Showing posts with label tricks and tips. Show all posts
Showing posts with label tricks and tips. Show all posts
Friday 6 July 2012
Fix "trying to overwrite '*', which is also in package *"
Today I was updating few stuffs in edubuntu and dpkg was continually throwing me the problem while trying to install kdelibs-data. The error read as "trying to overwrite 'A', which is also in package X" and the fix was pretty straightforward but still I thought it would help someone out there.
Below is the exact error I was getting while trying to install kdelibs5-data from the deb file.
The fix was pretty simple. Add the --force-overwrite switch in the dpkg command as below:
I hope this comes useful sometimes.
Read more...
Below is the exact error I was getting while trying to install kdelibs5-data from the deb file.
dpkg: error processing /var/cache/apt/archives/
kdelibs5-data_4%3a4.4.5-0ubuntu1.2_all.deb (--unpack):
trying to overwrite '/usr/share/polkit-1/actions
/org.kde.kcontrol.kcmremotewidgets.policy', which is also in package kdebase-runtime-data 4:4.6.5-0ubuntu1
kdelibs5-data_4%3a4.4.5-0ubuntu1.2_all.deb (--unpack):
trying to overwrite '/usr/share/polkit-1/actions
/org.kde.kcontrol.kcmremotewidgets.policy', which is also in package kdebase-runtime-data 4:4.6.5-0ubuntu1
The fix was pretty simple. Add the --force-overwrite switch in the dpkg command as below:
dpkg -i --force-overwrite kdelibs5-data_4.4.5-0ubuntu1.2_all.deb
I hope this comes useful sometimes.
Read more...
Fix "trying to overwrite '*', which is also in package *"
2012-07-06T17:34:00+05:45
Cool Samar
command line|edubuntu|linux|ltsp|tricks and tips|ubuntu|ubuntu 11.10|
Comments
Labels:
command line,
edubuntu,
linux,
ltsp,
tricks and tips,
ubuntu,
ubuntu 11.10
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Friday 15 June 2012
How To Enable Use Of Htaccess In Apache In Ubuntu
This How To provides a detail on how to enable use of .htaccess file in apache in ubuntu and the similar flavors of linux distribution.
To enable use of .htaccess, you can edit the /etc/apache2/sites-available/default file. Search for the portion which contains the following lines or something similar to that(The bold line is almost always present):
All you have to do is change the bold line above to:
Now you will need to restart the apache service so that the effect of change in configuration takes place. Enter the following command to restart the apache service:
Now your .htaccess files will start to work in ubuntu. :)
Read more...
To enable use of .htaccess, you can edit the /etc/apache2/sites-available/default file. Search for the portion which contains the following lines or something similar to that(The bold line is almost always present):
<Directory /var/www/>
Options Indexes FollowSymLinks MultiViews
AllowOverride None
Order allow,deny
allow from all
</Directory>
Options Indexes FollowSymLinks MultiViews
AllowOverride None
Order allow,deny
allow from all
</Directory>
All you have to do is change the bold line above to:
<Directory /var/www/>
Options Indexes FollowSymLinks MultiViews
AllowOverride All
Order allow,deny
allow from all
</Directory>
Options Indexes FollowSymLinks MultiViews
AllowOverride All
Order allow,deny
allow from all
</Directory>
Now you will need to restart the apache service so that the effect of change in configuration takes place. Enter the following command to restart the apache service:
samar@Techgaun:~$ sudo service apache2 reload
Now your .htaccess files will start to work in ubuntu. :)
Read more...
How To Enable Use Of Htaccess In Apache In Ubuntu
2012-06-15T21:53:00+05:45
Cool Samar
htaccess|linux|tricks and tips|ubuntu|
Comments
Labels:
htaccess,
linux,
tricks and tips,
ubuntu
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Monday 11 June 2012
Graphical Frontends To Sopcast Client For Linux
As all of you know the official Sopcast client for linux is only the command line version and many people find it difficult to use the CLI version. However, many good people have made an effort to write the graphical frontends to the Sopcast client for linux. Here you will find some of such GUI frontends for sopcast.
Sopcast Player: SopCast Player is designed to be an easy to use Linux GUI front-end for the p2p streaming technology developed by SopCast. SopCast Player features an integrated video player, a channel guide, and bookmarks. Once SopCast Player is installed it simply "just works" with no required configuration.
qsopcast: qsopcast is a QT GUI front-end of the Linux command line executive of P2P TV sopcast.
gsopcast: gsopcast is a GTK based GUI front-end for p2p TV sopcast.
TV-Maxe: TV-MAXE is an application which provides the ability to watch TV stations and listen radio via different streams, such is SopCast. Currently it has a large number of channels, both romanian and international.
SCPlayer: SCPlayer is a simple and lightweight GUI frontend for sopcast supporting only linux GNOME3 platform.
Pysopcast: It is a simple GUI for sopcast made using PyGTK.
totem-sopcast: A totem plugin to let you browse and play sopcast streams.
wxsopcast: A sopcast GUI for linux written in python and wxPython. Note that the channel URL needs to be changed to http://www.sopcast.com/gchlxml at first.
jsopcast: jsopcast is a simple GUI to see P2P TV sopcast made in Java.
If you know of any other GUI frontend for sopcast, please feel free to leave a comment. :)
Read more...
Sopcast Player: SopCast Player is designed to be an easy to use Linux GUI front-end for the p2p streaming technology developed by SopCast. SopCast Player features an integrated video player, a channel guide, and bookmarks. Once SopCast Player is installed it simply "just works" with no required configuration.
qsopcast: qsopcast is a QT GUI front-end of the Linux command line executive of P2P TV sopcast.
gsopcast: gsopcast is a GTK based GUI front-end for p2p TV sopcast.
TV-Maxe: TV-MAXE is an application which provides the ability to watch TV stations and listen radio via different streams, such is SopCast. Currently it has a large number of channels, both romanian and international.
SCPlayer: SCPlayer is a simple and lightweight GUI frontend for sopcast supporting only linux GNOME3 platform.
Pysopcast: It is a simple GUI for sopcast made using PyGTK.
totem-sopcast: A totem plugin to let you browse and play sopcast streams.
wxsopcast: A sopcast GUI for linux written in python and wxPython. Note that the channel URL needs to be changed to http://www.sopcast.com/gchlxml at first.
jsopcast: jsopcast is a simple GUI to see P2P TV sopcast made in Java.
If you know of any other GUI frontend for sopcast, please feel free to leave a comment. :)
Read more...
Graphical Frontends To Sopcast Client For Linux
2012-06-11T01:04:00+05:45
Cool Samar
fedora|linux|sopcast|tricks and tips|ubuntu|ubuntu 11.10|
Comments
Labels:
fedora,
linux,
sopcast,
tricks and tips,
ubuntu,
ubuntu 11.10
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Download Full Package Of Winetricks And Fonts To Remove Checksum Mismatch Error
While trying to install allfonts from winetricks, I got a sha checksum mismatch error and soon I started fixing them manually. In order to make it easier for the wine users out there, I've slightly edited(changed the sha checksums) the winetricks file and packaged the font files.
You can download the package from HERE.
After downloading the file, unzip the file and then copy winetricks to /usr/bin/winetricks as below:
Now copy all the fcontents of dotcache/winetricks directory to ~/.cache/winetricks/
Now re-run the winetricks and install the allfonts. This time, you'll not get any error. I hope this helps :)
Read more...
You can download the package from HERE.
After downloading the file, unzip the file and then copy winetricks to /usr/bin/winetricks as below:
cp -f winetricks /usr/bin/winetricks
Now copy all the fcontents of dotcache/winetricks directory to ~/.cache/winetricks/
Now re-run the winetricks and install the allfonts. This time, you'll not get any error. I hope this helps :)
Read more...
Download Full Package Of Winetricks And Fonts To Remove Checksum Mismatch Error
2012-06-11T00:22:00+05:45
Cool Samar
tricks and tips|wine|winetricks|
Comments
Labels:
tricks and tips,
wine,
winetricks
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Saturday 9 June 2012
How To Undo Sent Mail In Gmail
This is a how to on undoing the sent mail in gmail. However, this method has severe limitation at the time of writing this post since we are allowed to have maximum time of 30 seconds as a cancellation period but lets hope this gmail lab feature gets integrated in gmail with longer cancellation period.
Sometimes we send an e-mail to somebody and later realize that we should not have sent that particular e-mail. Though not so helpful, the "Undo Send" feature from Gmail Labs can be useful sometimes.
By default, you will not have Undo link after you just sent the message.
Click on the icon(see screenshot below) at the top left corner of your gmail interface and then click on Settings

Click on the Labs Tab and then in the lab search box, type Undo Send.
Now select the Enable radio button and then Save changes.
By default, the cancellation period is 10 seconds(at the time of writing). To change the default time to 30 seconds, again go to settings and in general tab, you will find the Cancellation period dropdown list. Choose any value you want.
Now you can undo the just sent emails as below:

Read more...
Sometimes we send an e-mail to somebody and later realize that we should not have sent that particular e-mail. Though not so helpful, the "Undo Send" feature from Gmail Labs can be useful sometimes.
By default, you will not have Undo link after you just sent the message.
Click on the icon(see screenshot below) at the top left corner of your gmail interface and then click on Settings
Click on the Labs Tab and then in the lab search box, type Undo Send.
Now select the Enable radio button and then Save changes.
By default, the cancellation period is 10 seconds(at the time of writing). To change the default time to 30 seconds, again go to settings and in general tab, you will find the Cancellation period dropdown list. Choose any value you want.
Now you can undo the just sent emails as below:
Read more...
How To Undo Sent Mail In Gmail
2012-06-09T00:15:00+05:45
Cool Samar
email|gmail|tricks and tips|
Comments
Labels:
email,
gmail,
tricks and tips
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Sunday 3 June 2012
Check Your Plugins To Keep Firefox Updated and Safe
Mozilla foundation is now providing an online tool to check if the plugins you've installed are up to date or not using simple interface. The objective of this service is to keep your third-party plugins up to date which helps Firefox run safely and smoothly.
The service lets you check all the plugins and update the outdated ones from a simple UI in two major steps:
Step 1: Click Update to update a plugin.
Step 2: Complete all recommended updates before restarting your browser.
Head on to Firefox Browser Plugin Check & Updates.
Stay safe :)
Read more...
The service lets you check all the plugins and update the outdated ones from a simple UI in two major steps:
Step 1: Click Update to update a plugin.
Step 2: Complete all recommended updates before restarting your browser.
Head on to Firefox Browser Plugin Check & Updates.
Stay safe :)
Read more...
Check Your Plugins To Keep Firefox Updated and Safe
2012-06-03T21:58:00+05:45
Cool Samar
browser|mozilla firefox|security|tricks and tips|web|
Comments
Labels:
browser,
mozilla firefox,
security,
tricks and tips,
web
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Sunday 27 May 2012
How To Supply Password With Connect Command In CS
So here is my scenario. My friend creates a counter strike server that uses the older engine and I play counter strike from 1.6. Unfortunately, the password protected server created by my friend does not appear in my LAN list. I try the connect command in console but I get the message that the password I gave was incorrect. If you guys are having similar scenarios, this post will help you out..
The trick is simple. There is another cvar called password in counter strike. First, we set the password and then use connect command.
Open console(Type ~) and then type:
password serverpass
and then,
connect IP
I hope this helps some of the gamers out there. :)
Read more...
The trick is simple. There is another cvar called password in counter strike. First, we set the password and then use connect command.
Open console(Type ~) and then type:
password serverpass
and then,
connect IP
I hope this helps some of the gamers out there. :)
Read more...
How To Supply Password With Connect Command In CS
2012-05-27T20:31:00+05:45
Cool Samar
counterstrike|tricks and tips|
Comments
Labels:
counterstrike,
tricks and tips
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Friday 4 May 2012
Decode The Dean Edwards Javascript Packer
Well today I had to unpack some javascript code from Dean Edwards packer and started to check how this tool works. I opened the official packer page and then thought of giving some inputs and analyzing outputs. But, wait!!! there's this "decode" button(in disabled state) and probably I can decode the stuff I was given.
I used the firebug and quickly removed one attribute each of the lower textarea and decode button. You'll have to remove the "readonly" attribute of the lower textarea and "disabled" attribute of the "docode" button. Now you can paste the packed code in the lower textarea and decode the packed code easily. Not the real reversing of the algorithm itself but works perfectly.
And you can beautify the unpacked script using some online beautifiers such as this.
I hope it helps some of you guys ;)
Read more...
I used the firebug and quickly removed one attribute each of the lower textarea and decode button. You'll have to remove the "readonly" attribute of the lower textarea and "disabled" attribute of the "docode" button. Now you can paste the packed code in the lower textarea and decode the packed code easily. Not the real reversing of the algorithm itself but works perfectly.
And you can beautify the unpacked script using some online beautifiers such as this.
I hope it helps some of you guys ;)
Read more...
Decode The Dean Edwards Javascript Packer
2012-05-04T22:00:00+05:45
Cool Samar
javascript|tricks and tips|useful website|
Comments
Labels:
javascript,
tricks and tips,
useful website
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Sunday 29 April 2012
Torrentz Offers Advanced Search Features[In Case You Didn't Know]
Until recently, I didn't know that my favorite torrent meta-search engine, Torrentz.eu, offered few advanced search features that makes it easier to spot the file we are searching for. After all, who would ever check the help page to read about a torrent meta-search engine but I would consider myself a noob for not thinking that advanced search are implemented in today's torrent meta-search engines.
Anyway, directly taken from the help page, below are the examples that can be used for making better search in Torrentz while searching for the files.
I've been finding these advanced searches useful since I discovered them. I hope you will also find them useful. ;)
Read more...
Anyway, directly taken from the help page, below are the examples that can be used for making better search in Torrentz while searching for the files.
Mozilla Firefox - search for Mozilla and Firefox anywhere in the title
"Mozilla Firefox" - search exactly for "Mozilla Firefox"
Mozilla | Linux - search for Mozilla or Linux
Mozilla Firefox -beta - search for Mozilla AND Firefox but NOT beta
^Mozilla - search for titles starting with Mozilla
movie* - match movie, movies or any other prefix - This is enabled by default on most queries
filename:Fedora iso - deep search inside torrent for file named Fedora iso
filename:Fedora size:3520802816 - deep search inside torrent for file named Fedora iso with size of 3520802816 bytes
Linux added: 7d - search for Linux added within the last 7 days - you can also use h for hours
"Mozilla Firefox" - search exactly for "Mozilla Firefox"
Mozilla | Linux - search for Mozilla or Linux
Mozilla Firefox -beta - search for Mozilla AND Firefox but NOT beta
^Mozilla - search for titles starting with Mozilla
movie* - match movie, movies or any other prefix - This is enabled by default on most queries
filename:Fedora iso - deep search inside torrent for file named Fedora iso
filename:Fedora size:3520802816 - deep search inside torrent for file named Fedora iso with size of 3520802816 bytes
Linux added: 7d - search for Linux added within the last 7 days - you can also use h for hours
I've been finding these advanced searches useful since I discovered them. I hope you will also find them useful. ;)
Read more...
Torrentz Offers Advanced Search Features[In Case You Didn't Know]
2012-04-29T19:53:00+05:45
Cool Samar
torrent|tricks and tips|
Comments
Labels:
torrent,
tricks and tips
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Monday 9 April 2012
Email Obfuscation Tricks In The Age Of Spammers
Every day thousands of spam emails are propelled to our e-mail addresses and the algorithms used by the spam bots are increasingly getting sophisticated and are able to harvest few kinds of obfuscated e-mail addresses already. While this race between spammers and web users goes on, we can still use several of the obfuscation tricks either to prevent bots from harvesting the emails or to fool bots to pick completely wrong e-mail adresses. Here, I am going to illustrate some useful obfuscation tricks I've come across over.
A very basic way of obfuscating emails is by replacing the characters such as @ and . with at and dot. Following are few samples:
And, below are some examples that would be nearly impossible to harvest :P. Just be more creative with them and no automated spam bot/email harvester out there will be able to get you :D. However, this might possibly create some kind of DoS like scenario for many legitimate users.
The unicode version:
samar@techgaun.com
will properly show as:
samar@techgaun.com
you can specify the following CSS property to use this obfuscation trick.
Edit: I found this link with some good examples so I thought I would rather refer you all to this webpage.
Read more...
The Very Basics
A very basic way of obfuscating emails is by replacing the characters such as @ and . with at and dot. Following are few samples:
samar[at]techgaun[dot]com
samar (at) techgaun (dot) com
samar (at) techgaun (dot) com
And, below are some examples that would be nearly impossible to harvest :P. Just be more creative with them and no automated spam bot/email harvester out there will be able to get you :D. However, this might possibly create some kind of DoS like scenario for many legitimate users.
<myfirstname> (at) techgaun (dot) com
<myfirstname> (at) <lastname> (dot) com
<myfirstname> (at) <lastname> (dot) com
Using Image
Another method is to create a small and appropriate image that will display your e-mail address. Should be more than enough, so just create a PNG/GIF of your e-mail address.Text Encodings
You could perform text encodings and javascript obfuscations, etc. An example of this is using ascii to unicode conversion and applying other level of obfuscations again to it.The unicode version:
samar@techgaun.com
will properly show as:
samar@techgaun.com
Obfuscations using CSS
Reverse Text Direction
CSS allows you to display the text in the reverse direction. For a HTML entity,<div class="email"> moc.nuaghcet@ramas</div>
you can specify the following CSS property to use this obfuscation trick.
.email
{
unicode-bidi: bidi-override;
direction: rtl;
float: left;
}
Hidden Text Within E-mail address
Another method is to put some hidden html entity between the parts of e-mail address and then set its display style as none. The spam bots while trying to extract the data from such e-mail information are subjected to get wrong information. An example is:samar@tech<span class='display: none;'>nique</span>gaun.com
Edit: I found this link with some good examples so I thought I would rather refer you all to this webpage.
Read more...
Email Obfuscation Tricks In The Age Of Spammers
2012-04-09T20:16:00+05:45
Cool Samar
email|tricks and tips|web|
Comments
Labels:
email,
tricks and tips,
web
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Sunday 8 April 2012
Turning The Internet Upside Down - A Prank To Play
Probably one of the best modern day april fool prank that should be played by the network admins to their users, I came acrosss this cool little trick to turn the whole internet upside down and thought to share with you guys.
With a linux gateway and some pretty basic linux skills(in fact, everything is well explained in the webpage & hence doesn't require much of skills), you can turn the internet upside down. The official webpage shows how to configure everything to play prank on your wi-fi stealing neighbours.
Ubuntu help also includes a good HowTo.
Read more...
With a linux gateway and some pretty basic linux skills(in fact, everything is well explained in the webpage & hence doesn't require much of skills), you can turn the internet upside down. The official webpage shows how to configure everything to play prank on your wi-fi stealing neighbours.
Ubuntu help also includes a good HowTo.
Read more...
Turning The Internet Upside Down - A Prank To Play
2012-04-08T01:03:00+05:45
Cool Samar
fun|network|tricks and tips|useful website|
Comments
Labels:
fun,
network,
tricks and tips,
useful website
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Saturday 7 April 2012
Sexy SSH Tricks For Linux Geeks
Previously I had posted on mounting filesystem over SSh and now its time for yet another post on cool SSh tricks.
So lets see few of the several SSH tricks that we either need to use or can use for fun and making stuffs easier.
Do not supply any passphrase and keep on pressing ENTER if you are looking for password-free SSH login. This will create two files id_dsa(private key) and id_dsa.pub(public key). All we have to do is copy the public key to the remote server computer and then add the content of public key to the list of authorized keys as below(or using nano or whatever you find easier):
You can even supply passphrase if you want and this will make authentication more secure. In that case, be sure to set the following value in /etc/ssh/sshd_config:
Similarly, we can encrypt the SSH sessions using one of the different available block ciphers: aes128-ctr,aes192-ctr,aes256-ctr,arcfour256,arcfour128,aes128-cbc,3des-cbc. IMHO, using aes256-ctr would be sufficiently secure due to 256 bits key size. Below is an example of using both the compression and encryption while establishing the SSH connection.
To prevent the last login status, simply change and set as following in the configuration file(/etc/ssh/sshd_config):
And also, change the content of the file /etc/motd and /var/run/motd which by default contains the banner message that is displayed by SSH.
So that's the end. Of course, there are more sexy SSH tricks which I'll cover up once I get some free time. Also, share what you have :)
Read more...
So lets see few of the several SSH tricks that we either need to use or can use for fun and making stuffs easier.
Password-less SSH
No matter how convinient it is to use SSH to connect to remote server, people tend to seek for more ease and typing passwords each time you are on interactive shell is something most users hate. Moreover, you can even prevent the bruteforcing attacks by using password-free SSH with small extra configuration change. First we need to generate a pair of keys by using the ssh-keygen tool. ssh-keygen generates, manages and converts authentication keys for ssh. ssh-keygen can create RSA keys for use by SSH protocol version 1 and DSA, ECDSA or RSA keys for use by SSH protocol version 2. In my example, I'll generate DSA keys as below:ssh-keygen -t dsa
Do not supply any passphrase and keep on pressing ENTER if you are looking for password-free SSH login. This will create two files id_dsa(private key) and id_dsa.pub(public key). All we have to do is copy the public key to the remote server computer and then add the content of public key to the list of authorized keys as below(or using nano or whatever you find easier):
cat id_dsa.pub >> ~/.ssh/authorized_keys
You can even supply passphrase if you want and this will make authentication more secure. In that case, be sure to set the following value in /etc/ssh/sshd_config:
PasswordAuthentication no
Mount Filesystem over SSH
This is another useful trick to use while working over SSH. The details on this can be read here.Copy File Over SSH Using SCP
SCP is a SSH based tool that provides an easy way to copy files over SSH. You can copy files from and to SSH server to/from your machine and also copy files from one server to another directly. Check my previous blog post on SCP for further details.Running Graphical Softwares Over SSH
With SSH, you can configure the X11 Forwarding(set to Yes in /etc/ssh/sshd_config for global effect and host-by-host basis in /etc/ssh/ssh_config by setting ForwardX11 yes) which allows us to run the graphical softwares on server over SSH. You can run the graphical softwares over SSH by supplying the -X switch while connecting to the server. An example is shown below:ssh -X samar@192.168.0.1 -p 222
Compressed and Encrypted SSH Sessions
Another good thing to do is compress and encrypt the SSH sessions. Compression is usually a very good idea for slow networks but is not desirable for faster networks where compression and de-compression might cause more overhead. The compression algorithm used by SSH is gzip and requests compression of all data (including stdin, stdout, stderr, and data for forwarded X11 and TCP connections). The default value can be set on a host-by-host basis in the configuration files(/etc/ssh/ssh_config) by setting the Compression option. To enable compression, use the -C switch while connecting to the remote SSH server or set the Compression yes in your config file.Similarly, we can encrypt the SSH sessions using one of the different available block ciphers: aes128-ctr,aes192-ctr,aes256-ctr,arcfour256,arcfour128,aes128-cbc,3des-cbc. IMHO, using aes256-ctr would be sufficiently secure due to 256 bits key size. Below is an example of using both the compression and encryption while establishing the SSH connection.
ssh -c aes256-ctr -C hostel@192.168.0.1
Disable Root Login
Its not a good thing to allow root login in SSH so be sure root login is disabled in your SSH server. This is done by setting the configuration(/etc/ssh/sshd_config) as PermitRootLogin no. What more? Disable the password-based logins and use the key-based login. And to keep script kiddies out, you could change the default port in the configuration.Disable Last Login & Default MOTD
By default, while logging in to the SSH servers like OpenSSH, we will see some kind of banner that includes a MOTD(Message Of The Day) and last login user and time. Disabling these or changing the banner requires two modifications.To prevent the last login status, simply change and set as following in the configuration file(/etc/ssh/sshd_config):
PrintMotd no
PrintLastLog no
PrintLastLog no
And also, change the content of the file /etc/motd and /var/run/motd which by default contains the banner message that is displayed by SSH.
So that's the end. Of course, there are more sexy SSH tricks which I'll cover up once I get some free time. Also, share what you have :)
Read more...
Sexy SSH Tricks For Linux Geeks
2012-04-07T22:45:00+05:45
Cool Samar
linux|ssh|tricks and tips|
Comments
Labels:
linux,
ssh,
tricks and tips
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Thursday 5 April 2012
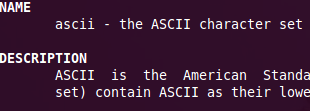
View ASCII Table In Your Linux Terminal
You need not be browsing some online ascii table website or need not download any document containing the list of ASCII characters if you are using linux OS. You can view the ASCII characters set encoded in octal, decimal, and hexadecimal by just opening the terminal.
In order to access the ASCII table, just type:
Isn't it cool to have all the ASCII character sets in your linux terminal?
Read more...
In order to access the ASCII table, just type:
samar@Techgaun:~$ man ascii
Isn't it cool to have all the ASCII character sets in your linux terminal?
Read more...
View ASCII Table In Your Linux Terminal
2012-04-05T02:35:00+05:45
Cool Samar
linux|tricks and tips|
Comments
Labels:
linux,
tricks and tips
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Monday 2 April 2012
How To Disable Password Prompts For sudo In Ubuntu
If you are one of those linux users who very frequently use the sudo command, you might have been annoyed of entering passwords each time you use this command. However with a very simple tweak, you can change this behaviour and disable the password prompts for the sudo command.
A bit of warning though, do not modify the default behavior of asking for passwords since it would drastically compromise security of your system. Following is the warning given by ubuntu help.
If you disable the sudo password for your account, you will seriously compromise the security of your computer. Anyone sitting at your unattended, logged in account will have complete Root access, and remote exploits become much easier for malicious crackers.
Now you are aware of warning, lets see how this can be done.We need to edit the /etc/sudoers file. Lets first open the file in safe editable mode using the following command:
Using visudo for editing the /etc/sudoers lets us locate the possible errors that may occur while editing the file so always use visudo.
Following is the format of disabling password prompts for specific user.
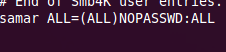
So if we are to disable password prompts for the user samar, you can make a new line with following entry:
In case you want to let all the users with admin privilege use the sudo command without having to give the password, you can edit the line that says %admin ALL=(ALL) ALL to the following:
Once you add such line for appropriate user, press Ctrl + x and save the changes. You will either have to log out and login back or restart the shell to see the modification in effect.
I hope this is useful. :)
Read more...
A bit of warning though, do not modify the default behavior of asking for passwords since it would drastically compromise security of your system. Following is the warning given by ubuntu help.
If you disable the sudo password for your account, you will seriously compromise the security of your computer. Anyone sitting at your unattended, logged in account will have complete Root access, and remote exploits become much easier for malicious crackers.
Now you are aware of warning, lets see how this can be done.We need to edit the /etc/sudoers file. Lets first open the file in safe editable mode using the following command:
samar@Techgaun:~$ sudo visudo
Using visudo for editing the /etc/sudoers lets us locate the possible errors that may occur while editing the file so always use visudo.
Following is the format of disabling password prompts for specific user.
<username> ALL=NOPASSWD: ALL
So if we are to disable password prompts for the user samar, you can make a new line with following entry:
samar ALL=(ALL)NOPASSWD: ALL
In case you want to let all the users with admin privilege use the sudo command without having to give the password, you can edit the line that says %admin ALL=(ALL) ALL to the following:
%admin ALL=(ALL)NOPASSWD: ALL
Once you add such line for appropriate user, press Ctrl + x and save the changes. You will either have to log out and login back or restart the shell to see the modification in effect.
I hope this is useful. :)
Read more...
How To Disable Password Prompts For sudo In Ubuntu
2012-04-02T23:33:00+05:45
Cool Samar
linux|tricks and tips|ubuntu|ubuntu 11.10|
Comments
Labels:
linux,
tricks and tips,
ubuntu,
ubuntu 11.10
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Friday 30 March 2012
Automating Execution Of Applications In DosBox
Running dosbox and mounting the necessary directory everytime to run any software in dosbox becomes boring with time. I had to automate the execution of qbasic by using dosbox in edubuntu and so here is the tutorial for making a simple desktop entry for automating the execution of apps in dosbox.
I will be giving an example of qbasic here but you can follow the same method, of course with little modification(that you'll easily figure out). So lets start.
The first thing we will do is make a new configuration file for our qbasic at /opt/qbasic/qbasic.conf. The file will consist of following content and you need to slightly modify according to your path and command name.
Basically what we are doing above is adding our commands in the autoexec section of configuration file that will be read by dosbox. In the autoexec section, we first mount our appropriate directory(~/qbasic as C) and then switch to the mount point and finally execute the required command(qb in above example).
Now all you need to do is create a new launcher with the following command:
Notice that I'm providing my custom configuration while running the dosbox command. As per your necessity, you could provide -noconsole and -exit switches in the command above(as in games). Also, though this article focusses on linux, you can follow this with minor OS specific variations to run in windows as well. I hope this helps you. :)
Read more...
I will be giving an example of qbasic here but you can follow the same method, of course with little modification(that you'll easily figure out). So lets start.
The first thing we will do is make a new configuration file for our qbasic at /opt/qbasic/qbasic.conf. The file will consist of following content and you need to slightly modify according to your path and command name.
[autoexec]
mount C ~/qbasic
C:
qb
mount C ~/qbasic
C:
qb
Basically what we are doing above is adding our commands in the autoexec section of configuration file that will be read by dosbox. In the autoexec section, we first mount our appropriate directory(~/qbasic as C) and then switch to the mount point and finally execute the required command(qb in above example).
Now all you need to do is create a new launcher with the following command:
/usr/bin/dosbox -conf /opt/qbasic/qbasic.conf
Notice that I'm providing my custom configuration while running the dosbox command. As per your necessity, you could provide -noconsole and -exit switches in the command above(as in games). Also, though this article focusses on linux, you can follow this with minor OS specific variations to run in windows as well. I hope this helps you. :)
Read more...
Automating Execution Of Applications In DosBox
2012-03-30T22:54:00+05:45
Cool Samar
dosbox|tricks and tips|
Comments
Labels:
dosbox,
tricks and tips
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Wednesday 28 March 2012
How To Fix NTFS Disk Partition From Linux
If you have problematic NTFS partition in your hard disk, you can fix many of the common NTFS inconsistencies from linux. Linux consists of a set of tools that allow you to manipulate and perform different types of actions on the NTFS partitions. This package is known as ntfsprogs.
If your linux distribution does not consist of the ntfsprogs package, you can install it by using the package manager tool that comes in your distribution or from command line. Debian and ubuntu users can type the following command:
Now to fix the NTFS drive, we must first determine the partition we want to fix. We can use the simplest one, the fdisk utility to determine the partition of hard disk we want to fix. Type the following command to view the list of partitions:
If you have more than one HDDs and want to view partitions of specific HDD, you can always do so by issuing the commands such as sudo fdisk -l /dev/sda or sudo fdisk -l /dev/sdb and so on.
Now lets suppose its /dev/sdb5 we need to fix. We can now use the ntfsfix command that comes in the ntfsprogs package.
Note that it only repairs some fundamental NTFS inconsistencies, resets the NTFS journal file and schedules an NTFS consistency check for the first boot into Windows. You may run ntfsfix on an NTFS volume if you think it was damaged by Windows or some other way and it cannot be mounted.
Read more...
If your linux distribution does not consist of the ntfsprogs package, you can install it by using the package manager tool that comes in your distribution or from command line. Debian and ubuntu users can type the following command:
sudo apt-get install ntfsprogs
Now to fix the NTFS drive, we must first determine the partition we want to fix. We can use the simplest one, the fdisk utility to determine the partition of hard disk we want to fix. Type the following command to view the list of partitions:
sudo fdisk -l
If you have more than one HDDs and want to view partitions of specific HDD, you can always do so by issuing the commands such as sudo fdisk -l /dev/sda or sudo fdisk -l /dev/sdb and so on.
Now lets suppose its /dev/sdb5 we need to fix. We can now use the ntfsfix command that comes in the ntfsprogs package.
sudo ntfsprogs /dev/sdb5
Note that it only repairs some fundamental NTFS inconsistencies, resets the NTFS journal file and schedules an NTFS consistency check for the first boot into Windows. You may run ntfsfix on an NTFS volume if you think it was damaged by Windows or some other way and it cannot be mounted.
Read more...
How To Fix NTFS Disk Partition From Linux
2012-03-28T20:53:00+05:45
Cool Samar
linux|tricks and tips|ubuntu|ubuntu 11.10|windows|
Comments
Labels:
linux,
tricks and tips,
ubuntu,
ubuntu 11.10,
windows
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Friday 23 March 2012
How To Copy Text To Clipboard From Command Prompt
I had earlier posted about alternate data streams and the post consisted of texts copied from command line. I was on local IRC channel, one guy was curious if I was using the redirection operator to get the content from the command prompt. So I thought to share this simple tip to copy text from command prompt in windows.
Follow the steps as below:
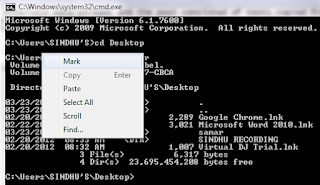
1) Right click anywhere on the command prompt window and then select the Mark option.
2) Now start selecting the text you need to copy using your mouse. You could keep on holding mouse and then do the selection. Alternatively, you could click on the starting point and then while holding the SHIFT key, click on the end of text you wish to copy.
3) After selecting the required text, just press Enter. Alternatively, you can right click on the top title bar of command prompt and then go to Edit -> Copy.
If you are looking for copy pasting methods in linux terminals, you can read my article. I hope this helps some of you guys. :)
Read more...
Read more...
How To Copy Text To Clipboard From Command Prompt
2012-03-23T20:04:00+05:45
Cool Samar
command prompt|tricks and tips|windows|
Comments
Labels:
command prompt,
tricks and tips,
windows
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Tuesday 20 March 2012
Some Fun With Alternate Data Streams
I have not been blogging for a while because of exams but now I'm free for few days so here comes another post back from my home village. This time, I'm going to share some basic funs with alternate data streams from theory to some practical stuffs.
What is Alternate Data Stream Alternate Data Stream(ADS) is a kind of file system fork which allows more than one data stream to be associated with a single filename. Alternate Data Stream was introduced by Microsoft as a part of its NTFS file system. Alternate Data Streams are not shown by Windows Explorer and even the dir command and size of ADS is also excluded from the file size. The dir command however allows us to view the alternate data streams using the dir /R command in Windows Vista and above.
One use of ADS could be hiding the information as alternate data streams in the file but beware that copying the file to non-NTFS file systems will make you loose the information in the ADS. ADS was originally introduced to store file information and properties however any user can hide any kind of information in the ADS. Some malwares have utilized the ADS to hide their code so most antiviruses today also scan the ADS of any file to find anything fishy.
Note that the format used to create(and access) ADS is filename:ADSname. A relatively simple guide I had written a while ago is HERE.
Now lets move on to some interesting stuffs and for that, I am creating a directory named "samar" in Desktop. We will first create a simple text file by using the command below:
Now lets add an alternate data stream by issuing the following command:
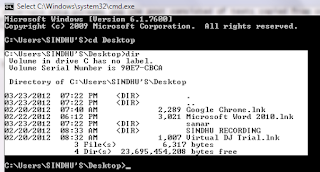
Lets issue the dir command to see what it lists:
We can see no information regarding the alternate data stream we just added to the file and lets see if the type command shows anything by just opening the file.
So where is the private stuff we've put as ADS in the file? Even viewing the file from windows explorer does not show the content in ADS and of course the size is also not included. The point here is the malicious user might add something bad in the alternate data stream and send to a normal PC user. The unsuspecting user will not know if there's anything other than just the text file. Now lets see how we can see the alternate data stream.
For a while, lets pretend that we don't know that the ADS is added in the file. So first we will use the commands to see if there's any ADS in the file. The simplest one is to use dir /R command as below:
We can see that besides the ads.txt file, there is another entry ads.txt:private:$DATA. By examining this file, we come to know that the alternate data stream with the name private is present in the file ads.txt and the alternate data stream is nothing but just the data. However, as stated earlier, only Vista and above contain the dir command that lets us list the alternate data streams. In such case, you can download a small utility named streams from Microsoft Technet. The streams tool also allows us to delete the ADS easily which is possible but a bit obscure for normal PC user. Now to view the content of the alternate data stream, we will use notepad:
Note that this time we didn't use type command since it does not support the use of colon in the command. We used the notepad but we could also use another command known as more as below:
The fun with ADS just does not stop here. We could do much more than this but the basic idea is same. We can embed executables and codes within the ADS and run those executable whenever necessary. I'll leave this as homework for you guys since it won't be hard to figure it out once you've understood the basics I've discussed above.
The alternate data stream has already been exploited in IIS, the primary web server from Microsoft. Following is the example I've taken from OWASP on how it could be exploited in IIS.
Normal access:
http://www.alternate-data-streams.com/default.asp Show code bypass accessing the :$DATA alternate data stream:
http://www.alternate-data-streams.com/default.asp::$DATA
Last thing I would like to discuss is how to delete the alternate data streams. The streamers tool provides a -d switch to delete the ADS and it also supports the wildcards for deleting the streams. Another way of deleting the alternate streams is to copy the file in non-NTFS drives such as to FAT32-formatted pendrives and then copying back. Of course, you could also save the content of main stream in another file and then delete the original file that consists of stream.
I hope this helps you. Please let me know if I should add something to it. :)
Read more...
What is Alternate Data Stream Alternate Data Stream(ADS) is a kind of file system fork which allows more than one data stream to be associated with a single filename. Alternate Data Stream was introduced by Microsoft as a part of its NTFS file system. Alternate Data Streams are not shown by Windows Explorer and even the dir command and size of ADS is also excluded from the file size. The dir command however allows us to view the alternate data streams using the dir /R command in Windows Vista and above.
One use of ADS could be hiding the information as alternate data streams in the file but beware that copying the file to non-NTFS file systems will make you loose the information in the ADS. ADS was originally introduced to store file information and properties however any user can hide any kind of information in the ADS. Some malwares have utilized the ADS to hide their code so most antiviruses today also scan the ADS of any file to find anything fishy.
Note that the format used to create(and access) ADS is filename:ADSname. A relatively simple guide I had written a while ago is HERE.
Now lets move on to some interesting stuffs and for that, I am creating a directory named "samar" in Desktop. We will first create a simple text file by using the command below:
echo An ordinary text file > ads.txt
Now lets add an alternate data stream by issuing the following command:
echo I am secret > ads.txt:private.txt
Lets issue the dir command to see what it lists:
Volume in drive C has no label.
Volume Serial Number is 90E7-CBCA
Directory of C:\Users\SINDHUS\Desktop\samar
03/20/2012 09:58 AM <DIR> .
03/20/2012 09:58 AM <DIR> ..
03/20/2012 09:56 AM 24 ads.txt
3 File(s) 24 bytes
3 Dir(s) 22,683,332,608 bytes free
We can see no information regarding the alternate data stream we just added to the file and lets see if the type command shows anything by just opening the file.
C:\Users\SINDHUS\Desktop\samar>type ads.txt
An ordinary text file
An ordinary text file
So where is the private stuff we've put as ADS in the file? Even viewing the file from windows explorer does not show the content in ADS and of course the size is also not included. The point here is the malicious user might add something bad in the alternate data stream and send to a normal PC user. The unsuspecting user will not know if there's anything other than just the text file. Now lets see how we can see the alternate data stream.
For a while, lets pretend that we don't know that the ADS is added in the file. So first we will use the commands to see if there's any ADS in the file. The simplest one is to use dir /R command as below:
C:\Users\SINDHU'S\Desktop\samar>dir /R
Volume in drive C has no label.
Volume Serial Number is 90E7-CBCA
Directory of C:\Users\SINDHU'S\Desktop\samar
03/20/2012 09:58 AM <DIR> .
03/20/2012 09:58 AM <DIR> ..
03/20/2012 09:56 AM 24 ads.txt
14 ads.txt:private.txt:$DATA
03/20/2012 09:58 AM 496 info.txt
2 File(s) 520 bytes
3 Dir(s) 22,881,669,120 bytes free
We can see that besides the ads.txt file, there is another entry ads.txt:private:$DATA. By examining this file, we come to know that the alternate data stream with the name private is present in the file ads.txt and the alternate data stream is nothing but just the data. However, as stated earlier, only Vista and above contain the dir command that lets us list the alternate data streams. In such case, you can download a small utility named streams from Microsoft Technet. The streams tool also allows us to delete the ADS easily which is possible but a bit obscure for normal PC user. Now to view the content of the alternate data stream, we will use notepad:
C:\Users\SINDHUS\Desktop\samar>notepad ads.txt:private.txt
Note that this time we didn't use type command since it does not support the use of colon in the command. We used the notepad but we could also use another command known as more as below:
C:\Users\SINDHU'S\Desktop\samar>more < ads.txt:private
I am secret
I am secret
The fun with ADS just does not stop here. We could do much more than this but the basic idea is same. We can embed executables and codes within the ADS and run those executable whenever necessary. I'll leave this as homework for you guys since it won't be hard to figure it out once you've understood the basics I've discussed above.
The alternate data stream has already been exploited in IIS, the primary web server from Microsoft. Following is the example I've taken from OWASP on how it could be exploited in IIS.
Normal access:
http://www.alternate-data-streams.com/default.asp Show code bypass accessing the :$DATA alternate data stream:
http://www.alternate-data-streams.com/default.asp::$DATA
Last thing I would like to discuss is how to delete the alternate data streams. The streamers tool provides a -d switch to delete the ADS and it also supports the wildcards for deleting the streams. Another way of deleting the alternate streams is to copy the file in non-NTFS drives such as to FAT32-formatted pendrives and then copying back. Of course, you could also save the content of main stream in another file and then delete the original file that consists of stream.
I hope this helps you. Please let me know if I should add something to it. :)
Read more...
Some Fun With Alternate Data Streams
2012-03-20T19:08:00+05:45
Cool Samar
alternate data stream|hacking|security|tricks and tips|windows|
Comments
Labels:
alternate data stream,
hacking,
security,
tricks and tips,
windows
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Sunday 11 March 2012
Finding Prime Factors Of A Number From Linux Terminal
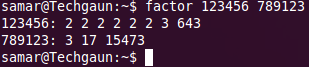
Linux is awesome because of its powerful commanline interface from where you can do any tasks of varied complexities. I've been posting different command line tricks for system administrations & stuffs like that. But this time I am posting a little command line trick to find the prime factors of any number.
Linux provides a command factor that lets you find the prime factors of any number. So if you are into mathematics and working on prime factorizations, why worry? Just open the terminal and use the factor command.
This command takes any number of integer values as the argument and prints the prime factor of each of them. If no number is specified, it takes the value from standard input.
More information on factor command: The factor command makes use of the Pollard Rho algorithm which is suitable for numbers with relatively small factors. It is not quite good for computing factors of large numbers whose factors are not small values.
Read more...
Linux provides a command factor that lets you find the prime factors of any number. So if you are into mathematics and working on prime factorizations, why worry? Just open the terminal and use the factor command.
This command takes any number of integer values as the argument and prints the prime factor of each of them. If no number is specified, it takes the value from standard input.
samar@Techgaun:~$ factor 2056 1234567
More information on factor command: The factor command makes use of the Pollard Rho algorithm which is suitable for numbers with relatively small factors. It is not quite good for computing factors of large numbers whose factors are not small values.
Read more...
Finding Prime Factors Of A Number From Linux Terminal
2012-03-11T17:30:00+05:45
Cool Samar
command line|command prompt|linux|mathematics|tricks and tips|
Comments
Labels:
command line,
command prompt,
linux,
mathematics,
tricks and tips
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Friday 9 March 2012
Being Away and Back In All IRC Chans At Once [XChat Tip]
Hi everybody, one friend of mine asked me today if he could mark himself as away at once in all the open servers and he was using the XChat IRC client in mint and I quickly remembered the allserv and allchanl commands. So here I am sharing the quick tip on how you can mark yourself away in all the open IRC channels at once in XChat IRC client.
XChat provides two commands allserv and allchanl that can be used to run any specified command for all the open IRC servers and IRC channels of currently selected server respectively. The syntax is very simple as below:
The first command i.e. allserv allows to run any IRC command in all servers you have open currently. So if you want to mark yourself away, all you have to use is away command in conjunction with allserv command(fyi, away syntax is /away Reason for being away), type the command as below:
Once you come back and do not need to be marked as away in all servers, enter the command as below:
The above allserv example is for marking you as away for all the servers. What if you want to mark yourself as away in all the channels of currently selected server? Don't worry, xchat offers allchanl for this very purpose. See the examples below using this command.
Set yourself away:
Set yourself no longer away:
I hope these information help you. :)
Read more...
XChat provides two commands allserv and allchanl that can be used to run any specified command for all the open IRC servers and IRC channels of currently selected server respectively. The syntax is very simple as below:
/allserv <cmd>
The first command i.e. allserv allows to run any IRC command in all servers you have open currently. So if you want to mark yourself away, all you have to use is away command in conjunction with allserv command(fyi, away syntax is /away Reason for being away), type the command as below:
/allserv away Brb Breakfast time
Once you come back and do not need to be marked as away in all servers, enter the command as below:
/allserv back
The above allserv example is for marking you as away for all the servers. What if you want to mark yourself as away in all the channels of currently selected server? Don't worry, xchat offers allchanl for this very purpose. See the examples below using this command.
Set yourself away:
/allchanl away Brb Breakfast time
Set yourself no longer away:
/allchanl back
I hope these information help you. :)
Read more...
Being Away and Back In All IRC Chans At Once [XChat Tip]
2012-03-09T19:42:00+05:45
Cool Samar
irc|tricks and tips|xchat|
Comments
Labels:
irc,
tricks and tips,
xchat
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Subscribe to:
Posts (Atom)