Showing posts with label security. Show all posts
Showing posts with label security. Show all posts
Friday 11 April 2014
Patching Your OpenShift Origin Against Heartbleed vulnerability
Recently the heartbleed bug was exposed which existed in all the services that used OpenSSL 1.0.1 through 1.0.1f (inclusive) for years already. This weakness allows stealing the information protected, under normal conditions, by the SSL/TLS encryption used to secure the Internet by reading the memory of the system without need of any kind of access.
I've been administering OpenShift applications recently and this post outlines the measures I took to secure the OpenShift applications from this critical vulnerability.
In order to check if you are vulnerable or not, you can either check OpenSSL version:
Alternatively, you can use one of the online tools or the offline python tool to check if you are vulnerable or not.
Note that in case of OpenShift origin, you will have to update the OpenSSL package in brokers and nodes such that all the OpenShift apps are secure.
Once completed, verify the installation of patched version:
We'll have to restart the proxy systems (node-proxy) for the nodes for the effect of the patch. In fact, we will have to restart all the services that use the vulnerable OpenSSL versions.
I hope this helps :)
Read more...
I've been administering OpenShift applications recently and this post outlines the measures I took to secure the OpenShift applications from this critical vulnerability.
In order to check if you are vulnerable or not, you can either check OpenSSL version:
# openssl version -a
OpenSSL 1.0.1e-fips 11 Feb 2013
built on: Wed Jan 8 07:20:55 UTC 2014
platform: linux-x86_64
OpenSSL 1.0.1e-fips 11 Feb 2013
built on: Wed Jan 8 07:20:55 UTC 2014
platform: linux-x86_64
Alternatively, you can use one of the online tools or the offline python tool to check if you are vulnerable or not.
Note that in case of OpenShift origin, you will have to update the OpenSSL package in brokers and nodes such that all the OpenShift apps are secure.
# yum install -y openssl
Once completed, verify the installation of patched version:
# openssl version -a
OpenSSL 1.0.1e-fips 11 Feb 2013
built on: Tue Apr 8 00:29:11 UTC 2014
platform: linux-x86_64
# rpm -q --changelog openssl | grep CVE-2014-0160
- pull in upstream patch for CVE-2014-0160
OpenSSL 1.0.1e-fips 11 Feb 2013
built on: Tue Apr 8 00:29:11 UTC 2014
platform: linux-x86_64
# rpm -q --changelog openssl | grep CVE-2014-0160
- pull in upstream patch for CVE-2014-0160
We'll have to restart the proxy systems (node-proxy) for the nodes for the effect of the patch. In fact, we will have to restart all the services that use the vulnerable OpenSSL versions.
# systemctl restart openshift-node-web-proxy.service
# /bin/systemctl reload httpd.service
# /bin/systemctl reload httpd.service
I hope this helps :)
Read more...
Patching Your OpenShift Origin Against Heartbleed vulnerability
2014-04-11T02:04:00+05:45
Cool Samar
fedora|heartbleed|openshift|openssl|security|
Comments
Labels:
fedora,
heartbleed,
openshift,
openssl,
security
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Friday 28 June 2013
Rename MySQL root User [How To]
MySQL ships with the default user 'root' who has all kind of access to the MySQL database. We often wish to rename this user to something else because of maybe security issues or any other reason. While renaming 'root' to something else is not going to alleviate all sorts of security problems that may arise, it is good idea to rename 'root' to some other name.
Login to the MySQL console and then type the following SQL statements:
It is often good idea to drop anonymous users and the test database because of security reasons. I bet you are never going to use that test database so why keep it? Run the SQL statements as below to do so:
Also, make sure you use strong passwords. You can use mysqladmin to change passwords.
The later two commands are to ensure that no log of any of your MySQL queries or admin level commands have been stored in the history.
I hope this helps :)
Read more...
Login to the MySQL console and then type the following SQL statements:
mysql> use mysql;
mysql> update user set user="some_other_user" where user="root";
mysql> flush privileges;
mysql> update user set user="some_other_user" where user="root";
mysql> flush privileges;
It is often good idea to drop anonymous users and the test database because of security reasons. I bet you are never going to use that test database so why keep it? Run the SQL statements as below to do so:
mysql> drop user "";
mysql> drop database test;
mysql> drop database test;
Also, make sure you use strong passwords. You can use mysqladmin to change passwords.
$ mysqladmin -u my_new_user -p password 's0m3_r4nd0m_$|r0ng_p455'
$ history -c
$ rm ~/.mysql_history
The later two commands are to ensure that no log of any of your MySQL queries or admin level commands have been stored in the history.
I hope this helps :)
Read more...
Rename MySQL root User [How To]
2013-06-28T10:37:00+05:45
Cool Samar
mysql|security|sysadmin|tricks and tips|
Comments
Labels:
mysql,
security,
sysadmin,
tricks and tips
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Tuesday 19 March 2013
How To View Your Gmail Access History Details
I do this thing on a regular basis to know if my account got compromised or not. Well I understand the risks imposed by logging in to my gmail account but still due to several circumstances, I have to login from public PCs. Though I employ some other techniques to trick possible keyloggers/RATs, etc. I do keep running from the dangers of account hijack and hence keep on regularly checking the account history details in gmail.
In order to access the gmail history log details, you need to scroll down to the right bottom of your gmail inbox where you will notice the option to view the detail of your account which looks like below:
Moreover, it seems like that the details now include the user agents and/or access type information along with the IP address and time of access to the gmail account.
If you're concerned about unauthorized access to your mail, you'll be able to use the data in the 'Access type' column to find out if and when someone accessed your mail. For instance, if the column shows any POP access, but you don't use POP to collect your mail, it may be a sign that your account has been compromised.
For more information, refer to this page.
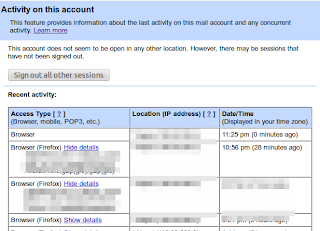
Moreover, this feature lets you log out all of your sessions other than the current session. This can come quite handy whenever you have forgotten to sign out or someone else is having an unauthorized access to your account.
Read more...
In order to access the gmail history log details, you need to scroll down to the right bottom of your gmail inbox where you will notice the option to view the detail of your account which looks like below:

Moreover, it seems like that the details now include the user agents and/or access type information along with the IP address and time of access to the gmail account.
If you're concerned about unauthorized access to your mail, you'll be able to use the data in the 'Access type' column to find out if and when someone accessed your mail. For instance, if the column shows any POP access, but you don't use POP to collect your mail, it may be a sign that your account has been compromised.
For more information, refer to this page.

Moreover, this feature lets you log out all of your sessions other than the current session. This can come quite handy whenever you have forgotten to sign out or someone else is having an unauthorized access to your account.
Read more...
How To View Your Gmail Access History Details
2013-03-19T23:38:00+05:45
Cool Samar
gmail|security|
Comments
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Friday 8 March 2013
Encrypt/Decrypt Confidential Data Using OpenSSL
If you wish to perform encrypted file transfers, openssl provides a robust implementation of SSL v2/3 and TLS v1 as well as full strength generic cryptographic functionalities. Available for almost every commonly used operating system, openssl can be used as a general purpose tool instead of looking for other specialized tools.
If you wish to have full strength cryptographic functions, openssl is a perfect choice. Forget about all other tools that promise to provide high end encryption for your confidential data. Openssl is more than enough for most of your cryptographic needs. Personally, I can't just rely on some random software that promises to provide full strength cryptography but lacks documentations and detailed reviews. Openssl, however, has a well structured documentation and is an open source implementation.
Openssl supports several ciphers such as AES, Blowfish, RC5, etc., several cryptographic hash functions such as MD5, SHA512, etc., and public key cryptographies such as RSA, DSA, etc. Openssl has been widely used in several softwares most notably the OpenSSH.
Now that we know some basics about what OpenSSL is, lets move on encrypting/decrypting files/data using openssl. OpenSSL can take any file and then apply one of the cryptographic functions to encrypt the file. As an example, we encrypt a confidential file 'priv8' with a password "hello" below:
In order to decrypt the encrypted file, we can run the following command:
Now that you know the basic syntax, you can choose among several available cryptographic functions. There are several other symmetric ciphers available for use. The full list of these ciphers is provided by the command:
I hope this helps for your file encryption needs :)
Read more...
If you wish to have full strength cryptographic functions, openssl is a perfect choice. Forget about all other tools that promise to provide high end encryption for your confidential data. Openssl is more than enough for most of your cryptographic needs. Personally, I can't just rely on some random software that promises to provide full strength cryptography but lacks documentations and detailed reviews. Openssl, however, has a well structured documentation and is an open source implementation.
Openssl supports several ciphers such as AES, Blowfish, RC5, etc., several cryptographic hash functions such as MD5, SHA512, etc., and public key cryptographies such as RSA, DSA, etc. Openssl has been widely used in several softwares most notably the OpenSSH.
Now that we know some basics about what OpenSSL is, lets move on encrypting/decrypting files/data using openssl. OpenSSL can take any file and then apply one of the cryptographic functions to encrypt the file. As an example, we encrypt a confidential file 'priv8' with a password "hello" below:
samar@Techgaun:~$ openssl aes-256-cbc -e -in priv8 -out priv8.enc -pass pass:hello
In order to decrypt the encrypted file, we can run the following command:
samar@Techgaun:~$ openssl aes-256-cbc -e -in priv8.enc -out priv8 -pass pass:hello
Now that you know the basic syntax, you can choose among several available cryptographic functions. There are several other symmetric ciphers available for use. The full list of these ciphers is provided by the command:
samar@Techgaun:~$ openssl list-cipher-algorithms
I hope this helps for your file encryption needs :)
Read more...
Encrypt/Decrypt Confidential Data Using OpenSSL
2013-03-08T22:10:00+05:45
Cool Samar
encryption|filesystem|security|
Comments
Labels:
encryption,
filesystem,
security
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Thursday 7 March 2013
Make An Encrypted Call On Android Using RedPhone
If you are quite worried about your privacy while making voice calls on your phone, RedPhone is a perfect tool to install in your android phone. RedPhone ensures that the eavesdropping attackers can not sniff your call by providing end-to-end encryption.
RedPhone is an open source communication encryption android software that well-integrates with the system dialer and lets you use the default system dialer and contacts apps to make calls as you normally would. The tool is written by Maxie Morlinspike, the same guy who wrote a famous tool called SSLStrip for performing HTTPS stripping attacks.

It is an open source tool licensed under GPL v3; the github README says, RedPhone is an application that enables encrypted voice communication between RedPhone users. RedPhone integrates with the system dialer to provide a frictionless call experience, but uses ZRTP to setup an encrypted VoIP channel for the actual call. RedPhone was designed specifically for mobile devices, using audio codecs and buffer algorithms tuned to the characteristics of mobile networks, and using push notifications to maximally preserve your device's battery life while still remaining responsive.
If you wish to understand more on Encryption protocol, you should refer to the WIKI.
Read more...
RedPhone is an open source communication encryption android software that well-integrates with the system dialer and lets you use the default system dialer and contacts apps to make calls as you normally would. The tool is written by Maxie Morlinspike, the same guy who wrote a famous tool called SSLStrip for performing HTTPS stripping attacks.
Install RedPhone
It is an open source tool licensed under GPL v3; the github README says, RedPhone is an application that enables encrypted voice communication between RedPhone users. RedPhone integrates with the system dialer to provide a frictionless call experience, but uses ZRTP to setup an encrypted VoIP channel for the actual call. RedPhone was designed specifically for mobile devices, using audio codecs and buffer algorithms tuned to the characteristics of mobile networks, and using push notifications to maximally preserve your device's battery life while still remaining responsive.
If you wish to understand more on Encryption protocol, you should refer to the WIKI.
Install RedPhone
Read more...
Make An Encrypted Call On Android Using RedPhone
2013-03-07T21:16:00+05:45
Cool Samar
android|mobile|security|web|
Comments
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Tuesday 12 February 2013
Chaining The Proxies With ProxyChains
In this tutorial, we will learn to redirect our TCP traffics through the chain of proxies using a well known tool named ProxyChains.
ProxyChains is a tool for tunneling TCP and DNS traffics through chain of several proxy servers which supports HTTP, SOCKS4, and SOCKS5 proxy servers. Hence, this tool leverages several usages such as anonymity, bypassing filters, running any program through proxy servers, etc.
You can DOWNLOAD proxychains from SourceForge. In ubuntu, you can directly install it from repos:
Once you have installed the proxychains, you need to configure this tool. The global configuration file is located at /etc/proxychains.conf so if you wish to have your own configuration file, you could either create the proxychains.conf file in the current working directory or at $HOME/.proxychains/proxychains.conf.
In my example, I'll edit the global configuration file by issuing the command:
First, we will have to select the kind of chaining option we want to use. We can use one of the dynamic_chain, strict_chain, and random_chain chaining options. In most cases, it is good to just use the dynamic_chain so we uncomment the line containing dynamic_chain and comment all other chaining options.
Then we need to grab some proxies and then insert at the end of our configuration file which would look like:
You could add as much as proxy servers in the list. Btw, the asterisks in the above example do not mean wildcards, they are just there to symbolize some proxy server. There are free sites on the Internet which provide big database of different kinds of proxies. Even several proxy scrapers are available all over the internet and you could even write one on your own. So getting list of good proxies is not the difficult job. Once you finish the configuration, you can run any command through proxychains. The syntax is as simple as below:
For example, below is the example nmap scan run through the proxychains:
P.S. If you are interested in some GUI for using proxychains, you can use ProxyChainsGUI. Lastly, the default package from Ubuntu repository seems to be missing the proxyresolv command so I would recommend to compile the source code locally.
Read more...
ProxyChains is a tool for tunneling TCP and DNS traffics through chain of several proxy servers which supports HTTP, SOCKS4, and SOCKS5 proxy servers. Hence, this tool leverages several usages such as anonymity, bypassing filters, running any program through proxy servers, etc.
You can DOWNLOAD proxychains from SourceForge. In ubuntu, you can directly install it from repos:
samar@samar-Techgaun:~$ sudo apt-get install proxychains
Once you have installed the proxychains, you need to configure this tool. The global configuration file is located at /etc/proxychains.conf so if you wish to have your own configuration file, you could either create the proxychains.conf file in the current working directory or at $HOME/.proxychains/proxychains.conf.
In my example, I'll edit the global configuration file by issuing the command:
samar@samar-Techgaun:~$ sudo nano /etc/proxychains.conf
First, we will have to select the kind of chaining option we want to use. We can use one of the dynamic_chain, strict_chain, and random_chain chaining options. In most cases, it is good to just use the dynamic_chain so we uncomment the line containing dynamic_chain and comment all other chaining options.
Then we need to grab some proxies and then insert at the end of our configuration file which would look like:
socks4 127.0.0.1 9050
socks5 192.168.2.90 3128
socks5 1**.1**.*.* 8080
socks5 192.168.2.90 3128
socks5 1**.1**.*.* 8080
You could add as much as proxy servers in the list. Btw, the asterisks in the above example do not mean wildcards, they are just there to symbolize some proxy server. There are free sites on the Internet which provide big database of different kinds of proxies. Even several proxy scrapers are available all over the internet and you could even write one on your own. So getting list of good proxies is not the difficult job. Once you finish the configuration, you can run any command through proxychains. The syntax is as simple as below:
samar@samar-Techgaun:~$ proxychains <any_command>
For example, below is the example nmap scan run through the proxychains:
samar@samar-Techgaun:~$ proxychains nmap -p 1-1000 -O victim.tld
P.S. If you are interested in some GUI for using proxychains, you can use ProxyChainsGUI. Lastly, the default package from Ubuntu repository seems to be missing the proxyresolv command so I would recommend to compile the source code locally.
Read more...
Chaining The Proxies With ProxyChains
2013-02-12T21:02:00+05:45
Cool Samar
anonymity|hacking|linux|security|
Comments
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Saturday 26 January 2013
Subterfuge - An Automated MITM Attack Framework
Subterfuge is a very useful tool for hackers and security experts for automating the man-in-the-middle attacks. It provides a complete framework for automating different kinds of MITM attacks.
Subterfuge largely transforms the complexity of performing the man-in-the-middle attacks with the tools such as ettercap and makes it far more easier to launch various form of MITMs. Hence, even a general computer user can perform MITM using this tool. Subterfuge provides a very clear interface accessible over HTTP through browser through which we can view the intercepted authentication data. The tool also supports several other form of MITM attacks such as session injection, http code injection, fake AP, and DNS spoofing.
Currently, the 4.3 beta version of this tool is available as the latest release. You can download the tool and read about the tool at code.google.com/p/subterfuge.
Installation is straightforward. Download the tar file from the above link and then run the following commands in terminal:
After a while, the installation will complete. Now you can run the subterfuge framework by typing subterfuge in your terminal. Enjoy hacking :)
Read more...
Subterfuge largely transforms the complexity of performing the man-in-the-middle attacks with the tools such as ettercap and makes it far more easier to launch various form of MITMs. Hence, even a general computer user can perform MITM using this tool. Subterfuge provides a very clear interface accessible over HTTP through browser through which we can view the intercepted authentication data. The tool also supports several other form of MITM attacks such as session injection, http code injection, fake AP, and DNS spoofing.
Currently, the 4.3 beta version of this tool is available as the latest release. You can download the tool and read about the tool at code.google.com/p/subterfuge.
Installation is straightforward. Download the tar file from the above link and then run the following commands in terminal:
samar@samar-Techgaun:~$ tar -xvf SubterfugePublicBeta4.3.tar.gz
samar@samar-Techgaun:~$ python install.py -i
After a while, the installation will complete. Now you can run the subterfuge framework by typing subterfuge in your terminal. Enjoy hacking :)
Read more...
Subterfuge - An Automated MITM Attack Framework
2013-01-26T00:39:00+05:45
Cool Samar
arp spoofing|hack tool|hacking|security|
Comments
Labels:
arp spoofing,
hack tool,
hacking,
security
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Friday 11 January 2013
Java 0-day In The Wild - Disable Java Plugin NOW
Security researchers have discovered yet another critical Java 0-day exploit being used by majority of the browser exploit packs such as Blackhole and Cool. Users are urged to DISABLE the Java plugin RIGHT NOW.
French researcher Kaffeine discovered that the java 0-day has been spotted to be making big hits daily, in a blog post. This particular exploit has proven to be very serious threat for the users. The folks at AlienVault Lab have also reproduced the exploit and it seems to work over all the java versions across all platforms which is a very serious threat.
As for now, the users are highly urged to disable their JAVA plugins right now so that they do not get hit by these 0-days.
So what are you waiting for?
How To Disable Java Plugin
Kaffeine's blog post
Alien Vault Labs Post
Read more...
French researcher Kaffeine discovered that the java 0-day has been spotted to be making big hits daily, in a blog post. This particular exploit has proven to be very serious threat for the users. The folks at AlienVault Lab have also reproduced the exploit and it seems to work over all the java versions across all platforms which is a very serious threat.
As for now, the users are highly urged to disable their JAVA plugins right now so that they do not get hit by these 0-days.
So what are you waiting for?
Important links:
How To Disable Java Plugin
Kaffeine's blog post
Alien Vault Labs Post
Read more...
Java 0-day In The Wild - Disable Java Plugin NOW
2013-01-11T20:33:00+05:45
Cool Samar
hacking|internet|news|security|web|
Comments
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Tuesday 11 December 2012
Inj3ct0r Team Hacked ExploitHub, Stole Private Exploits Worth $242333
Inj3ct0r team, which provides the ultimate database of exploits and vulnerabilities and serves as a great resource for vulnerability researchers and security professionals, has hacked ExploitHub.com, the site similar to inj3ct0r and stolen several private exploits worth $242333.
In the post from inj3ct0r team, they have provided the details for motivation of hack and the process of hack. At the time of writing this, ExploitHub.com seems to be down.
The post gives the process to accomplish the hack as below: I am very much surprised when he learned of Magento eCommerce Software and search /install/ 1) We scan server and site 2) We reinstall Magento CMS https://www.exploithub.com/install/ <= We reinstall Magento CMS 3) Upload shell and phpinfo https://www.exploithub.com/phpinfo.php 4) Back all files and database. 5) Upload piece of the database https://www.exploithub.com/export/ 6) Increased privileges
Read more...
In the post from inj3ct0r team, they have provided the details for motivation of hack and the process of hack. At the time of writing this, ExploitHub.com seems to be down.
The post gives the process to accomplish the hack as below: I am very much surprised when he learned of Magento eCommerce Software and search /install/ 1) We scan server and site 2) We reinstall Magento CMS https://www.exploithub.com/install/ <= We reinstall Magento CMS 3) Upload shell and phpinfo https://www.exploithub.com/phpinfo.php 4) Back all files and database. 5) Upload piece of the database https://www.exploithub.com/export/ 6) Increased privileges
Read more...
Inj3ct0r Team Hacked ExploitHub, Stole Private Exploits Worth $242333
2012-12-11T23:18:00+05:45
Cool Samar
hacking|internet|news|security|
Comments
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Saturday 8 December 2012
DNS Rebinding Attack Using Rebind
Rebind is a tool that implements the multiple A record DNS rebinding attack. Although this tool was originally written to target home routers, it can be used to target any public (non RFC1918) IP address.
Rebind provides an external attacker access to a target router's internal Web interface. This tool works on routers that implement the weak end system model in their IP stack, have specifically configured firewall rules, and who bind their Web service to the router's WAN interface. Note that remote administration does not need to be enabled for this attack to work. All that is required is that a user inside the target network surf to a Web site that is controlled, or has been compromised, by the attacker.
Download rebind
Tested Routers (Affected + Not affected)
Rebind FAQ
Defcon Slides
Kind of interesting vector and I guess many are vulnerable out there.
Read more...
Rebind provides an external attacker access to a target router's internal Web interface. This tool works on routers that implement the weak end system model in their IP stack, have specifically configured firewall rules, and who bind their Web service to the router's WAN interface. Note that remote administration does not need to be enabled for this attack to work. All that is required is that a user inside the target network surf to a Web site that is controlled, or has been compromised, by the attacker.
Important Links
Download rebind
Tested Routers (Affected + Not affected)
Rebind FAQ
Defcon Slides
Kind of interesting vector and I guess many are vulnerable out there.
Read more...
DNS Rebinding Attack Using Rebind
2012-12-08T23:45:00+05:45
Cool Samar
hack tool|hacking|router|security|security bypass|software|web|
Comments
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Friday 30 November 2012
Nmap 6.25 Holiday Season Released
After five months of the release of NMAP 6.01, a newer version 6.25 has been released yesterday.
Nmap 6.25 contains hundreds of improvements, including 85 new NSE scripts, nearly 1,000 new OS and service detection fingerprints, performance enhancements such as the new kqueue and poll I/O engines, better IPv6 traceroute support, Windows 8 improvements, and much more! It also includes the work of five Google Summer of Code interns who worked full time with Nmap mentors during the summer.
Nmap 6.25 source code and binary packages for Linux, Windows, and Mac are available for free download from:
http://nmap.org/download.html
Release details
Read more...
Nmap 6.25 contains hundreds of improvements, including 85 new NSE scripts, nearly 1,000 new OS and service detection fingerprints, performance enhancements such as the new kqueue and poll I/O engines, better IPv6 traceroute support, Windows 8 improvements, and much more! It also includes the work of five Google Summer of Code interns who worked full time with Nmap mentors during the summer.
Nmap 6.25 source code and binary packages for Linux, Windows, and Mac are available for free download from:
http://nmap.org/download.html
Release details
Read more...
Nmap 6.25 Holiday Season Released
2012-11-30T17:45:00+05:45
Cool Samar
hack tool|hacking|network|nmap|security|
Comments
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Monday 19 November 2012
PHP 5.5 To Include Simple And Secure Password Hashing API
Few days ago, we saw the release of PHP 5.5.0 Alpha 1 to the public. The PHP development team is serious about addressing all the criticism it gets time and again. With the recent leaks of several high profile sites, a simple to use yet secure password hashing API has been introduced now.
Here's the RFC for simple password hashing API proposed by ircmaxell and now it has been implemented as a PHP core in 5.5.0 Alpha 1 release and will continue to be part of the PHP core in future releases.
In case you would like to use the API functions in older releases, there's a compatible PHP library for PHP >= 5.3.7. The reason for this is that PHP prior to 5.3.7 contains a security issue with its BCRYPT implementation.
Basically the idea behind simple password hashing API is that most of the PHP developers either don't understand or don't think worth the effort the whole concept of strong password hashing. By providing a simple API that can be called, which takes care of all of those issues for you, hopefully more projects and developers will be able to use secure password hashing.
Using the API is quite simple. All you have to do to get the hash is:
Verifying the password is also quite simple.
The simple password hashing API provides sets of password_* functions for the developers to make use of strong password hashing.
RFC for simple password hashing API
Designing an API
PHP 5.5.0 Alpha 1 released
Read more...
Here's the RFC for simple password hashing API proposed by ircmaxell and now it has been implemented as a PHP core in 5.5.0 Alpha 1 release and will continue to be part of the PHP core in future releases.
In case you would like to use the API functions in older releases, there's a compatible PHP library for PHP >= 5.3.7. The reason for this is that PHP prior to 5.3.7 contains a security issue with its BCRYPT implementation.
Basically the idea behind simple password hashing API is that most of the PHP developers either don't understand or don't think worth the effort the whole concept of strong password hashing. By providing a simple API that can be called, which takes care of all of those issues for you, hopefully more projects and developers will be able to use secure password hashing.
Using the API is quite simple. All you have to do to get the hash is:
$hash = password_hash($password, PASSWORD_BCRYPT);
Verifying the password is also quite simple.
if (password_verify($password, $hash)) {
// pass is correct :)
} else {
// pass is correct :/
}
The simple password hashing API provides sets of password_* functions for the developers to make use of strong password hashing.
Reading materials
RFC for simple password hashing API
Designing an API
PHP 5.5.0 Alpha 1 released
Read more...
PHP 5.5 To Include Simple And Secure Password Hashing API
2012-11-19T14:49:00+05:45
Cool Samar
development|hashing|password hacking|php|programming|security|web|
Comments
Labels:
development,
hashing,
password hacking,
php,
programming,
security,
web
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Sunday 28 October 2012
Think Like A Hacker For Better Security Awareness
52% of businesses experienced more malware infections as a result of employees on social media. This whitepaper provides an insight on how to think like a hacker for better security awareness.
Security awareness is mostly about common sense, and thinking like the hackers to understand what security weaknesses they look for. But like other security precautions, it's easy to let down your guard.
Security awareness education can arm your staff with the skills to practice safe Internet usage - to reduce malware and other cyber threats. The whitepaper entitled Takes One to Know One: Think Like a Hacker for Better Security Awareness is a must read for making yourself aware of security in this digital world.
In this paper, find out:
Read more...
Security awareness is mostly about common sense, and thinking like the hackers to understand what security weaknesses they look for. But like other security precautions, it's easy to let down your guard.
Security awareness education can arm your staff with the skills to practice safe Internet usage - to reduce malware and other cyber threats. The whitepaper entitled Takes One to Know One: Think Like a Hacker for Better Security Awareness is a must read for making yourself aware of security in this digital world.
In this paper, find out:
- Best ways to deliver a security awareness program
- What you should teach your staff
- How to make security awareness a priority
Download The Whitepaper
Read more...
Think Like A Hacker For Better Security Awareness
2012-10-28T14:02:00+05:45
Cool Samar
ebook|hacking|security|
Comments
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Wednesday 12 September 2012
Disable Guest Account Login In Ubuntu 12.04
Security is an important issue and I do not want anyone to access my machine, not even as the guest. Like almost every operating systems, I could see guest logon option in Ubuntu 12.04 which was turned on by default. This post provides the steps to enable or disable the guest account login in Ubuntu 12.04.
Fire up your terminal and type the following command:
Now add a new line at the end containing the string as below:
Now reboot your system or type the following in your terminal:
The guest account will no longer be active. If you want to enable the guest login again, just remove the line you added or change the value to true. I hope this helps :)
Read more...
Fire up your terminal and type the following command:
samar@samar-Techgaun:~$ sudo nano /etc/lightdm/lightdm.conf
Now add a new line at the end containing the string as below:
allow-guest=false
Now reboot your system or type the following in your terminal:
samar@samar-Techgaun:~$ sudo /etc/init.d/lightdm restart
The guest account will no longer be active. If you want to enable the guest login again, just remove the line you added or change the value to true. I hope this helps :)
Read more...
Disable Guest Account Login In Ubuntu 12.04
2012-09-12T11:18:00+05:45
Cool Samar
lightdm|security|tricks and tips|ubuntu 12.04|
Comments
Labels:
lightdm,
security,
tricks and tips,
ubuntu 12.04
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Tuesday 28 August 2012
Hack Attack The Networks With Yersinia
Yersinia is a network attack tool that takes advantages of inherent weaknesses of several protocols to attack the network using different attack vectors. Yersinia can prove as a solid tool for analyzing and testing the deployed networks and systems for possible weaknesses.
The protocols implemented for testing using Yersinia are:
Yersinia supports number of attacks in all of the above listed network protocols and hence can be used (or misused) to test any network.
The tool works on several operating systems such as OpenBSD 3.4 (with pcap libraries >= 0.7.2), Linux 2.4.x and 2.6.x, Solaris 5.8 64bits SPARC, Mac OSX 10.4 Tiger (Intel), etc.
Installation on ubuntu: Fire up the terminal and type:
To download yersinia for other distros, go through the Download section of yersinia.
Read more...
The protocols implemented for testing using Yersinia are:
- Spanning Tree Protocol (STP)
- Cisco Discovery Protocol (CDP)
- Dynamic Trunking Protocol (DTP)
- Dynamic Host Configuration Protocol (DHCP)
- Hot Standby Router Protocol (HSRP)
- IEEE 802.1Q
- IEEE 802.1X
- Inter-Switch Link Protocol (ISL)
- VLAN Trunking Protocol (VTP)
Yersinia supports number of attacks in all of the above listed network protocols and hence can be used (or misused) to test any network.
The tool works on several operating systems such as OpenBSD 3.4 (with pcap libraries >= 0.7.2), Linux 2.4.x and 2.6.x, Solaris 5.8 64bits SPARC, Mac OSX 10.4 Tiger (Intel), etc.
Installation on ubuntu: Fire up the terminal and type:
sudo apt-get install yersinia
To download yersinia for other distros, go through the Download section of yersinia.
Read more...
Hack Attack The Networks With Yersinia
2012-08-28T00:09:00+05:45
Cool Samar
hack tool|hacking|network|security|software|
Comments
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Sunday 3 June 2012
Check Your Plugins To Keep Firefox Updated and Safe
Mozilla foundation is now providing an online tool to check if the plugins you've installed are up to date or not using simple interface. The objective of this service is to keep your third-party plugins up to date which helps Firefox run safely and smoothly.
The service lets you check all the plugins and update the outdated ones from a simple UI in two major steps:
Step 1: Click Update to update a plugin.
Step 2: Complete all recommended updates before restarting your browser.
Head on to Firefox Browser Plugin Check & Updates.
Stay safe :)
Read more...
The service lets you check all the plugins and update the outdated ones from a simple UI in two major steps:
Step 1: Click Update to update a plugin.
Step 2: Complete all recommended updates before restarting your browser.
Head on to Firefox Browser Plugin Check & Updates.
Stay safe :)
Read more...
Check Your Plugins To Keep Firefox Updated and Safe
2012-06-03T21:58:00+05:45
Cool Samar
browser|mozilla firefox|security|tricks and tips|web|
Comments
Labels:
browser,
mozilla firefox,
security,
tricks and tips,
web
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Thursday 31 May 2012
JSUnpack - A Generic Javascript Unpacker
JSUnpack is an online service that can unpack different kinds of obfuscated and packed javascript source codes. It is designed for security researchers and computer professionals.
You can either supply the source code or link to the javascript file to unpack it. The site also supports uploading and unpacking of PDF, pcap, HTML, or JavaScript file.
JSUNPACK website
I hope it comes handy to you as it did to me. :)
Read more...
You can either supply the source code or link to the javascript file to unpack it. The site also supports uploading and unpacking of PDF, pcap, HTML, or JavaScript file.
JSUNPACK website
I hope it comes handy to you as it did to me. :)
Read more...
JSUnpack - A Generic Javascript Unpacker
2012-05-31T19:21:00+05:45
Cool Samar
damn vulnerable web application|hacking|javascript|security|unpacker|
Comments
Labels:
damn vulnerable web application,
hacking,
javascript,
security,
unpacker
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Tuesday 22 May 2012
NMAP 6 Released
Version 6 of nmap, one of the most widely used network exploration and security auditing tool was released on 21 May. Nmap (“Network Mapper”) is a free and open source (license) utility for network discovery and security auditing.
The nmap site says:
"The Nmap Project is pleased to announce the immediate, free availability of the Nmap Security Scanner version 6.00 from http://nmap.org/. It is the product of almost three years of work, 3,924 code commits, and more than a dozen point releases since the big Nmap 5 release in July 2009. Nmap 6 includes a more powerful Nmap Scripting Engine, 289 new scripts, better web scanning, full IPv6 support, the Nping packet prober, faster scans, and much more! We recommend that all current users upgrade."
The new version of nmap consists of 6 major improvements among several changes. Enhanced Nmap scripting engine(NSE), better web scanning, full-fledged IPv6 support, addition of nping tool, better zenmap GUI and faster scanning are the enhancements seen in the version 6 of nmap.
More Release Information
Download NMAP
Read more...
The nmap site says:
"The Nmap Project is pleased to announce the immediate, free availability of the Nmap Security Scanner version 6.00 from http://nmap.org/. It is the product of almost three years of work, 3,924 code commits, and more than a dozen point releases since the big Nmap 5 release in July 2009. Nmap 6 includes a more powerful Nmap Scripting Engine, 289 new scripts, better web scanning, full IPv6 support, the Nping packet prober, faster scans, and much more! We recommend that all current users upgrade."
The new version of nmap consists of 6 major improvements among several changes. Enhanced Nmap scripting engine(NSE), better web scanning, full-fledged IPv6 support, addition of nping tool, better zenmap GUI and faster scanning are the enhancements seen in the version 6 of nmap.
More Release Information
Download NMAP
Read more...
NMAP 6 Released
2012-05-22T16:54:00+05:45
Cool Samar
hack tool|hacking|network|nmap|security|
Comments
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Tuesday 20 March 2012
Some Fun With Alternate Data Streams
I have not been blogging for a while because of exams but now I'm free for few days so here comes another post back from my home village. This time, I'm going to share some basic funs with alternate data streams from theory to some practical stuffs.
What is Alternate Data Stream Alternate Data Stream(ADS) is a kind of file system fork which allows more than one data stream to be associated with a single filename. Alternate Data Stream was introduced by Microsoft as a part of its NTFS file system. Alternate Data Streams are not shown by Windows Explorer and even the dir command and size of ADS is also excluded from the file size. The dir command however allows us to view the alternate data streams using the dir /R command in Windows Vista and above.
One use of ADS could be hiding the information as alternate data streams in the file but beware that copying the file to non-NTFS file systems will make you loose the information in the ADS. ADS was originally introduced to store file information and properties however any user can hide any kind of information in the ADS. Some malwares have utilized the ADS to hide their code so most antiviruses today also scan the ADS of any file to find anything fishy.
Note that the format used to create(and access) ADS is filename:ADSname. A relatively simple guide I had written a while ago is HERE.
Now lets move on to some interesting stuffs and for that, I am creating a directory named "samar" in Desktop. We will first create a simple text file by using the command below:
Now lets add an alternate data stream by issuing the following command:
Lets issue the dir command to see what it lists:
We can see no information regarding the alternate data stream we just added to the file and lets see if the type command shows anything by just opening the file.
So where is the private stuff we've put as ADS in the file? Even viewing the file from windows explorer does not show the content in ADS and of course the size is also not included. The point here is the malicious user might add something bad in the alternate data stream and send to a normal PC user. The unsuspecting user will not know if there's anything other than just the text file. Now lets see how we can see the alternate data stream.
For a while, lets pretend that we don't know that the ADS is added in the file. So first we will use the commands to see if there's any ADS in the file. The simplest one is to use dir /R command as below:
We can see that besides the ads.txt file, there is another entry ads.txt:private:$DATA. By examining this file, we come to know that the alternate data stream with the name private is present in the file ads.txt and the alternate data stream is nothing but just the data. However, as stated earlier, only Vista and above contain the dir command that lets us list the alternate data streams. In such case, you can download a small utility named streams from Microsoft Technet. The streams tool also allows us to delete the ADS easily which is possible but a bit obscure for normal PC user. Now to view the content of the alternate data stream, we will use notepad:
Note that this time we didn't use type command since it does not support the use of colon in the command. We used the notepad but we could also use another command known as more as below:
The fun with ADS just does not stop here. We could do much more than this but the basic idea is same. We can embed executables and codes within the ADS and run those executable whenever necessary. I'll leave this as homework for you guys since it won't be hard to figure it out once you've understood the basics I've discussed above.
The alternate data stream has already been exploited in IIS, the primary web server from Microsoft. Following is the example I've taken from OWASP on how it could be exploited in IIS.
Normal access:
http://www.alternate-data-streams.com/default.asp Show code bypass accessing the :$DATA alternate data stream:
http://www.alternate-data-streams.com/default.asp::$DATA
Last thing I would like to discuss is how to delete the alternate data streams. The streamers tool provides a -d switch to delete the ADS and it also supports the wildcards for deleting the streams. Another way of deleting the alternate streams is to copy the file in non-NTFS drives such as to FAT32-formatted pendrives and then copying back. Of course, you could also save the content of main stream in another file and then delete the original file that consists of stream.
I hope this helps you. Please let me know if I should add something to it. :)
Read more...
What is Alternate Data Stream Alternate Data Stream(ADS) is a kind of file system fork which allows more than one data stream to be associated with a single filename. Alternate Data Stream was introduced by Microsoft as a part of its NTFS file system. Alternate Data Streams are not shown by Windows Explorer and even the dir command and size of ADS is also excluded from the file size. The dir command however allows us to view the alternate data streams using the dir /R command in Windows Vista and above.
One use of ADS could be hiding the information as alternate data streams in the file but beware that copying the file to non-NTFS file systems will make you loose the information in the ADS. ADS was originally introduced to store file information and properties however any user can hide any kind of information in the ADS. Some malwares have utilized the ADS to hide their code so most antiviruses today also scan the ADS of any file to find anything fishy.
Note that the format used to create(and access) ADS is filename:ADSname. A relatively simple guide I had written a while ago is HERE.
Now lets move on to some interesting stuffs and for that, I am creating a directory named "samar" in Desktop. We will first create a simple text file by using the command below:
echo An ordinary text file > ads.txt
Now lets add an alternate data stream by issuing the following command:
echo I am secret > ads.txt:private.txt
Lets issue the dir command to see what it lists:
Volume in drive C has no label.
Volume Serial Number is 90E7-CBCA
Directory of C:\Users\SINDHUS\Desktop\samar
03/20/2012 09:58 AM <DIR> .
03/20/2012 09:58 AM <DIR> ..
03/20/2012 09:56 AM 24 ads.txt
3 File(s) 24 bytes
3 Dir(s) 22,683,332,608 bytes free
We can see no information regarding the alternate data stream we just added to the file and lets see if the type command shows anything by just opening the file.
C:\Users\SINDHUS\Desktop\samar>type ads.txt
An ordinary text file
An ordinary text file
So where is the private stuff we've put as ADS in the file? Even viewing the file from windows explorer does not show the content in ADS and of course the size is also not included. The point here is the malicious user might add something bad in the alternate data stream and send to a normal PC user. The unsuspecting user will not know if there's anything other than just the text file. Now lets see how we can see the alternate data stream.
For a while, lets pretend that we don't know that the ADS is added in the file. So first we will use the commands to see if there's any ADS in the file. The simplest one is to use dir /R command as below:
C:\Users\SINDHU'S\Desktop\samar>dir /R
Volume in drive C has no label.
Volume Serial Number is 90E7-CBCA
Directory of C:\Users\SINDHU'S\Desktop\samar
03/20/2012 09:58 AM <DIR> .
03/20/2012 09:58 AM <DIR> ..
03/20/2012 09:56 AM 24 ads.txt
14 ads.txt:private.txt:$DATA
03/20/2012 09:58 AM 496 info.txt
2 File(s) 520 bytes
3 Dir(s) 22,881,669,120 bytes free
We can see that besides the ads.txt file, there is another entry ads.txt:private:$DATA. By examining this file, we come to know that the alternate data stream with the name private is present in the file ads.txt and the alternate data stream is nothing but just the data. However, as stated earlier, only Vista and above contain the dir command that lets us list the alternate data streams. In such case, you can download a small utility named streams from Microsoft Technet. The streams tool also allows us to delete the ADS easily which is possible but a bit obscure for normal PC user. Now to view the content of the alternate data stream, we will use notepad:
C:\Users\SINDHUS\Desktop\samar>notepad ads.txt:private.txt
Note that this time we didn't use type command since it does not support the use of colon in the command. We used the notepad but we could also use another command known as more as below:
C:\Users\SINDHU'S\Desktop\samar>more < ads.txt:private
I am secret
I am secret
The fun with ADS just does not stop here. We could do much more than this but the basic idea is same. We can embed executables and codes within the ADS and run those executable whenever necessary. I'll leave this as homework for you guys since it won't be hard to figure it out once you've understood the basics I've discussed above.
The alternate data stream has already been exploited in IIS, the primary web server from Microsoft. Following is the example I've taken from OWASP on how it could be exploited in IIS.
Normal access:
http://www.alternate-data-streams.com/default.asp Show code bypass accessing the :$DATA alternate data stream:
http://www.alternate-data-streams.com/default.asp::$DATA
Last thing I would like to discuss is how to delete the alternate data streams. The streamers tool provides a -d switch to delete the ADS and it also supports the wildcards for deleting the streams. Another way of deleting the alternate streams is to copy the file in non-NTFS drives such as to FAT32-formatted pendrives and then copying back. Of course, you could also save the content of main stream in another file and then delete the original file that consists of stream.
I hope this helps you. Please let me know if I should add something to it. :)
Read more...
Some Fun With Alternate Data Streams
2012-03-20T19:08:00+05:45
Cool Samar
alternate data stream|hacking|security|tricks and tips|windows|
Comments
Labels:
alternate data stream,
hacking,
security,
tricks and tips,
windows
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Tuesday 28 February 2012
List of Hashing Algorithms Used In Major CMS & Forums
Just found this random image from one digital friend and its a pretty good list of hashing algorithms used in many web based applications such as CMS and forum softwares. Some of these algorithms might get outdated with newer versions, but still it will be a good reference.
View Full Size Image
Note for creator: If you are the owner of this image, please let me know so that I can give you the credit.
Read more...
View Full Size Image
Note for creator: If you are the owner of this image, please let me know so that I can give you the credit.
Read more...
List of Hashing Algorithms Used In Major CMS & Forums
2012-02-28T01:53:00+05:45
Cool Samar
encryption|hacking|password hacking|security|
Comments
Labels:
encryption,
hacking,
password hacking,
security
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Subscribe to:
Posts (Atom)

