves the image visibly unchanged. gifshuffle works with all GIF images, including those with transparency and animation, and in addition provides compression and encryption of the concealed message.
7) Snow: snow is used to conceal messages in ASCII text by appending whitespace to the end of lines. Because spaces and tabs are generally not visible in text viewers, the message is effectively hidden from casual observers. And if the built-in encryption is used, the message cannot be read even if it is detected.
8) Camouflage: Camouflage allows you to hide files by scrambling them and then attaching them to the file of your choice. This camouflaged file then looks and behaves like a normal file, and can be stored, used or emailed without attracting attention.
9) OpenPuff: OpenPuff is a professional steganography tool, with unique features you won't find among any other free or commercial software. OpenPuff is 100% free and suitable for highly sensitive data covert transmission. Its very advanced tool with support to images, audios, videos, flash, adobe.
10) SteganRTP: Steganography tool which establishes a full-duplex steganographic data transfer protocol utilizing Real-time Transfer Protocol (RTP) packet payloads as the cover medium. The tool provides interactive chat, file transfer, and remote shell access. A network steganographic tool.
Read more...
As mentioned earlier, steganography is the art of hiding information and can be done in many ways. For instance, simplest forms of steganography would be toinsert each character of hidden message in the Nth position of each word in a sentence so that recipient takes Nth letters of each words to reconstruct the message. While this was very basic example, steganography has no bounds and one can hide messages within images, audios, videos, source codes, etc and this involves some sort of creation to increase the obscurity of the hidden message. Wikipedia entry gives far much deeper information on steganography tool and I would like to recommend you to read it.
To make digital steganography easier, numerous tools have been developed and I'm listing some of them here.
1) Hide in Picture: Hide In Picture is a program that allows you to conceal files inside bitmap pictures, using a password. The pictures look like normal images, so people will not suspect there is hidden data in them.
2) wbStego: wbStego4 offers steganography in bitmaps, text files, HTML files and PDF files. It is has two very user-friendly interfaces and is ideal for securely transmitting data online or adding copyright information, especially with the copyright information manager.
3) Hide4PGP: Hide4PGP is a freeware program distributed as source code in ANSI C and precompiled executables for DOS (any version but 1.x), OS/2 (Warp and up), and the Win32 console (9x and NT). It's purpose is to hide any data in a way that the viewer or listener does not recognize any difference. It supports BMP, WAV and VOC file formats.
4) MP3Stego: Hide files within mp3 files. MP3Stego will hide information in MP3 files during the compression process. The data is first compressed, encrypted and then hidden in the MP3 bit stream.
5) TextHide: Simple text steganography
6) GifShuffle: gifshuffle is used to conceal messages in GIF images by shuffling the colourmap, which leaves the image visibly unchanged. gifshuffle works with all GIF images, including those with transparency and animation, and in addition provides compression and encryption of the concealed message.
7) Snow: snow is used to conceal messages in ASCII text by appending whitespace to the end of lines. Because spaces and tabs are generally not visible in text viewers, the message is effectively hidden from casual observers. And if the built-in encryption is used, the message cannot be read even if it is detected.
8) Camouflage: Camouflage allows you to hide files by scrambling them and then attaching them to the file of your choice. This camouflaged file then looks and behaves like a normal file, and can be stored, used or emailed without attracting attention.
9) OpenPuff: OpenPuff is a professional steganography tool, with unique features you won't find among any other free or commercial software. OpenPuff is 100% free and suitable for highly sensitive data covert transmission. Its very advanced tool with support to images, audios, videos, flash, adobe.
10) SteganRTP: Steganography tool which establishes a full-duplex steganographic data transfer protocol utilizing Real-time Transfer Protocol (RTP) packet payloads as the cover medium. The tool provides interactive chat, file transfer, and remote shell access. A network steganographic tool.
Read more...
Lists of Various Steganographic Tools
2011-10-26T17:38:00+05:45
Cool Samar
security|software|steganography|
Comments
Labels:
security,
software,
steganography
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Useful and Basic Commands and Shortcuts For Ubuntu Beginners
One of my friends asked me to list useful commands and shortcuts for him to use in his ubuntu distro. I listed some pretty useful ones and am also sharing them over here.
Basic Commands
Alt + F1: Opens application menu.
Alt + F2: Opens run command(something similar to run command in windows)
Ctrl +Alt + FN: Switch to TTYN terminals
Ctrl +Alt + F7: Switch to X Display
mkdir <dir_name>: Create a directory
cd $HOME: Set the current path as your home directory
cd /: Set the current path as root filesystem
Privileged commands: Note that most of these commands require you to have sudoers privilege which is specified in /etc/sudoers file.
sudo su: Run the shell as root user.
sudo su user: Run the shell as the user specified
sudo command: Run the specified command with root privilege
gksudo command: Run the specified command as graphical root mode.(used for graphical programs)
passwd: Change your password
Basic Network Commands
ifconfig: Displays information about network. Also, ifconfig interface would give information about the specified interface.
iwconfig: Displays information about wireless network
ping host_or_IP: Pings to check if the specified host or IP is online or not. Also useful for knowing if you are connected to some other network eg. internet.
host ip_addr: Displays hostname for specified IP address by querying nameservers specified in /etc/resolv.conf
ifup interface: Bring the specified network up.
ifdown interface: Bring the specified network down.
ssh user@hostname -p PORTNO: Establish SSh connection to specified host and port number and login as specified user.
Commands For Package Management: These commands require root privilege so either escalate privilege to root by sudo su command or precede each commands with sudo.
apt-get install package1 package2 .. packageN: Download and install the package(s) specified.
apt-get install -d package: Just download the packages(no installation)
apt-get update: Update packages information.
apt-get dist-upgrade: Perform distro version upgrade.
do-release-upgrade: Perform distro version upgrade.
apt-get remove package: Remove the specified package(s).
apt-get -f install: Fix packages problem.
dpkg --configure -a: Fix broken packages.
Other/Misc. Commands
id: Displays user and group IDs for current user.
uname -a: Displays all kernel information
gedit: Open text editor
nautilus: Open nautilus file manager
gksudo nautilus: Open root nautilus file manager
lsb_release -a: Get information about installed ubuntu version
These are some of the commands that has come in my mind as of now. I might update this list when some other commands come into my mind. By the way, TAB is very useful in terminal as it allows auto-completion and suggestion of commands and files in ubuntu. What this means is if you type do- and then press TAB, it will auto complete the command to do-release-upgrade thus saving some important time. Also be sure to share the useful commands in the comment section below.
Read more...
Basic Commands
Alt + F1: Opens application menu.
Alt + F2: Opens run command(something similar to run command in windows)
Ctrl +Alt + FN: Switch to TTYN terminals
Ctrl +Alt + F7: Switch to X Display
mkdir <dir_name>: Create a directory
cd $HOME: Set the current path as your home directory
cd /: Set the current path as root filesystem
Privileged commands: Note that most of these commands require you to have sudoers privilege which is specified in /etc/sudoers file.
sudo su: Run the shell as root user.
sudo su user: Run the shell as the user specified
sudo command: Run the specified command with root privilege
gksudo command: Run the specified command as graphical root mode.(used for graphical programs)
passwd: Change your password
Basic Network Commands
ifconfig: Displays information about network. Also, ifconfig interface would give information about the specified interface.
iwconfig: Displays information about wireless network
ping host_or_IP: Pings to check if the specified host or IP is online or not. Also useful for knowing if you are connected to some other network eg. internet.
host ip_addr: Displays hostname for specified IP address by querying nameservers specified in /etc/resolv.conf
ifup interface: Bring the specified network up.
ifdown interface: Bring the specified network down.
ssh user@hostname -p PORTNO: Establish SSh connection to specified host and port number and login as specified user.
Commands For Package Management: These commands require root privilege so either escalate privilege to root by sudo su command or precede each commands with sudo.
apt-get install package1 package2 .. packageN: Download and install the package(s) specified.
apt-get install -d package: Just download the packages(no installation)
apt-get update: Update packages information.
apt-get dist-upgrade: Perform distro version upgrade.
do-release-upgrade: Perform distro version upgrade.
apt-get remove package: Remove the specified package(s).
apt-get -f install: Fix packages problem.
dpkg --configure -a: Fix broken packages.
Other/Misc. Commands
id: Displays user and group IDs for current user.
uname -a: Displays all kernel information
gedit: Open text editor
nautilus: Open nautilus file manager
gksudo nautilus: Open root nautilus file manager
lsb_release -a: Get information about installed ubuntu version
These are some of the commands that has come in my mind as of now. I might update this list when some other commands come into my mind. By the way, TAB is very useful in terminal as it allows auto-completion and suggestion of commands and files in ubuntu. What this means is if you type do- and then press TAB, it will auto complete the command to do-release-upgrade thus saving some important time. Also be sure to share the useful commands in the comment section below.
Read more...
Useful and Basic Commands and Shortcuts For Ubuntu Beginners
2011-10-26T16:07:00+05:45
Cool Samar
beginner|linux|tricks and tips|ubuntu|
Comments
Labels:
beginner,
linux,
tricks and tips,
ubuntu
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Mass Youtube Videos Download Using BYTubeD under Firefox
Before going for vacation, I wanted to download some youtube videos and I wanted to download them in bulk but I had no idea. Tried searching firefox addons site and found an addon known as BYTubeD that allows me to perform bulk downloads from youtube.
BYTubeD is a Bulk YouTube video Downloader. It can be used to download all/selected YouTube videos on any page which has some links to YouTube videos, by clicking the BYTubeD menu item in the Tools menu or in the context menu (i.e. right click menu).
Get BYTubeD in Firefox.
Read more...
BYTubeD is a Bulk YouTube video Downloader. It can be used to download all/selected YouTube videos on any page which has some links to YouTube videos, by clicking the BYTubeD menu item in the Tools menu or in the context menu (i.e. right click menu).
Get BYTubeD in Firefox.
Read more...
Mass Youtube Videos Download Using BYTubeD under Firefox
2011-10-26T11:50:00+05:45
Cool Samar
browser addons|mozilla firefox|software|tricks and tips|
Comments
Labels:
browser addons,
mozilla firefox,
software,
tricks and tips
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Bleeding Life 2 Released By Blackhat Academy
Bleeding Life 2 is a browser exploit pack that affects the web browsers on the Microsoft Windows operating system with remote code execution and buffer overflows. The tool can be used to launch client side browser exploits to the vulnerable users.
The wiki page of Bleeding Life enlists the exploits and features of this tool.
For download, click HERE.
Read more...
The wiki page of Bleeding Life enlists the exploits and features of this tool.
For download, click HERE.
Read more...
Bleeding Life 2 Released By Blackhat Academy
2011-10-26T11:15:00+05:45
Cool Samar
browser|hack tool|hacking|windows|
Comments
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Extract and Download Multiple Attachments At Once
I was searching for a way to extract and download multiple attachments at once and came across a thunderbird plugin that allows you to do this.
Just select the messages containing the attachments you want to extract and select 'Extract Attachments' and this extension does the rest. No more having to go through each message to extract the attachments!
Check out the settings dialog for the different options.
For downloads and further information, check addon's page.
Read more...
Just select the messages containing the attachments you want to extract and select 'Extract Attachments' and this extension does the rest. No more having to go through each message to extract the attachments!
Check out the settings dialog for the different options.
For downloads and further information, check addon's page.
Read more...
Extract and Download Multiple Attachments At Once
2011-10-26T11:08:00+05:45
Cool Samar
bulk extraction|email|tricks and tips|
Comments
Labels:
bulk extraction,
email,
tricks and tips
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
SSL DOS Tool From The Hacker's Choice
On october 24, the german hackers group The Hacker's Choice released a new Denial of Service(DOS) tool that exploits the weakness in the SSL implementation to take the servers down.
THC-SSL-DOS is a tool to verify the performance of SSL.
The Hacker's Choice says:
Establishing a secure SSL connection requires 15x more processing
power on the server than on the client.
THC-SSL-DOS exploits this asymmetric property by overloading the
server and knocking it off the Internet.
This problem affects all SSL implementations today.
For more information and downloads, visit THC SSL DOS Page.
Read more...
THC-SSL-DOS is a tool to verify the performance of SSL.
The Hacker's Choice says:
Establishing a secure SSL connection requires 15x more processing
power on the server than on the client.
THC-SSL-DOS exploits this asymmetric property by overloading the
server and knocking it off the Internet.
This problem affects all SSL implementations today.
For more information and downloads, visit THC SSL DOS Page.
Read more...
SSL DOS Tool From The Hacker's Choice
2011-10-26T10:50:00+05:45
Cool Samar
hack tool|hacking|ssl|the hacker's choice|
Comments
Labels:
hack tool,
hacking,
ssl,
the hacker's choice
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Tuesday 25 October 2011
Stay connected to social networks with Yoono
Yoono is an easy to use application that brings all major social networking sites under a single application. The best thing about Yoono is that it is available for all major platforms and operating systems.
It is available as Desktop app for windows, linux and MAC and also the portable version of the application is available. Moreover, it is available as Browser addon for Firefox and Google Chrome. And both the paid and free(with ads) versions of this app are available for iPhones. So the users can choose any version of Yoono according to their convinience and preferences.
Some of the features of Yoono are:
- Stay connected with major social networking sites Twitter, Facebook, Foursquare, LinkedIn, YouTube, Flickr, GoogleBuzz, Yammer, Friendfeed, MySpace and more...all in one place.
- Update your status and share links, images and video from the page you're viewing across all your networks simultaneously.
- Easily sync the status and update your status across all the sites at once.
The software is available for downloads at yoono.com.
Firefox users can download the addon from HERE as well.
Google chrome users can download the addon from HERE as well.
Read more...
It is available as Desktop app for windows, linux and MAC and also the portable version of the application is available. Moreover, it is available as Browser addon for Firefox and Google Chrome. And both the paid and free(with ads) versions of this app are available for iPhones. So the users can choose any version of Yoono according to their convinience and preferences.
Some of the features of Yoono are:
- Stay connected with major social networking sites Twitter, Facebook, Foursquare, LinkedIn, YouTube, Flickr, GoogleBuzz, Yammer, Friendfeed, MySpace and more...all in one place.
- Update your status and share links, images and video from the page you're viewing across all your networks simultaneously.
- Easily sync the status and update your status across all the sites at once.
The software is available for downloads at yoono.com.
Firefox users can download the addon from HERE as well.
Google chrome users can download the addon from HERE as well.
Read more...
Stay connected to social networks with Yoono
2011-10-25T16:49:00+05:45
Cool Samar
browser|browser addons|facebook|flickr|social networking|software|twitter|youtube|
Comments
Labels:
browser,
browser addons,
facebook,
flickr,
social networking,
software,
twitter,
youtube
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Sunday 16 October 2011
Demo Of Ubuntu 11.10 Runs On Browsers Supporting HTML5
Rather than posting photos and video stuffs, this time ubuntu has made a very interactive demo of newly released ubuntu 11.10. You can use the online tour just like a real ubuntu OS installed in your PC. This online tour feature is pretty impressive and helps people understand how the look, feel and functionality of ubuntu 11.10 is.
Visit the online tour.
Read more...
Visit the online tour.
Read more...
Demo Of Ubuntu 11.10 Runs On Browsers Supporting HTML5
2011-10-16T22:36:00+05:45
Cool Samar
ubuntu|ubuntu 11.10|
Comments
Labels:
ubuntu,
ubuntu 11.10
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Tuesday 11 October 2011
Center the text horizontally and vertically on a page in Microsoft Word
Microsoft word is the most widely used word processing software and of course, is an easy tool to use for writing properly formatted documents. Many times, you need to center the text horizontally and vertically in a page and this process is very simple in Microsoft Word.
There are two steps involved in this centering and as you might have guessed, they are horizontal centering and then vertical centering to have the final effect. Select the text you want to center and then follow the following steps:
Horizontal centering of the text
On the Home tab, click Center which is in Paragraph group.
Vertical centering of the text
On the Page Layout tab, click on the Page Setup dialog launcher at the bottom-right of Page Setup group.
Now select the Layout tab from the dialog box. Select Center from the Vertical Alignment dropdown and then select Selected Text from the Apply To dropdown. Then click Ok.
This should center your text both horizontally and vertically in the page. I hope this helps you. :)
Read more...
There are two steps involved in this centering and as you might have guessed, they are horizontal centering and then vertical centering to have the final effect. Select the text you want to center and then follow the following steps:
Horizontal centering of the text
On the Home tab, click Center which is in Paragraph group.
Vertical centering of the text
On the Page Layout tab, click on the Page Setup dialog launcher at the bottom-right of Page Setup group.
Now select the Layout tab from the dialog box. Select Center from the Vertical Alignment dropdown and then select Selected Text from the Apply To dropdown. Then click Ok.
This should center your text both horizontally and vertically in the page. I hope this helps you. :)
Read more...
Center the text horizontally and vertically on a page in Microsoft Word
2011-10-11T09:07:00+05:45
Cool Samar
microsoft word|tricks and tips|
Comments
Labels:
microsoft word,
tricks and tips
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Sunday 9 October 2011
Rip Audio CDs With Windows Media Player
You need not download any other Audio CD ripping software in windows to rip your Audio CD as Audio CD ripping can be easily done with windows media player. I was thinking I might need to download ripping tools but I just guessed WMP might also have such feature and yeah it had easy way to do so. I'm here to help those non-techie people out there rip the audio CD.
First insert your Audio CD and play it with windows media player. There's a ripping option directly available in the interface. The screenshot provided below will help you to adjust your ripping settings. You might want to adjust the rip settings from the interface itself. Then select the tracks that you want to rip and click on the Rip CD button. Ripping will take few minutes and then output folder will open.
Read more...
First insert your Audio CD and play it with windows media player. There's a ripping option directly available in the interface. The screenshot provided below will help you to adjust your ripping settings. You might want to adjust the rip settings from the interface itself. Then select the tracks that you want to rip and click on the Rip CD button. Ripping will take few minutes and then output folder will open.
Read more...
Rip Audio CDs With Windows Media Player
2011-10-09T12:29:00+05:45
Cool Samar
beginner|media player|tricks and tips|windows|
Comments
Labels:
beginner,
media player,
tricks and tips,
windows
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Tuesday 4 October 2011
Google URL Shortener Service - Goo.gl
If you are looking for URL shorteners, google has come up with the URL shortener service and now there's no need to use bit.ly or similar services as Google has come with the same service for us.
To access google URL shortening service, go to http://goo.gl/.
If you need any help or further information, check this page.
Read more...
To access google URL shortening service, go to http://goo.gl/.
If you need any help or further information, check this page.
Read more...
Google URL Shortener Service - Goo.gl
2011-10-04T14:37:00+05:45
Cool Samar
URL shortener|useful website|
Comments
Labels:
URL shortener,
useful website
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Monday 3 October 2011
How To Activate Administrator Account In Windows 7
Many of you might be wondering where is the administrator account in windows 7 that used to be available by default in win XP. By default, the administrator account is disabled in windows 7 and you will learn the simple way to enable that account.
First, run the command prompt with admin rights. For that, navigate to C:\windows\system32 and right click on cmd.exe and click on Run as administrator. Now type the following command in the command prompt and you are good to go.
On success, you would see the message as in the screenshot below and now your admin account is enabled for logging in.
Disabling is not difficult either. I guess you've already figured it out. Just type the following command to disable the administrator account.
I hope this helps. :)
Read more...
First, run the command prompt with admin rights. For that, navigate to C:\windows\system32 and right click on cmd.exe and click on Run as administrator. Now type the following command in the command prompt and you are good to go.
net user administrator /active:yes
On success, you would see the message as in the screenshot below and now your admin account is enabled for logging in.
Disabling is not difficult either. I guess you've already figured it out. Just type the following command to disable the administrator account.
net user administrator /active:yes
I hope this helps. :)
Read more...
How To Activate Administrator Account In Windows 7
2011-10-03T11:25:00+05:45
Cool Samar
administrator account|tricks and tips|windows|
Comments
Labels:
administrator account,
tricks and tips,
windows
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Thursday 29 September 2011
Simple Guide To Recording Counter Strike Game Using HLTV
Half-Life TV offers the ability to have an unlimited number of spectators watching online games. They can follow the game just like they would as a spectator on the game server. Also, it can be used to record the game you are playing. I am going to show how simply you can use HLTV to record your games.
HLTV.exe file is located at the root folder of your CounterStrike installation (eg: c:/Valve/Condition Zero). To record your game, run the hltv.exe file and then you need to connect to the Counter Strike server by issuing the connect IP:PORT. Check the screenshot below:
After the connection is successful, type record filename.dem and the recording will be initialized and in few seconds the actual recording will start as well.
After finishing recording of screenshot, you can type stop in the hltv console to stop and then just type exit to exit HLTV. To watch the demo later, run CounterStrike game and then in console(type ~ to reach console), type viewdemo filename.dem.
I hope this helps. :)
Read more...
HLTV.exe file is located at the root folder of your CounterStrike installation (eg: c:/Valve/Condition Zero). To record your game, run the hltv.exe file and then you need to connect to the Counter Strike server by issuing the connect IP:PORT. Check the screenshot below:
After the connection is successful, type record filename.dem and the recording will be initialized and in few seconds the actual recording will start as well.
After finishing recording of screenshot, you can type stop in the hltv console to stop and then just type exit to exit HLTV. To watch the demo later, run CounterStrike game and then in console(type ~ to reach console), type viewdemo filename.dem.
I hope this helps. :)
Read more...
Simple Guide To Recording Counter Strike Game Using HLTV
2011-09-29T16:03:00+05:45
Cool Samar
counterstrike|game|tricks and tips|
Comments
Labels:
counterstrike,
game,
tricks and tips
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Wednesday 28 September 2011
Tools For Customizing Ubuntu Into Your Custom Distro
Hello everybody, I'm listing some of the tools that can be used to customize the ubuntu distro and create your own flavour of ubuntu. I'm saying ubuntu specifically because I've tested them on ubuntu but some work for all debian based distro and maybe some work for all linux distro.
If you want to customize the ubuntu distro, you need an ISO file of the ubuntu of your preferred version. For the terminal lovers, the following two links are very helpful:
Ubuntu Live CD Customization
Ubuntu Install CD Customization
Now for those people who hate terminal and would like to the same thing using GUI, I'm listing here few of the tools that you can use.
1) Ubuntu Customization Kit: UCK is a tool that helps you customizing official Ubuntu Live CDs (including Kubuntu/Xubuntu and Edubuntu) to your needs. You can add any package to the live system like, for example, language packs, applications, etc.
2) RemasterSys: This script creates a livecd of the installed system. You can either make a distributable livecd or backup of your system. The resulting iso file can be used on any other PC that still meets the original minimum requirements of Ubuntu or Debian. Things like the graphics card and other hardware will be configured and setup automatically and you do not have to use identical hardware. Ubuntu's live boot tool, casper, currently blacklists Nvidia and AMD proprietary drivers so they will not be available on the live system and will need to be reinstalled after installation of your custom system.
3) Reconstructor Engine: Reconstructor is a GNU/Linux distribution customization and creation toolkit. It allows for the customization of the Ubuntu GNU/Linux distribution. Customizations include boot logo image and text color, wallpaper, themes, icons, applications, and more. Personally, I didn't like this one very much. Check this site.
4) Live Magic: Live-helper is a collection of programs that can be used to build Debian Live system images. The philosophy behind live-helper is to provide a collection of small, simple, and easily understood tools that can be used in your own program to automate building of a Live system.
5) Live Scripts: Linux Live is a set of shell scripts which allows you to create your own Live Linux from an already installed Linux distribution. The Live system you create will be bootable from CD-ROM or a disk device, for example USB Flash Drive, USB Pen Drive, Camera connected to USB port, and so on. People use Linux Live scripts to boot Linux from iPod as well.
6) Revisor For Fedora: Revisor enables you to customize and compose your own Fedora based installation and live media. It does so by presenting you a GUI with all options you can click your way through, a command-line interface and extended configuration files for more advanced users. Features that Revisor has vary from customizing the packages available during the installation and/or installed on the live media, to fully customizing the desktop environment for the live media.
I hope these helps. :)
Read more...
If you want to customize the ubuntu distro, you need an ISO file of the ubuntu of your preferred version. For the terminal lovers, the following two links are very helpful:
Ubuntu Live CD Customization
Ubuntu Install CD Customization
Now for those people who hate terminal and would like to the same thing using GUI, I'm listing here few of the tools that you can use.
1) Ubuntu Customization Kit: UCK is a tool that helps you customizing official Ubuntu Live CDs (including Kubuntu/Xubuntu and Edubuntu) to your needs. You can add any package to the live system like, for example, language packs, applications, etc.
2) RemasterSys: This script creates a livecd of the installed system. You can either make a distributable livecd or backup of your system. The resulting iso file can be used on any other PC that still meets the original minimum requirements of Ubuntu or Debian. Things like the graphics card and other hardware will be configured and setup automatically and you do not have to use identical hardware. Ubuntu's live boot tool, casper, currently blacklists Nvidia and AMD proprietary drivers so they will not be available on the live system and will need to be reinstalled after installation of your custom system.
3) Reconstructor Engine: Reconstructor is a GNU/Linux distribution customization and creation toolkit. It allows for the customization of the Ubuntu GNU/Linux distribution. Customizations include boot logo image and text color, wallpaper, themes, icons, applications, and more. Personally, I didn't like this one very much. Check this site.
4) Live Magic: Live-helper is a collection of programs that can be used to build Debian Live system images. The philosophy behind live-helper is to provide a collection of small, simple, and easily understood tools that can be used in your own program to automate building of a Live system.
5) Live Scripts: Linux Live is a set of shell scripts which allows you to create your own Live Linux from an already installed Linux distribution. The Live system you create will be bootable from CD-ROM or a disk device, for example USB Flash Drive, USB Pen Drive, Camera connected to USB port, and so on. People use Linux Live scripts to boot Linux from iPod as well.
6) Revisor For Fedora: Revisor enables you to customize and compose your own Fedora based installation and live media. It does so by presenting you a GUI with all options you can click your way through, a command-line interface and extended configuration files for more advanced users. Features that Revisor has vary from customizing the packages available during the installation and/or installed on the live media, to fully customizing the desktop environment for the live media.
I hope these helps. :)
Read more...
Tools For Customizing Ubuntu Into Your Custom Distro
2011-09-28T23:06:00+05:45
Cool Samar
distro customization|linux|software|ubuntu|useful website|
Comments
Labels:
distro customization,
linux,
software,
ubuntu,
useful website
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Happy Dashain 2011
We, the team of techgaun.com would like to wish all Hindus and Nepali people happy vijaya dashami 2066/2011 and we hope this Dashain brings peace, prosperity and love in each and every house of Nepal and we also hope that the country finds some right direction to attain political stability.
Read more...
Read more...
Happy Dashain 2011
2011-09-28T17:40:00+05:45
capricious solace
festivals and celebrations|happy dashain|
Comments
Labels:
festivals and celebrations,
happy dashain
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Shutter : Advanced Screenshot Tool For Linux
The default screenshot tool in linux(I'm using ubuntu 10.10) does not have much features as some of you might have desired but there exists yet another tool known as Shutter that has lots of functionalities as a screenshot tool. Shutter is a feature rich screenshot tool available for many flavours of linux distribution.
With shutter, you can take a screenshot of a specific area, window, your whole screen, or even of a website – apply different effects to it, draw on it to highlight points, and then upload to an image hosting site, all within one window. There are numerous plugins written in Perl and bash included within the shutter as plugins and you can give different sexy looks to your screenshot. So for a blogger, writer and screen-sharer, this tool is a must if you are using linux.
To install shutter, either open the software centre according to your distro, search for shutter and install from there. For ubuntu, you can alternatively type the following from your terminal to install shutter:
To open shutter, click on Applications -> Accessories -> Shutter. Then you can use various features of shutter to take screenshots of window, selection, websites and full screen and then edit your screenshot, hide the sensitive areas and apply effects of your choice to the screenshots.
Some sample screenshots of the tool itself:
GUI of shutter:
Screenshot of website:
Screenshot of selection:
Read more...
With shutter, you can take a screenshot of a specific area, window, your whole screen, or even of a website – apply different effects to it, draw on it to highlight points, and then upload to an image hosting site, all within one window. There are numerous plugins written in Perl and bash included within the shutter as plugins and you can give different sexy looks to your screenshot. So for a blogger, writer and screen-sharer, this tool is a must if you are using linux.
To install shutter, either open the software centre according to your distro, search for shutter and install from there. For ubuntu, you can alternatively type the following from your terminal to install shutter:
sudo apt-get install shutter
To open shutter, click on Applications -> Accessories -> Shutter. Then you can use various features of shutter to take screenshots of window, selection, websites and full screen and then edit your screenshot, hide the sensitive areas and apply effects of your choice to the screenshots.
Some sample screenshots of the tool itself:
GUI of shutter:
Screenshot of website:
Screenshot of selection:
Read more...
Shutter : Advanced Screenshot Tool For Linux
2011-09-28T17:13:00+05:45
Cool Samar
graphics|linux|screenshot|software|ubuntu|
Comments
Labels:
graphics,
linux,
screenshot,
software,
ubuntu
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Tuesday 27 September 2011
Qt4 Development Using Monkey Studio
Monkey Studio is a free and open-source crossplatform Qt 4 IDE. It is developed using the Qt library itself, meaning it will run on any platform supported by Qt 4. This allows you to work on the same project on multiple platforms using the same IDE. Monkey Studio uses the Qt Project file (.pro) to manage the project, and there are no extra files created.
With a active forum and wiki, Monkey Studio IDE offers pretty cool features for developing Qt4 Apps. Its noticeable features are:
- Monkey Studio also features * Advanced, customizable code editor, based on QScintilla.
- Syntax highlighting for more than 22 programming languages
- Templates wizard - create files or projects from templates
- Code restyling - quickly fix/update style of your code using AStyle
- Qt Designer integration
- Qt Assistant integration
To install MonkeyStudio in ubuntu, open the terminal and type:
For downloads for other platforms and more information, visit official website.
Read more...
With a active forum and wiki, Monkey Studio IDE offers pretty cool features for developing Qt4 Apps. Its noticeable features are:
- Monkey Studio also features * Advanced, customizable code editor, based on QScintilla.
- Syntax highlighting for more than 22 programming languages
- Templates wizard - create files or projects from templates
- Code restyling - quickly fix/update style of your code using AStyle
- Qt Designer integration
- Qt Assistant integration
To install MonkeyStudio in ubuntu, open the terminal and type:
sudo apt-get install monkeystudio
For downloads for other platforms and more information, visit official website.
Read more...
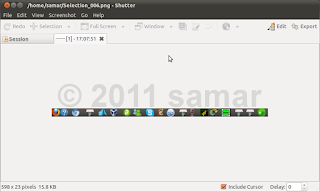
Qt4 Development Using Monkey Studio
2011-09-27T07:51:00+05:45
Cool Samar
development|ide|monkey studio|programming|qt|software|
Comments
Labels:
development,
ide,
monkey studio,
programming,
qt,
software
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Monday 26 September 2011
RSS and Related Security Issues For Business People
While RSS is a very simple way to expand your business and nothing complex is involved in RSS feed systems, you should never underestimate the security issues in any digitized systems, not even in really simple technology like RSS. A business company should always be aware of possible security risks in any system they are employing to help them in their tasks.
Most of you might believe there would not be much security issues in RSS feeds and feel that you need not worry about any cases of exploiting of your system but that's just a myth. Malicious attackers can inject scripts inside the feeds and affect thousands of feed readers with even a single vulnerability discovered in the popular RSS reader or aggregators.
Bad HTML or javascript can be injected as malware inside the feeds and if your business is gathering content from other sources and adding them to feeds, your feeds are likely to be affected by such malwares. Such scripts are generally injected in the feed titles, descriptions, links and other components of the RSS feeds. The scripts injected can exploit the possible vulnerabilities in the RSS readers of your subscribers leading to possible control of your subscriber's PC by the attacker. This can open possible backdoors by the installation of trojans or keyloggers using the proper exploits such as browser exploits, activex exploits, etc. and let the attacker steal the data by using possible local zone security attacks which can be the worst thing you can imagine happening to your business as customers are the life blood of every business and you engage customers everywhere. And if your customers are affected, then ultimately your business will be affected. Hence extreme care should be taken while importing content from other sources to develop your RSS contents.
Many times business owners like to include the comments from subscribers in the RSS contents and mostly they hardly watch the actual content in those comments. There is always a possibility of injection of malicious scripts in those comments as well. So proper filtering and stripping mechanism has to be employed before storing new contents to your RSS feeds rather than just storing those comments in the feed contents. The HTML tags such as script, embed, object, etc. are the ones that must be stripped out in most cases to avoid possible security issues. Also, using safe and secure RSS reader or aggregator is a good approach to RSS security. So you should choose the most secure RSS reader or aggregator from the available ones and suggest those to your subscribers. Also, make sure that your customers and employees use the latest and patched version of the reader so that maximum level of security is ensured.
In many cases, the RSS generators and other services in the RSS servers are also prone to security attacks and the attackers might be able to gain certain level of privilege in the system. In such case, the attackers can replace the original RSS feeds with their own affected version of RSS feeds which will then be delivered to your customers affecting your customers and your business as well. This can be devastating as this might lead not only to the script injections in the feeds but also stealing of many sensitive information from the server. For example, if your RSS server is used to host your business website or maybe for file sharing, the critical data related to them might be compromised as well. So proper security assessment of the server and network from the security professionals is necessary before taking your system live for production usage.
As a business owner, you must understand that security is a necessity in any system, be it a physical system or be it a digitized and online system and RSS is not an exception to this. If you want to succeed as a business owner, you should never underestimate the need of security and privacy and you should employ proper level of security as discussed above in the RSS system. Security in RSS system will ensure gaining of customers and expansion and promotion of your business so do not miss security practices in your RSS feed contents.
Read more...
Most of you might believe there would not be much security issues in RSS feeds and feel that you need not worry about any cases of exploiting of your system but that's just a myth. Malicious attackers can inject scripts inside the feeds and affect thousands of feed readers with even a single vulnerability discovered in the popular RSS reader or aggregators.
Bad HTML or javascript can be injected as malware inside the feeds and if your business is gathering content from other sources and adding them to feeds, your feeds are likely to be affected by such malwares. Such scripts are generally injected in the feed titles, descriptions, links and other components of the RSS feeds. The scripts injected can exploit the possible vulnerabilities in the RSS readers of your subscribers leading to possible control of your subscriber's PC by the attacker. This can open possible backdoors by the installation of trojans or keyloggers using the proper exploits such as browser exploits, activex exploits, etc. and let the attacker steal the data by using possible local zone security attacks which can be the worst thing you can imagine happening to your business as customers are the life blood of every business and you engage customers everywhere. And if your customers are affected, then ultimately your business will be affected. Hence extreme care should be taken while importing content from other sources to develop your RSS contents.
Many times business owners like to include the comments from subscribers in the RSS contents and mostly they hardly watch the actual content in those comments. There is always a possibility of injection of malicious scripts in those comments as well. So proper filtering and stripping mechanism has to be employed before storing new contents to your RSS feeds rather than just storing those comments in the feed contents. The HTML tags such as script, embed, object, etc. are the ones that must be stripped out in most cases to avoid possible security issues. Also, using safe and secure RSS reader or aggregator is a good approach to RSS security. So you should choose the most secure RSS reader or aggregator from the available ones and suggest those to your subscribers. Also, make sure that your customers and employees use the latest and patched version of the reader so that maximum level of security is ensured.
In many cases, the RSS generators and other services in the RSS servers are also prone to security attacks and the attackers might be able to gain certain level of privilege in the system. In such case, the attackers can replace the original RSS feeds with their own affected version of RSS feeds which will then be delivered to your customers affecting your customers and your business as well. This can be devastating as this might lead not only to the script injections in the feeds but also stealing of many sensitive information from the server. For example, if your RSS server is used to host your business website or maybe for file sharing, the critical data related to them might be compromised as well. So proper security assessment of the server and network from the security professionals is necessary before taking your system live for production usage.
As a business owner, you must understand that security is a necessity in any system, be it a physical system or be it a digitized and online system and RSS is not an exception to this. If you want to succeed as a business owner, you should never underestimate the need of security and privacy and you should employ proper level of security as discussed above in the RSS system. Security in RSS system will ensure gaining of customers and expansion and promotion of your business so do not miss security practices in your RSS feed contents.
Read more...
RSS and Related Security Issues For Business People
2011-09-26T16:24:00+05:45
Cool Samar
beginner|rss|security|
Comments
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Monday 12 September 2011
Facebook Pwn - Facebook Profile Dumper Tool
FBPwn is a cross-platform Java based Facebook profile dumper, sends friend requests to a list of Facebook profiles, and polls for the acceptance notification. Once the victim accepts the invitation, it dumps all their information,photos and friend list to a local folder.
Usage
A typical scenario is to gather the information from a user profile. The plugins are just a series of normal operations on FB, automated to increase the chance of you getting the info.
Typically, first you create a new blank account for the purpose of the test. Then, the friending plugin works first, by adding all the friends of the victim (to have some common friends). Then the clonning plugin asks you to choose one of the victims friends. The cloning plugin clones only the display picture and the display name of the chosen friend of victim and set it to the authenticated account. Afterwards, a friend request is sent to the victim's account. The dumper polls waiting for the friend to accept. As soon as the victim accepts the friend request, the dumper starts to save all accessable HTML pages (info, images, tags, ...etc) for offline examining.
After a a few minutes, probably the victim will unfriend the fake account after he/she figures out it's a fake, but probably it's too late!
Check FBPwn Google Code Page
Read more...
Usage
A typical scenario is to gather the information from a user profile. The plugins are just a series of normal operations on FB, automated to increase the chance of you getting the info.
Typically, first you create a new blank account for the purpose of the test. Then, the friending plugin works first, by adding all the friends of the victim (to have some common friends). Then the clonning plugin asks you to choose one of the victims friends. The cloning plugin clones only the display picture and the display name of the chosen friend of victim and set it to the authenticated account. Afterwards, a friend request is sent to the victim's account. The dumper polls waiting for the friend to accept. As soon as the victim accepts the friend request, the dumper starts to save all accessable HTML pages (info, images, tags, ...etc) for offline examining.
After a a few minutes, probably the victim will unfriend the fake account after he/she figures out it's a fake, but probably it's too late!
Check FBPwn Google Code Page
Read more...
Facebook Pwn - Facebook Profile Dumper Tool
2011-09-12T22:53:00+05:45
Cool Samar
facebook|hacking|information gathering|
Comments
Labels:
facebook,
hacking,
information gathering
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Simple Movie Searching Trick with Google
While this post is not anything other than just another simple google dork for advanced google users, it still will help a lot of net beginners to search movies using google.
The trick for searching movies is just another usage of directory browsing feature in many webservers. So our text would be something like below:
Just replace the movie name with the name of your movie and you are good to go. Moreover, you can customize this dork to include extensions(such as .avi, .mkv). Just be creative and you'll find most of the movies to download just by using google. And for download, I use axel or sometimes FatRat under linux.
For example, check the first result in the following dork for sniper movie. Yeah it is simple and really works.
Read more...
The trick for searching movies is just another usage of directory browsing feature in many webservers. So our text would be something like below:
"index of /" "parent directory" "movie name"
Just replace the movie name with the name of your movie and you are good to go. Moreover, you can customize this dork to include extensions(such as .avi, .mkv). Just be creative and you'll find most of the movies to download just by using google. And for download, I use axel or sometimes FatRat under linux.
For example, check the first result in the following dork for sniper movie. Yeah it is simple and really works.
"index of /" "parent directory" inurl:movies "sniper" ".avi"
Read more...
Simple Movie Searching Trick with Google
2011-09-12T09:43:00+05:45
Cool Samar
google hacking|tricks and tips|
Comments
Labels:
google hacking,
tricks and tips
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Nixory - A Light Antispyware Tool
Nixory is a light and handy open source antispyware tool aimed at removing malicious tracking cookies. It currently supports Mozilla Firefox, Google Chrome and Internet Explorer and it runs on all major OS including Windows, Linux and MacOSx.
For more information and download, visit nixory sourceforge page.
Read more...
For more information and download, visit nixory sourceforge page.
Read more...
Nixory - A Light Antispyware Tool
2011-09-12T09:32:00+05:45
Cool Samar
browser|security|software|
Comments
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
LinuxFoundation.org, Linux.com and their subdomains hacked
Linuxfoundation.org, linux.com and their subdomains have been compromised by the hackers and the linux foundation has taken all the related servers down for clean-up.
The index page of linuxfoundation.org and linux.com both state:
Linux Foundation infrastructure including LinuxFoundation.org, Linux.com, and their subdomains are down for maintenance due to a security breach that was discovered on September 8, 2011. The Linux Foundation made this decision in the interest of extreme caution and security best practices. We believe this breach was connected to the intrusion on kernel.org.
We are in the process of restoring services in a secure manner as quickly as possible. As with any intrusion and as a matter of caution, you should consider the passwords and SSH keys that you have used on these sites compromised. If you have reused these passwords on other sites, please change them immediately. We are currently auditing all systems and will update this statement when we have more information.
We apologize for the inconvenience. We are taking this matter seriously and appreciate your patience. The Linux Foundation infrastructure houses a variety of services and programs including Linux.com, Open Printing, Linux Mark, Linux Foundation events and others, but does not include the Linux kernel or its code repositories.
Please contact us at info@linuxfoundation.org with questions about this matter.
The Linux Foundation
Read more...
The index page of linuxfoundation.org and linux.com both state:
Linux Foundation infrastructure including LinuxFoundation.org, Linux.com, and their subdomains are down for maintenance due to a security breach that was discovered on September 8, 2011. The Linux Foundation made this decision in the interest of extreme caution and security best practices. We believe this breach was connected to the intrusion on kernel.org.
We are in the process of restoring services in a secure manner as quickly as possible. As with any intrusion and as a matter of caution, you should consider the passwords and SSH keys that you have used on these sites compromised. If you have reused these passwords on other sites, please change them immediately. We are currently auditing all systems and will update this statement when we have more information.
We apologize for the inconvenience. We are taking this matter seriously and appreciate your patience. The Linux Foundation infrastructure houses a variety of services and programs including Linux.com, Open Printing, Linux Mark, Linux Foundation events and others, but does not include the Linux kernel or its code repositories.
Please contact us at info@linuxfoundation.org with questions about this matter.
The Linux Foundation
Read more...
LinuxFoundation.org, Linux.com and their subdomains hacked
2011-09-12T09:23:00+05:45
Cool Samar
hacking|news|
Comments
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Monday 5 September 2011
Solving MySQL Connection Error In Non-standard Bundles
For a standard MySQL installation from software repository, there won't be much problem in using MySQL for different connections however if you install some other bundles such as LAMPP, you are most likely to see an error Can't connect to local MySQL server through socket '/var/run/mysqld/mysqld.sock' however the solution to this is as easy as making a symbolic link of MySQL socket.
In my case, I had LAMPP installed and the MySQL socket was in the folder /opt/lampp/var/mysql/mysql.sock and your might be different so first figure out the location of this MySQL socket and then just enter the following commands and you're done.
That should work as a charm. I hope this helps :)
Read more...
In my case, I had LAMPP installed and the MySQL socket was in the folder /opt/lampp/var/mysql/mysql.sock and your might be different so first figure out the location of this MySQL socket and then just enter the following commands and you're done.
samar@Techgaun:~$ sudo mkdir /var/run/mysqld/
samar@Techgaun:~$ sudo ln -s /opt/lampp/var/mysql/mysql.sock /var/run/mysqld/mysqld.sock
samar@Techgaun:~$ sudo ln -s /opt/lampp/var/mysql/mysql.sock /var/run/mysqld/mysqld.sock
That should work as a charm. I hope this helps :)
Read more...
Solving MySQL Connection Error In Non-standard Bundles
2011-09-05T09:12:00+05:45
Cool Samar
linux|mysql|tricks and tips|
Comments
Labels:
linux,
mysql,
tricks and tips
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Saturday 3 September 2011
Javascript Linux Emulator
JS/Linux is a javascript linux emulator developed by Fabrice Bellard and I believe its a very creative concept. Anyway, check the javascript linux here. Isn't it fun to have linux in the browser :D
Read more...
Read more...
Javascript Linux Emulator
2011-09-03T21:36:00+05:45
Cool Samar
javascript|linux|
Comments
Labels:
javascript,
linux
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Tuesday 30 August 2011
XSS Vulnerability in Ladypopular.com
The popular girl's online game play site ladypopular.com suffers from a cross site scripting vulnerability. The GET parameter "error_message" is not properly sanitized and allows the injection of HTML and javascript code.
Check the vulnerable URL.
I've notified the ladypopular team about the vulnerability.
Read more...
Check the vulnerable URL.
I've notified the ladypopular team about the vulnerability.
Read more...
XSS Vulnerability in Ladypopular.com
2011-08-30T17:58:00+05:45
Cool Samar
cross site scripting|ladypopular.com|
Comments
Labels:
cross site scripting,
ladypopular.com
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Monday 29 August 2011
More Multi-Tabbed Putty Tools
In the previous post, MTPuTTY(which was written in native win32 code) was introduced as the solution for multiple tabs in Putty. But there are few other solutions already for multiple tabs in PuTTY which I am introducing in this post.
Both the tools I am talking about require .NET framework 2.0 to function which was not the necessity of MTPuTTY.
The first one is PuTTY Connection Manager addon. PuTTY Connection Manager is a free PuTTY Client Add-on for Windows platforms which goal is to provide a solution for managing multiple PuTTY instances.
For more details and downloads, visit official site.
Another tool is PuTTYTabs which reads the Registry information of PuTTY and opens a new tab for each opened window by the user. The source code of PuttyTabs is also available for download.
For more details and downloads, visit official site.
Read more...
Both the tools I am talking about require .NET framework 2.0 to function which was not the necessity of MTPuTTY.
The first one is PuTTY Connection Manager addon. PuTTY Connection Manager is a free PuTTY Client Add-on for Windows platforms which goal is to provide a solution for managing multiple PuTTY instances.
For more details and downloads, visit official site.
Another tool is PuTTYTabs which reads the Registry information of PuTTY and opens a new tab for each opened window by the user. The source code of PuttyTabs is also available for download.
For more details and downloads, visit official site.
Read more...
More Multi-Tabbed Putty Tools
2011-08-29T15:42:00+05:45
Cool Samar
ssh|windows|
Comments
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Putty with Tab using MT-Putty
If you are familiar with SSH, you've most likely used Putty for SSH logins, tunnelling, etc. One bad thing about putty is we need to open separate windows for each connection but TTY Plus has developed MTPuTTY as solution for this.
MTPuTTY (Multi-Tabbed PuTTY) is a small free utility enabling you to wrap unlimited number of PuTTY applications in one tabbed GUI interface. You are still continue using your favorite SSH client, but you are no longer messing around with PuTTY windows - each window will be opened in a separate tab. However, as of now, it is for only windows system.
Features:
All PuTTY features
Supports all PuTTY protocols - SSH, Telnet, Rlogin, Raw. Supports PuTTY session. You can control and change PuTTY command line parameters. You can run PuTTY configuration from within the program.
Automation
Can automatically login the remote servers and "type" your passwords. Can run any script after login. Can "type" a script in several PuTTY tabs simultaneously.
Easy to use
Clear tabbed user interface. Servers are grouped in a sidebar. Taskbar to quick access to basic program tasks. Any PuTTY tab can be detached and converted into a general PuTTY window.
Smart code
Native Win32 code - no need to have any libraries (like .NET, VB etc). Multithreaded automation tasks - freezing in one PuTTY tab will not freeze the other ones.
Download MTPuTTY
Read more...
MTPuTTY (Multi-Tabbed PuTTY) is a small free utility enabling you to wrap unlimited number of PuTTY applications in one tabbed GUI interface. You are still continue using your favorite SSH client, but you are no longer messing around with PuTTY windows - each window will be opened in a separate tab. However, as of now, it is for only windows system.
Features:
All PuTTY features
Supports all PuTTY protocols - SSH, Telnet, Rlogin, Raw. Supports PuTTY session. You can control and change PuTTY command line parameters. You can run PuTTY configuration from within the program.
Automation
Can automatically login the remote servers and "type" your passwords. Can run any script after login. Can "type" a script in several PuTTY tabs simultaneously.
Easy to use
Clear tabbed user interface. Servers are grouped in a sidebar. Taskbar to quick access to basic program tasks. Any PuTTY tab can be detached and converted into a general PuTTY window.
Smart code
Native Win32 code - no need to have any libraries (like .NET, VB etc). Multithreaded automation tasks - freezing in one PuTTY tab will not freeze the other ones.
Download MTPuTTY
Read more...
Putty with Tab using MT-Putty
2011-08-29T15:21:00+05:45
Cool Samar
software|ssh|windows|
Comments
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Sunday 28 August 2011
Real time video capturing and benchmarking with FRAPS
Fraps is a universal Windows application that can be used with games using DirectX or OpenGL graphic technology. This application software can be used for real time video capturing and benchmarking.
In its current form Fraps performs many tasks and can best be described as:
Benchmarking Software - Show how many Frames Per Second (FPS) you are getting in a corner of your screen. Perform custom benchmarks and measure the frame rate between any two points. Save the statistics out to disk and use them for your own reviews and applications.
Screen Capture Software - Take a screenshot with the press of a key! There's no need to paste into a paint program every time you want a new shot. Your screen captures are automatically named and timestamped.
Realtime Video Capture Software - Have you ever wanted to record video while playing your favourite game? Come join the Machinima revolution! Throw away the VCR, forget about using a DV cam, game recording has never been this easy! Fraps can capture audio and video up to 2560x1600 with custom frame rates from 1 to 120 frames per second!
Download Free Version
Read more...
In its current form Fraps performs many tasks and can best be described as:
Benchmarking Software - Show how many Frames Per Second (FPS) you are getting in a corner of your screen. Perform custom benchmarks and measure the frame rate between any two points. Save the statistics out to disk and use them for your own reviews and applications.
Screen Capture Software - Take a screenshot with the press of a key! There's no need to paste into a paint program every time you want a new shot. Your screen captures are automatically named and timestamped.
Realtime Video Capture Software - Have you ever wanted to record video while playing your favourite game? Come join the Machinima revolution! Throw away the VCR, forget about using a DV cam, game recording has never been this easy! Fraps can capture audio and video up to 2560x1600 with custom frame rates from 1 to 120 frames per second!
Download Free Version
Read more...
Real time video capturing and benchmarking with FRAPS
2011-08-28T22:11:00+05:45
Cool Samar
graphics|software|video|
Comments
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Wednesday 24 August 2011
Resizing Virtual Disk Size Under Virtualbox 4 and Higher
In the earlier versions(< 4), there was not any direct method of resizing the size of virtual box disk however with the release of Virtualbox 4 and higher, the VBoxManage tool can be easily used to resize the vbox disks.
Open the terminal and navigate to the folder that contains your Vbox disk and just type the following command and in few secs, you are done.
The above command will resize the filename.vdi disk to 30 GB(30GB = 30*1024 = 30720).
If you are running virtualbox version less than 4, then you will have to create a bigger virtual disk and then clone the content from the existing virtual disk. You can freely download the disk cloning/backup tools for cloning. I hope this helps.
Read more...
Open the terminal and navigate to the folder that contains your Vbox disk and just type the following command and in few secs, you are done.
VBoxManage modifyhd filename.vdi --resize 30720
The above command will resize the filename.vdi disk to 30 GB(30GB = 30*1024 = 30720).
If you are running virtualbox version less than 4, then you will have to create a bigger virtual disk and then clone the content from the existing virtual disk. You can freely download the disk cloning/backup tools for cloning. I hope this helps.
Read more...
Resizing Virtual Disk Size Under Virtualbox 4 and Higher
2011-08-24T18:57:00+05:45
Cool Samar
tricks and tips|virtualbox|
Comments
Labels:
tricks and tips,
virtualbox
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Anonymous and Secure Web Surfing With JonDoFox
JonDoFox is a firefox profile that has been optimized for anonymous and secure web surfing. The profile requires a proxy changer such as Tor. However JonDoFox makers have also developed JonDo as the proxy changer.
JonDoFox is available for all major platforms and debian/ubuntu users can download the .deb package for easy installation. For downloads and installation instructions, visit the JonDoFox page.
Read more...
JonDoFox is available for all major platforms and debian/ubuntu users can download the .deb package for easy installation. For downloads and installation instructions, visit the JonDoFox page.
Read more...
Anonymous and Secure Web Surfing With JonDoFox
2011-08-24T09:38:00+05:45
Cool Samar
anonymity|mozilla firefox|
Comments
Labels:
anonymity,
mozilla firefox
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Sunday 21 August 2011
Web Server[HTTP] Fingerprinting With httprint
Earlier I posted about web server fingerprinting using telnet however more sophisticated tools have been developed out there and one of them is httprint. httprint is a web server fingerprinting tool. It relies on web server characteristics to accurately identify web servers, despite the fact that they may have been obfuscated by changing the server banner strings, or by plug-ins such as mod_security or servermask. httprint can also be used to detect web enabled devices which do not have a server banner string, such as wireless access points, routers, switches, cable modems, etc. httprint uses text signature strings and it is very easy to add signatures to the signature database.
Features
-Identification of web servers despite the banner string and any other obfuscation. httprint can successfully identify the underlying web servers when their headers are mangled by either patching the binary, by modules such as mod_security.c or by commercial products such as ServerMask. Click here to see an example of how httprint detects disguised servers.
-Inventorying of web enabled devices such as printers, routers, switches, wireless access points, etc. Click on the sample HTML report.
-Customisable web server signature database. To add new signatures, simply cut and paste the httprint output against unknown servers into the signatures text file.
-Confidence Ratings. httprint now picks the best matches based on confidence ratings, derived using a fuzzy logic technique, instead of going by the highest weight. More details on the significance of confidence ratings can be found in section 8.4 of the Introduction to HTTP fingerprinting paper.
-Multi-threaded engine. httprint v301 is a complete re-write, featuring a multi-threaded scanner, to process multiple hosts in parallel. This greatly saves scanning time. *multi-threading is not yet supported in the FreeBSD version.
-SSL information gathering. httprint now gathers SSL certificate information, which helps you identify expired SSL certificates, ciphers used, certificate issuer, and other such SSL related details.
-Automatic SSL detection. httprint can detect if a port is SSL enabled or not, and can automatically switch to SSL connections when needed.
-Automatic traversal of HTTP 301 and 302 redirects. Many servers who have transferred their content to other servers send a default redirect response towards all HTTP requests. httprint now follows the redirection and fingerprints the new server pointed to. This feature is enabled by default and can be turned off, if needed.
-Ability to import web servers from nmap network scans. httprint can import nmap's xml output files.
-Reports in HTML, CSV and XML formats.
-Available on Linux, Mac OS X, FreeBSD (command line only) and Win32 (command line and GUI)
For more information and downloads, Check this link.
Also, if you want to learn more about webserver fingerprinting, I would highly recommend you to read this paper.
Read more...
Features
-Identification of web servers despite the banner string and any other obfuscation. httprint can successfully identify the underlying web servers when their headers are mangled by either patching the binary, by modules such as mod_security.c or by commercial products such as ServerMask. Click here to see an example of how httprint detects disguised servers.
-Inventorying of web enabled devices such as printers, routers, switches, wireless access points, etc. Click on the sample HTML report.
-Customisable web server signature database. To add new signatures, simply cut and paste the httprint output against unknown servers into the signatures text file.
-Confidence Ratings. httprint now picks the best matches based on confidence ratings, derived using a fuzzy logic technique, instead of going by the highest weight. More details on the significance of confidence ratings can be found in section 8.4 of the Introduction to HTTP fingerprinting paper.
-Multi-threaded engine. httprint v301 is a complete re-write, featuring a multi-threaded scanner, to process multiple hosts in parallel. This greatly saves scanning time. *multi-threading is not yet supported in the FreeBSD version.
-SSL information gathering. httprint now gathers SSL certificate information, which helps you identify expired SSL certificates, ciphers used, certificate issuer, and other such SSL related details.
-Automatic SSL detection. httprint can detect if a port is SSL enabled or not, and can automatically switch to SSL connections when needed.
-Automatic traversal of HTTP 301 and 302 redirects. Many servers who have transferred their content to other servers send a default redirect response towards all HTTP requests. httprint now follows the redirection and fingerprints the new server pointed to. This feature is enabled by default and can be turned off, if needed.
-Ability to import web servers from nmap network scans. httprint can import nmap's xml output files.
-Reports in HTML, CSV and XML formats.
-Available on Linux, Mac OS X, FreeBSD (command line only) and Win32 (command line and GUI)
For more information and downloads, Check this link.
Also, if you want to learn more about webserver fingerprinting, I would highly recommend you to read this paper.
Read more...
Web Server[HTTP] Fingerprinting With httprint
2011-08-21T14:58:00+05:45
Cool Samar
fingerprinting|hacking|
Comments
Labels:
fingerprinting,
hacking
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Basic Web Server Version Fingerprinting Using Telnet Client
Hi this time I am presenting you a simple quick tip that can be used to fingerprint the web servers. This can be quite handy for basic fingerprinting to determine web server version.
At first, open your command prompt/terminal and then type:
If everything is working fine, type either of the below in the terminal(as per the protocol version) and then press ENTER twice to get result from the server:
or
It will output some HTML content with the basic web server information at the end. Sample output would like below:
Note that this method works only if the web server provides the HEAD method as one of its methods(Other methods you might have commonly heard are GET, and POST).
Read more...
At first, open your command prompt/terminal and then type:
telnet
If everything is working fine, type either of the below in the terminal(as per the protocol version) and then press ENTER twice to get result from the server:
HEAD/ HTTP/1.1
or
HEAD/ HTTP/1.0
It will output some HTML content with the basic web server information at the end. Sample output would like below:
Apache/2.0.63 (Unix) mod_ssl/2.0.63 OpenSSL/0.9.8e-fips-rhel5 mod_bwlimited/1.4 Server at ds01.nepallink.net Port 80
Note that this method works only if the web server provides the HEAD method as one of its methods(Other methods you might have commonly heard are GET, and POST).
Read more...
Basic Web Server Version Fingerprinting Using Telnet Client
2011-08-21T14:51:00+05:45
Cool Samar
fingerprinting|
Comments
Labels:
fingerprinting
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Friday 19 August 2011
Open Source Anti-theft Solution For MAC, PCs and Phones
Prey is an open source application that helps us track the lost laptops or phones. Prey lets you keep track of your phone or laptop at all times, and will help you find it if it ever gets lost or stolen. It's lightweight, open source software, and free for anyone to use.
In order to understand more about the project, visit the Official website.
Also try this video tutorial for configuring the Prey application.
I hope it becomes useful for you. :)
Read more...
In order to understand more about the project, visit the Official website.
Also try this video tutorial for configuring the Prey application.
I hope it becomes useful for you. :)
Read more...
Open Source Anti-theft Solution For MAC, PCs and Phones
2011-08-19T13:33:00+05:45
Cool Samar
anti-theft|security|software|
Comments
Labels:
anti-theft,
security,
software
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Wally: Advanced Utility To Change Wallpaper
Wally is a Qt4 wallpaper changer using multiple sources like files, folders, FTP remote folders, Flickr, Yahoo!, Panoramio, Pikeo, Ipernity, Photobucket, Buzznet, Picasa and Smugmug images. It is available in many languages. Supported Linux window managers are GNOME, KDE 3, KDE 4, Xfce 4, BlackBox, FluxBox, Window Maker, and FVWM.
Features
· Runs on Win32, Linux and MacOSX platforms
· History support
· Many wallpaper layouts available on all platforms
· EXIF data available over picture and in system tray tooltip
· Save downloaded photos
· Proxy support
Wally Download Page
It is available in ubuntu repository so you can install easily from ubuntu software center.
Read more...
Features
· Runs on Win32, Linux and MacOSX platforms
· History support
· Many wallpaper layouts available on all platforms
· EXIF data available over picture and in system tray tooltip
· Save downloaded photos
· Proxy support
Wally Download Page
It is available in ubuntu repository so you can install easily from ubuntu software center.
Read more...
Wally: Advanced Utility To Change Wallpaper
2011-08-19T13:17:00+05:45
Cool Samar
graphics|linux|software|ubuntu|
Comments
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Anonymous and Encrypted Torrent Download With Anomos
Anomos is a free and open source standalone anonymous and encrypted torrent client so if you are too concerned about anonymity, why not try this torrent client. Anomos is available for all major platforms including windows, linux and OSX.
Anomos Quote:
Anomos is a pseudonymous, encrypted multi-peer-to-peer file distribution protocol. It is based on the peer/tracker concept of BitTorrent in combination with an onion routing anonymization layer, with the added benefit of end-to-end encryption. By combining these technologies, we have created a platform where by no party outside of the trusted tracker will have any information about who a peer is or what they are downloading.
smwhite
Anomos is designed to be easy to use – you won’t even be aware of the security that it provides. Anybody who is already familiar with BitTorrent won’t have to do anything differently, other than use ‘atorrent’ files rather than ‘torrent’ files.
For more technical details, please see this blog post.
For downloads and more information, visit the Anomos Official Site.
Read more...
Anomos Quote:
Anomos is a pseudonymous, encrypted multi-peer-to-peer file distribution protocol. It is based on the peer/tracker concept of BitTorrent in combination with an onion routing anonymization layer, with the added benefit of end-to-end encryption. By combining these technologies, we have created a platform where by no party outside of the trusted tracker will have any information about who a peer is or what they are downloading.
smwhite
Anomos is designed to be easy to use – you won’t even be aware of the security that it provides. Anybody who is already familiar with BitTorrent won’t have to do anything differently, other than use ‘atorrent’ files rather than ‘torrent’ files.
For more technical details, please see this blog post.
For downloads and more information, visit the Anomos Official Site.
Read more...
Anonymous and Encrypted Torrent Download With Anomos
2011-08-19T12:45:00+05:45
Cool Samar
anonymity|security|torrent|
Comments
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
BleachBit : Disk Cleanup Utility For Windows and Linux
Bleachbit is a free and open-source utility that can be used to clean Junk space to free disk space and maintain privacy.
BleachBit quickly frees disk space and tirelessly guards your privacy. Free cache, delete cookies, clear Internet history, shred temporary files, delete logs, and discard junk you didn't know was there. Designed for Linux and Windows systems, it wipes clean 90 applications including Firefox, Internet Explorer, Adobe Flash, Google Chrome, Opera, Safari,and more. Beyond simply deleting files, BleachBit includes advanced features such as shredding files to prevent recovery, wiping free disk space to hide traces of files deleted by other applications, and vacuuming Firefox to make it faster. Better than free, BleachBit is open source.
Downloads and more information available at Bleachbit SourceForge Page.
Read more...
BleachBit quickly frees disk space and tirelessly guards your privacy. Free cache, delete cookies, clear Internet history, shred temporary files, delete logs, and discard junk you didn't know was there. Designed for Linux and Windows systems, it wipes clean 90 applications including Firefox, Internet Explorer, Adobe Flash, Google Chrome, Opera, Safari,and more. Beyond simply deleting files, BleachBit includes advanced features such as shredding files to prevent recovery, wiping free disk space to hide traces of files deleted by other applications, and vacuuming Firefox to make it faster. Better than free, BleachBit is open source.
Downloads and more information available at Bleachbit SourceForge Page.
Read more...
BleachBit : Disk Cleanup Utility For Windows and Linux
2011-08-19T12:24:00+05:45
Cool Samar
linux|security|software|windows|
Comments
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
How To Crack Windows 7
This guide is not written by me as I never use windows 7 but one hacker friend of mine found this and sent it to me so I thought why not post for everyone out there to try this stuff to have no need of activating their windows 7.
If anyone knows who was the original author of this little guide, please post in the comment so that I can edit this post to give proper credit to the author.
First you will have to download Windows 7 loader from the link below:
http://www.datafilehost.com/download-ba73398b.html
Click install.
After that;
Remove update KB971033
1. Click start and search 'windows update'
2. Hit Installed Updates. If that link isn't there, hit "view update history" and hit the "installed updates" link at the top.
3. Find update KB971033.
4. Right click it and hit 'uninstall'
5. Restart your compy ;p
6. Go into Windows update again
7. Find the update KB971033
8. Right-click and hit 'hide update from installing'
If that didn't work, open a cmd and type:
Then you never have to activate again:D
Read more...
If anyone knows who was the original author of this little guide, please post in the comment so that I can edit this post to give proper credit to the author.
First you will have to download Windows 7 loader from the link below:
http://www.datafilehost.com/download-ba73398b.html
Click install.
After that;
Remove update KB971033
1. Click start and search 'windows update'
2. Hit Installed Updates. If that link isn't there, hit "view update history" and hit the "installed updates" link at the top.
3. Find update KB971033.
4. Right click it and hit 'uninstall'
5. Restart your compy ;p
6. Go into Windows update again
7. Find the update KB971033
8. Right-click and hit 'hide update from installing'
If that didn't work, open a cmd and type:
slmgr.vbs -rearm
Then you never have to activate again:D
Read more...
How To Crack Windows 7
2011-08-19T10:36:00+05:45
Cool Samar
cracking|windows|
Comments
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
IPV6 Attacking Toolkit - THC-ipV6 Toolkit Released
The famous hackers group The Hacker Choice(THC) has released a set of tools to attack the IPv6 protocol. IPv6 is the descendant of IPv4 protocol which was purposed due to exhaustion of the IPv4 pool.
THC writes:
THC is proud to be the first who are releasing an comprehensive attack toolkit for the IPv6 protocol suite. It comprises of state-of-the-art tools for alive scanning, man-in-the-middle attacks, denial-of-service etc. which exploits inherent vulnerabilities in IPv6. Included is a fast and easy to use packet crafting library to create your own attack tools.
For more information on the project, visit the THC IPv6 Project Page.
Download Here
Read more...
THC writes:
THC is proud to be the first who are releasing an comprehensive attack toolkit for the IPv6 protocol suite. It comprises of state-of-the-art tools for alive scanning, man-in-the-middle attacks, denial-of-service etc. which exploits inherent vulnerabilities in IPv6. Included is a fast and easy to use packet crafting library to create your own attack tools.
For more information on the project, visit the THC IPv6 Project Page.
Download Here
Read more...
IPV6 Attacking Toolkit - THC-ipV6 Toolkit Released
2011-08-19T09:59:00+05:45
Cool Samar
hacking|internet protocol|security|software|
Comments
Labels:
hacking,
internet protocol,
security,
software
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Backtrack 5 R1 Released
The most widely used linux-based penetration testing distro, BackTrack had a new release yesterday. Backtrack 5 R1 was released on August 18 which adds 30 new tools in the famous hacker's distro.
Offsec team says:
We are really happy with this release, and believe that as with every release, this is our best one yet. Some pesky issues such as rfkill in VMWare with rtl8187 issues have been fixed, which provides for a much more solid experience with BackTrack.
We’ve released Gnome and KDE ISO images for 32 and 64 bit (no arm this release, sorry!), as well as a VMWare image of a 32 bit Gnome install, with VMWare Tools pre-installed.
For downloads, visit Backtrack Download Page.
Read more...
Offsec team says:
We are really happy with this release, and believe that as with every release, this is our best one yet. Some pesky issues such as rfkill in VMWare with rtl8187 issues have been fixed, which provides for a much more solid experience with BackTrack.
We’ve released Gnome and KDE ISO images for 32 and 64 bit (no arm this release, sorry!), as well as a VMWare image of a 32 bit Gnome install, with VMWare Tools pre-installed.
For downloads, visit Backtrack Download Page.
Read more...
Backtrack 5 R1 Released
2011-08-19T09:25:00+05:45
Cool Samar
backtrack|hacking|linux|security|
Comments
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Sunday 31 July 2011
Download Subtitles For Movies While Watching
Hi everybody, my apologies for not posting frequently but I'm busy with my end semester exams. Today, I am going to talk on how you can download subtitles for the movies you are watching in your VLC player or totem media player.
1) VLC: VLC from videolan is one of the best media players and my personal favourite as well. This open source player is simple yet pretty much powerful. In vlc, you can download subtitles for the movies you are watching by installing the lua script for subtitle download.
A little info about LUA: Lua is a powerful, fast, lightweight, embeddable scripting language. Lua combines simple procedural syntax with powerful data description constructs based on associative arrays and extensible semantics. Lua is dynamically typed, runs by interpreting bytecode for a register-based virtual machine, and has automatic memory management with incremental garbage collection, making it ideal for configuration, scripting, and rapid prototyping.
So all you have to do is grab subtitles finder script and then install the lua file in the proper directory according to your system.
You must put the file in the folder:
- Windows (all users): %ProgramFiles%\VideoLAN\VLC\lua\extensions\
- Windows (current user): %APPDATA%\VLC\lua\extensions\
- Linux (all users): /usr/share/vlc/lua/extensions/
- Linux (current user): ~/.local/share/vlc/lua/extensions/
- Mac OS X (all users): /Applications/VLC.app/Contents/MacOS/share/lua/extensions/
This script currently gets the subtitles from OpenSubTitles.Org and to use this tool, start the movie in VLC and go to View -> Subtitles and then you can search the subtitle from there easily. Also, there is a upload feature though I've not checked it.
2) Totem: Totem is my another favourite player for being simple and quite fast. This one even does not need any extra plugin/extension to be downloaded. The subtitle downloader plugin is already there within the player but most of us don't know that it is available. To use the plugin, just activate it from the Edit -> Plugins and then just go to View -> Subtitles -> Download Movie Subtitles.
If you are looking for some other alternatives, try splayer.
I hope this works well for you. :)
Read more...
1) VLC: VLC from videolan is one of the best media players and my personal favourite as well. This open source player is simple yet pretty much powerful. In vlc, you can download subtitles for the movies you are watching by installing the lua script for subtitle download.
A little info about LUA: Lua is a powerful, fast, lightweight, embeddable scripting language. Lua combines simple procedural syntax with powerful data description constructs based on associative arrays and extensible semantics. Lua is dynamically typed, runs by interpreting bytecode for a register-based virtual machine, and has automatic memory management with incremental garbage collection, making it ideal for configuration, scripting, and rapid prototyping.
So all you have to do is grab subtitles finder script and then install the lua file in the proper directory according to your system.
You must put the file in the folder:
- Windows (all users): %ProgramFiles%\VideoLAN\VLC\lua\extensions\
- Windows (current user): %APPDATA%\VLC\lua\extensions\
- Linux (all users): /usr/share/vlc/lua/extensions/
- Linux (current user): ~/.local/share/vlc/lua/extensions/
- Mac OS X (all users): /Applications/VLC.app/Contents/MacOS/share/lua/extensions/
This script currently gets the subtitles from OpenSubTitles.Org and to use this tool, start the movie in VLC and go to View -> Subtitles and then you can search the subtitle from there easily. Also, there is a upload feature though I've not checked it.
2) Totem: Totem is my another favourite player for being simple and quite fast. This one even does not need any extra plugin/extension to be downloaded. The subtitle downloader plugin is already there within the player but most of us don't know that it is available. To use the plugin, just activate it from the Edit -> Plugins and then just go to View -> Subtitles -> Download Movie Subtitles.
If you are looking for some other alternatives, try splayer.
I hope this works well for you. :)
Read more...
Download Subtitles For Movies While Watching
2011-07-31T18:34:00+05:45
Cool Samar
linux|media player|video|windows|
Comments
Labels:
linux,
media player,
video,
windows
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Monday 25 July 2011
Wireshark 1.6.1 stable version released
The stable version of wireshark 1.6.1 has been released lately (July 18). Wireshark is the world's foremost network protocol analyzer. It lets you capture and interactively browse the traffic running on a computer network. It is the de facto standard across many industries and educational institutions.
To download wireshark, visit this link.
Read more...
To download wireshark, visit this link.
Read more...
Wireshark 1.6.1 stable version released
2011-07-25T21:00:00+05:45
Cool Samar
hacking|security|sniffer|wireshark|
Comments
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Virtual Box 4.1 Is Out
VirtualBox is a powerful x86 and AMD64/Intel64 virtualization product for enterprise as well as home use. Not only is VirtualBox an extremely feature rich, high performance product for enterprise customers, it is also the only professional solution that is freely available as Open Source Software under the terms of the GNU General Public License (GPL) version 2.
Oracle today released VirtualBox 4.1, a new major release. Introducing VM clones, increased capability for very large hosts, and Windows Aero support. You can view the Changelog in this version.
For downloads, check this link.
Read more...
Oracle today released VirtualBox 4.1, a new major release. Introducing VM clones, increased capability for very large hosts, and Windows Aero support. You can view the Changelog in this version.
For downloads, check this link.
Read more...
Virtual Box 4.1 Is Out
2011-07-25T20:47:00+05:45
Cool Samar
software|virtualbox|
Comments
Labels:
software,
virtualbox
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Tuesday 12 July 2011
Search Exploits & Vulnerability With Exploitsearch.net
The site, www.exploitsearch.net, is an attempt at cross referencing data from various sources and making the resulting database available to everyone.
Unlike other exploit search engines which are simply custom google searches, this site actually crawls the source sites and parses the contained data. Once the data is collected and parsed, it is inserted into the www.exploitsearch.net database and becomes available for searching.
www.exploitsearch.net
Currently utilizes data from NVD, OSVDB, SecurityFocus, Exploit-DB, Metasploit, Nessus, OpenVAS, and PacketStorm.Comes handy for better results. :)
Read more...
Unlike other exploit search engines which are simply custom google searches, this site actually crawls the source sites and parses the contained data. Once the data is collected and parsed, it is inserted into the www.exploitsearch.net database and becomes available for searching.
www.exploitsearch.net
Currently utilizes data from NVD, OSVDB, SecurityFocus, Exploit-DB, Metasploit, Nessus, OpenVAS, and PacketStorm.Comes handy for better results. :)
Read more...
Search Exploits & Vulnerability With Exploitsearch.net
2011-07-12T23:13:00+05:45
Cool Samar
hacking|security|useful website|
Comments
Labels:
hacking,
security,
useful website
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Thursday 30 June 2011
Mobius Forensic Toolkit 0.5.8 Is Out
Mobius Forensic Toolkit is a forensic framework written in Python/GTK that manages cases and case items, providing an abstract interface for developing extensions. Cases and item categories are defined using XML files for easy integration with other tools.
Changes: The Hive (registry viewer) features three new reports: email accounts, TCP/IP interfaces, and computer descriptions. All registry reports can be exported as CSV and the user password report can be exported in a format suitable for John the Ripper as well. Minor improvements were made.
For more information and downloads, visit the official link here.
Read more...
Changes: The Hive (registry viewer) features three new reports: email accounts, TCP/IP interfaces, and computer descriptions. All registry reports can be exported as CSV and the user password report can be exported in a format suitable for John the Ripper as well. Minor improvements were made.
For more information and downloads, visit the official link here.
Read more...
Mobius Forensic Toolkit 0.5.8 Is Out
2011-06-30T21:00:00+05:45
Cool Samar
forensic|security|
Comments
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Wednesday 29 June 2011
Ubuntu PPA Managing With PPABuilder
While reading stuffs on internet I came across this. You can manage your ubuntu PPA using the PPABuilder tool.
To install the tool, type the following commands from terminal:
The complete guide for this is available here.
Read more...
To install the tool, type the following commands from terminal:
sudo apt-add-repository ppa:lkjoel/ppabuilder
sudo apt-get update
sudo apt-get install ppabuilder
sudo apt-get update
sudo apt-get install ppabuilder
The complete guide for this is available here.
Read more...
Ubuntu PPA Managing With PPABuilder
2011-06-29T22:28:00+05:45
Cool Samar
software|ubuntu|
Comments
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Source Code Auditing With Graudit
Graudit is a simple script and signature sets that allows you to find potential security flaws in source code using the GNU utility grep. It's comparable to other static analysis applications like RATS, SWAAT and flaw-finder while keeping the technical requirements to a minimum and being very flexible.
The tool can be downloaded from HERE
Read more...
The tool can be downloaded from HERE
Read more...
Source Code Auditing With Graudit
2011-06-29T19:13:00+05:45
Cool Samar
security|software|
Comments
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Subscribe to:
Posts (Atom)